
Beginning on September 24th, Bitcoin collapsed for a full week and prices continued to fluctuate around $8,000. Bitcoin buyers have now received warnings that their cryptocurrency investments face another threat. Uniper Threat Labs security researchers say the spyware provided by the Trojan uses the encrypted Telegram messaging platform to reveal cryptocurrency data. Read the rest of this post »
Published by on October 8, 2019 2:39 am and last modified on October 8, 2019 2:39 am.
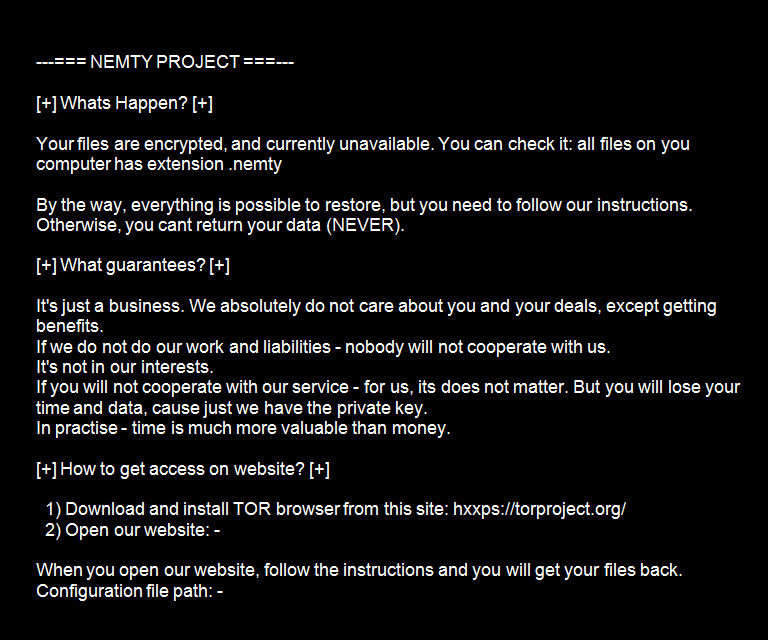
At the end of August, Nemty Ransomware was actively, spreading via compromised RDP connections. The ransomware virus has been traded through the dark network, and the ransomware mode of “blocking the road, robbing and sitting on the ground” has forced the user to accumulate wealth.
Now, 1.5 version of the Nemty ransomware virus has hit again, raging the network. Read the rest of this post »
Published by on October 5, 2019 11:27 am and last modified on September 30, 2019 11:56 am.

