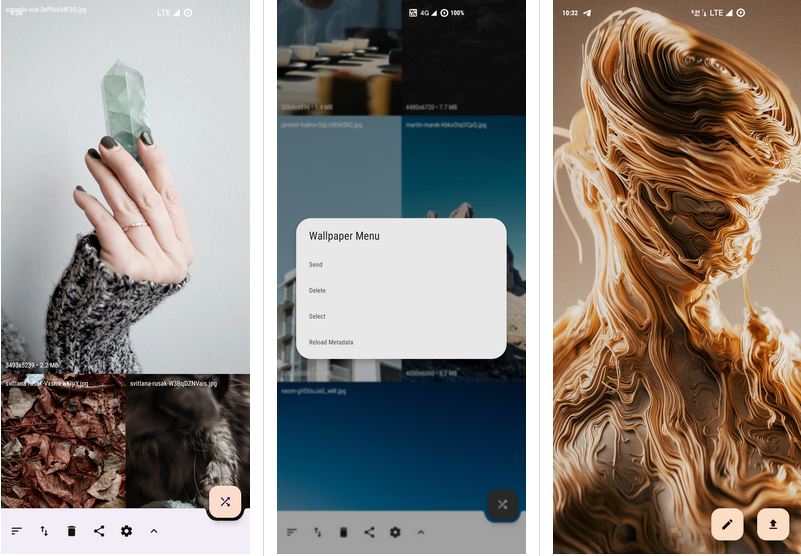
Peristyle: Build Your Local Wallpaper Library
Is there anyone like me, who has a million online wallpaper apps in his phone, but still prefers to use locally saved wallpapers? But with so many files, it’s not only not so convenient to use, but also makes the album app become bloated and complicated. Why can’t we treat these local wallpapers as a wallpaper app, and Peristyle is one such tool you can use to effectively organize these wallpapers in one place!
Published by YooCare Editor on May 28, 2024 2:11 am and last modified on May 28, 2024 2:16 am.
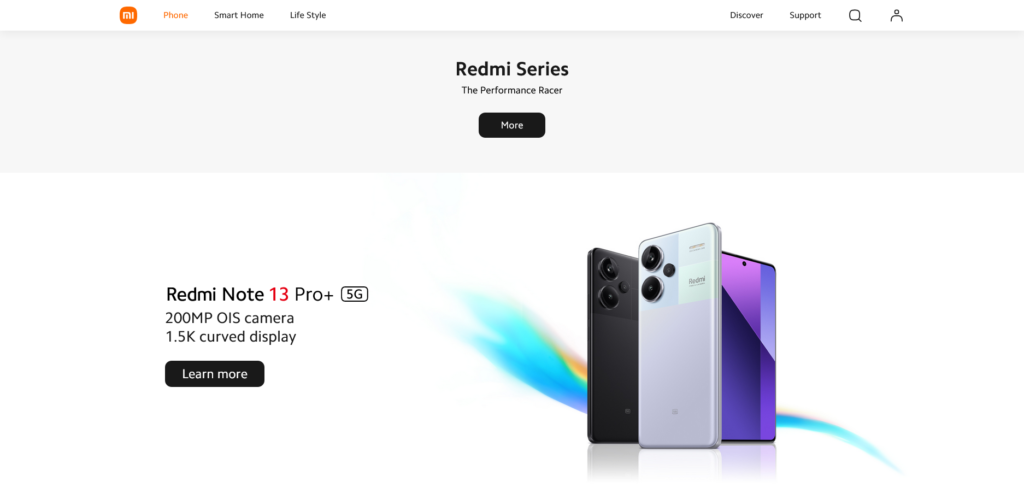
Redmi Held a New Product Conference
On April 10th, the Redmi brand (Redmi) held a new product launch event, introducing several new products including the Redmi Turbo 3 smartphone, the Redmi Pad Pro tablet, the Mi Home Pro 1.5 horsepower fresh air conditioner, the Redmi MAX 100-inch 2025 model TV, and the Xiaomi TV S, among others.