Since the Astaroth fileless attack was released in July this year, Microsoft has once again revealed a new wave of Nodersok file-free attacks recently. The hackers also use legitimate tools to launch attacks in order to convert infected systems into proxies and perform click-fraud. It is estimated that thousands of Windows computers have been wrapped up.
Nodersok attacks do not infect any files on the device, and do not leave traces on the hard disk. It is only a series of infections are launched through legitimate tools.
The Nodersok attack begins with the user downloading and executing an HTML program (HTA) by clicking or browsing a malicious advertisement, while the JavaScript code hidden in the HTA file downloads another JavaScript file from the C&C server. Next, it downloads an encrypted MP4 file that contains the PowerShell command. After decrypting, it uses the PowerShell command to download the module and other modules that can disable Windows Defender Antivirus. The last thing left is to turn the victim computer into a proxy and JavaScript module based on the Node.JS framework.
Microsoft said that Nodersok, like Astaroth, performs every step of the infection chain only on legitimate tools, whether it’s the built-in mshta.exe and powershell.exe, or node.exe and Windivert.dll/sys downloaded from a third-party website. The functionalities that come with these scripts or Shellcodes appear encrypted form. They then are decrypted, and executed only in memory. No malicious code is written to the hard disk.
If you remove the legitimate tools that Nodersok uses, the left malicious files are the original HTA file, the final JavaScript module, and a large number of encrypted files.
Microsoft discovered the Nodersok attack in mid-July this year and launched an investigation because it detected an abnormality in the use of mshta.exe. Now Nodersok’s main goal is to target the average consumer in the US and Europe.
Published by on October 2, 2019 7:08 am and last modified on September 30, 2019 8:08 am.
Hi. I need your help to uninstall Adobe Acrobat Reader DC. Few months ago, I downloaded it to convert and edit pdf file. Now I try to uninstall it and use other software. However, it won’t go away. When I click on the uninstall button, the icon comes up with “preparing to remove” but just stays there for up to hours. In the end, it just crashes. Another time I try to uninstall it, the AcroRd32.exe Application Error pops up. Have you guys ever seen this error? How do you uninstall the software in the end? I need your suggestion to remove Adobe Acrobat Reader DC. Thanks. Read the rest of this post »
Published by on September 30, 2019 3:30 am and last modified on December 19, 2019 2:20 am.
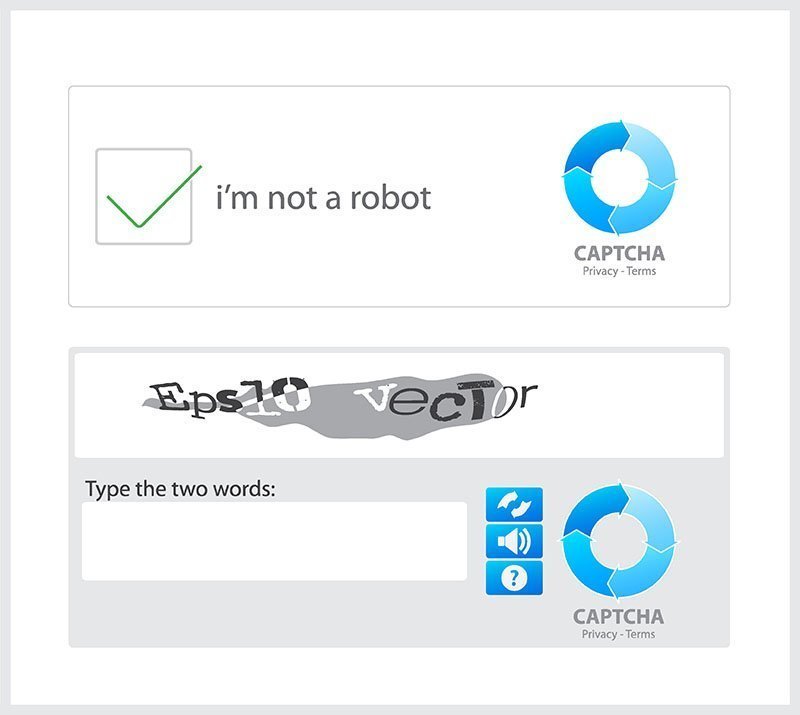
The Captcha verification code mechanism (a method for identifying real humans or network robots by identifying the letters in the picture) is familiar for most Internet users. However, this mechanism is no longer safe. Security researchers have found that hackers are using it to take victims to phishing pages. According to researchers, the phishing campaign uses captcha boxes to hide a fake Microsoft account login page from secure email gateways (SEGs) into order to trick victims into providing sensitive information. Read the rest of this post »
Published by on September 27, 2019 2:29 am
Are you looking for a reliable password manager? Can’t decide which one to choose? Is 1Password any good? Is 1Password safe? Our experts have tested all the popular password managers and recorded features and other information. To help you make an informed decision, we sorted the information and wrote reviews about the password managers. Many users ask if 1Password is worth to invest. If you are one of them, learn about the product in this 1Password review to get your answer. Read the rest of this post »
Published by YooCare Editor on September 26, 2019 9:07 am and last modified on May 27, 2024 10:39 am.
Hello. I need your help you to uninstall Skype from my PC. It’s strange, but I can’t remove it via the Windows add/remove feature. I successfully uninstalled Facebook and reinstalled it. Why can’t I uninstall Skype this time? What did I miss? I tried to click uninstall button, but nothing happened. Is there anyone who can help me delete Skype off my Windows 10? Read the rest of this post »
Published by on September 24, 2019 3:03 am and last modified on December 19, 2019 2:07 am.

Security vendor UpGuard announced a data breach this week, saying its researchers found 1.7TB of data on a public rsync server, and the data content revolves around Russia’s network monitoring system SORM. Read the rest of this post »
Published by on September 23, 2019 2:19 am
On September 18, Symantec, a network security company, said that since July 2018, the gang of Tortoiseshell hackers has attacked at least 11 organizations, most of which are located in Saudi Arabia. The hacker group mainly targets Saudi IT vendors and collects data including IP addresses, the operating system version, computer name, and network connections on its network. Researchers say they don’t have enough information to attribute this behavior to a known organization or government. However, CrowdStrike’s vice president of intelligence said that the hackers described by Symantec seem to be supporting the Islamic Revolutionary Guard Corps. Read the rest of this post »
Published by on September 20, 2019 2:21 am

On September 16, ZDNet reported that more than 24.38 million Lumin PDF users were disclosed on the Hacking Forum. Lumin PDF is a little-known cloud-based service that allows users to view, edit, and share PDF files through web-based dashboards, browser extensions, or corporate mobile applications. Read the rest of this post »
Published by on September 18, 2019 8:29 am and last modified on September 18, 2019 8:30 am.