Read the rest of this post »
Published by YooCare Editor on April 11, 2024 1:09 am
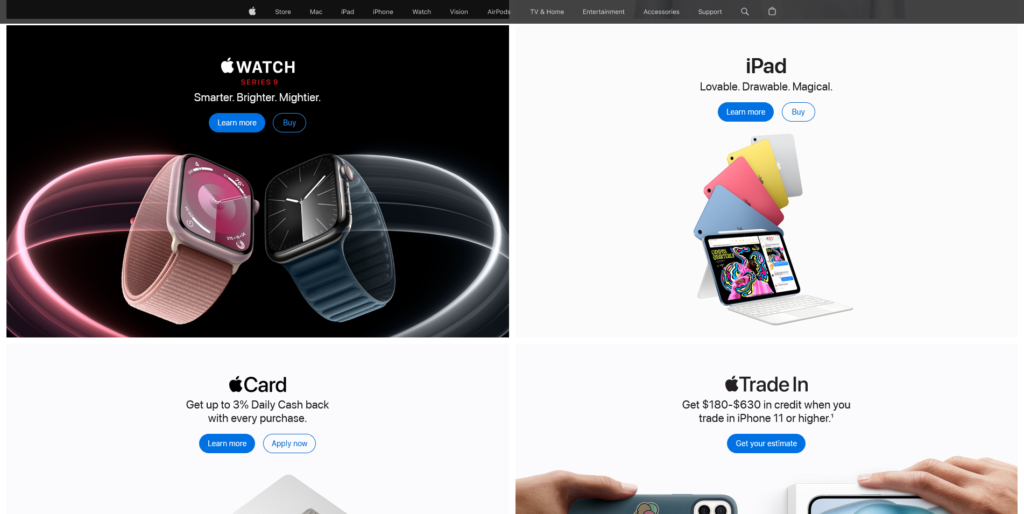
Apple Jing’an is the eighth Apple Retail Store in Shanghai, the 57th in Greater China, and one of the most highly anticipated. It’s been seven years since the store was closed for renovation in 2017, and on March 21st, Apple Jing’an will finally be opened.
Read the rest of this post »
Published by YooCare Editor on March 23, 2024 2:04 am and last modified on April 11, 2024 3:05 am.
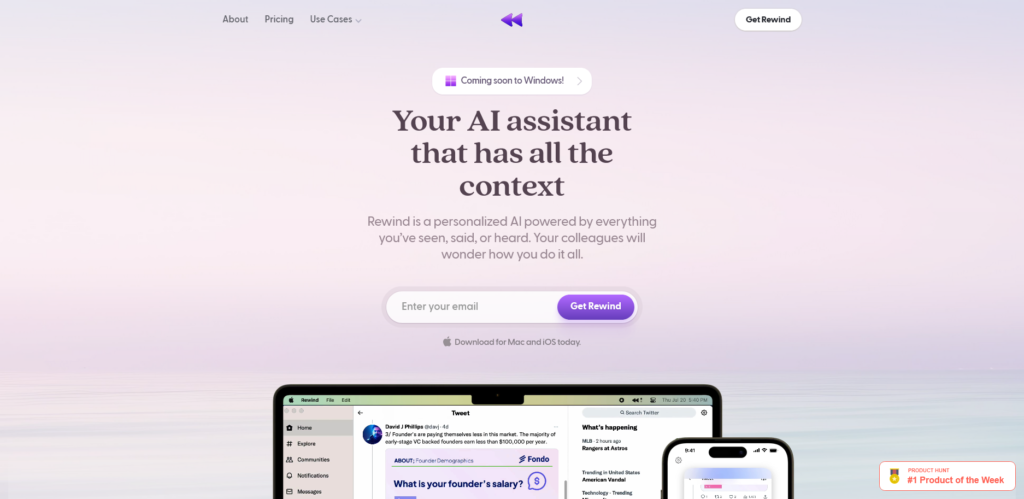
Rewind: Music Time Machine
Platform: iOS and Android
Keywords: music, player
Teachers often say “you’re the worst class I’ve ever brought up”, audiences often say “the aesthetics of the entertainment has been seriously downgraded”, and music lovers often say “the music scene has regressed by twenty years”, in that case, try to turn on Rewind, and let it bring you back to the era of your favorite music through time and space, Rewind spans over 50 years, and allows you to go back to the 60’s, the era when psychedelia was flourishing, the late 70’s when punk and disco were popular, or the wave of electronic music at the beginning of the millennium. Rewind spans 50 years, so you can go back to the ’60s when psychedelia was booming, the late ’70s when punk and disco were big.
Read the rest of this post »
Published by YooCare Editor on January 16, 2024 7:53 am and last modified on April 10, 2024 10:14 am.
Superlist
Platform: iOS, iPadOS, macOS, Web and Android
Keywords: task management, team collaboration, task management
If you’ve been using To Do List service for a long time, you must have heard of Wonderlist – the simple inbox design and intuitive task creation mode can be considered as the best choice for users who are new to task management to get started. And To Do List covers almost all popular platforms and brings a consistent experience on all platforms as much as possible. Only with the eventual acquisition of Wonder List by Microsoft, this easy to use, simple logic and cross-platform task management tool has become Microsoft To Do, although it still maintains the excellent features such as easy to use cross-platform, but neither the functionality nor innovation can not be compared with the Wonderlist. Perhaps it is also to see Microsoft’s “inaction” and lack of innovation after the completion of the acquisition of the list of marvelous, the original author of the list of marvelous decided to start a second business – still to do a To Do List product, the name is also very domineering: Superlist. Since it’s just released, Superlist is only available for Mac, iOS, Android, and Web – there is no Windows client, but that doesn’t affect the big picture, after all, through PWAs, you can use the browser on Windows to realize After all, with PWAs, it’s possible to have a browser-based experience on Windows that’s just as good as the client’s.
Read the rest of this post »
Published by YooCare Editor on January 6, 2024 4:34 am and last modified on April 10, 2024 7:57 am.

Sleeve 2: Custom desktop music widgets
Platform: macOS
Keywords: music, widget
Sleeve is a desktop music widget for macOS. Unlike the native “Now Playing” widget that you need to click from the menu bar, Sleeve’s widget can reside on the desktop and the dock bar, which is not only convenient for you to get the information of the currently playing music, but also allows you to control it with interactive buttons and shortcuts.
Read the rest of this post »
Published by YooCare Editor on January 6, 2024 2:12 am and last modified on April 11, 2024 3:05 am.
BetterCounter: Simple and Reliable Counter
Platform: Android
Keywords: counter
The convenience store downstairs of my house has come up with a preferential strategy of buy 6 get 1 free and buy 10 get 2 free in order to better develop the coffee business and increase the sales of coffee. In order to solve the problem of people consuming more than one time, they allow customers to save cups and record them with the help of the cell phone’s tail number plus a tablet memo, searching for and inputting the number of cups whenever the customer buys a new one and deleting the old ones when the customer consumes the coffee and manually Update to existing cups.
Read the rest of this post »
Published by YooCare Editor on January 4, 2024 12:35 pm and last modified on April 10, 2024 12:42 pm.
IYPS: Are your hand rubbed passwords actually safe?
Platform: Android
Keywords: password management, password security
Read the rest of this post »
Published by YooCare Editor on January 2, 2024 2:52 am and last modified on April 11, 2024 3:14 am.
ReLens: The Professional iPhoneography App with a More Lifestyle Approach
Platform: iOS/iPadOS/Android
Keywords: mobile photography, retouching
Read the rest of this post »
Published by YooCare Editor on January 1, 2024 2:52 am and last modified on April 11, 2024 3:06 am.
Welcome to this edition of AppWatch. We will regularly post latest apps and updates on this new column.
Read the rest of this post »
Published by YooCare Editor on February 16, 2023 4:01 am and last modified on April 10, 2024 7:51 am.


