Do you have a popup saying it is Win 8 Protection 2014 in the computer? What does this strange program do in your compute? How to uninstall it because you never approve its installation? How can it get in the computer? Is it really from Microsoft? How do we verify that?
Win 8 Protection 2014 is classified as a rogue antivirus program which masquerades as a legitimate one and attempts to defraud innocent computer users of as much money as possible. This newly released computer virus should be concerned by the ordinary computer users around the world for it looks no difference from those famous legitimate antivirus programs on the surface. Computer hackers aim at tricking computer users through convincing them that the rogue program is useful. This hateful thing is created by computer hackers with the purpose of accumulating wealth unfairly. In order to avoid being swindled, we should be cautious if we see any unknown programs on the computer.
Win 8 Protection 2014 shows up immediately after it is installed on the computer successfully. No matter what you do, the rogue program will pop up out of nowhere when the time is right and start scanning your computer without permission. In order to let you pay for its “registered version”, it will tell you that there are many problems in the computer according to the scan results and display security alerts continuously. Don’t trust the detected infections showing on the scan result because they are all fake. They do not exist in your computer. The scam program claims that these infections cannot be handled by other antivirus applications and it can help. If you want to clean up the computer, you need to pay to register / activate the full version at first. However, this full version does not exist. Once you pay, you will not receive any registration procedures since it is not to provide protection services for your computer in the future. Once Win 8 Protection 2014 cheats you out of money the successfully, it will let you face all the chaos alone for it still takes over your computer completely. Therefore, the rogue antivirus program should be removed as soon as possible once you realize that it is in your computer.
Basically, victims of this computer rogue scam virus will see and experience:
1) constant popups of the fake antivirus screen;
2) lots of security alerts reporting viruses in almost all files and programs;
3) constant blocks from the pop-up virus screen;
4) a rather slow computer.
Win 8 Protection 2014 virus can install itself in the computer without permission from the computer user. It also can prevent computer user from accessing to other programs in the infected computer. You will realize that you cannot open anything on the computer because it will continue to pop up alerts to block you. Sometimes the Internet connection may get disconnected by the virus. More importantly, the system will be frozen frequently or get blue screen of death. If you pay for this fake antivirus program, you use credit card information may be exposed and collected by computer hackers remotely. This scam virus can be as dangerous as it can be. So we should get rid of it completely as early as possible.
1. Restart the Infected Computer into Safe Mode with Networking
(* Usually the malware will be temporarily disabled in Safe Mode which will provide users a chance to get this problem fixed. If you are still getting the virus popup in safe mode with networking, please try safe mode with command prompt instead.)
For Windows 8
(1). Sign out to get the log-in screen
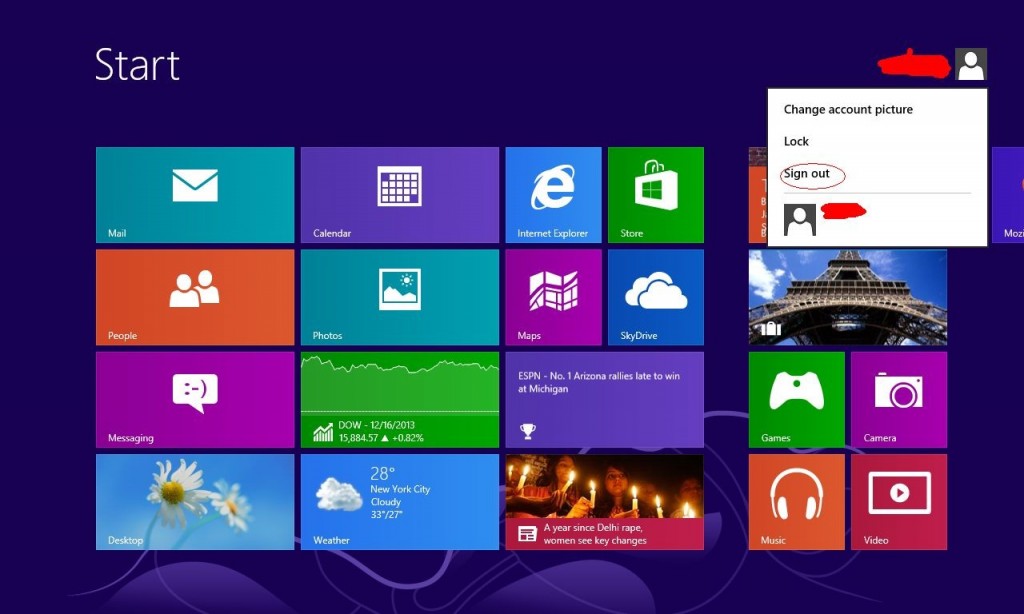
(2). Keep holding down Shift key then click on the Shut Down icon to select Restart

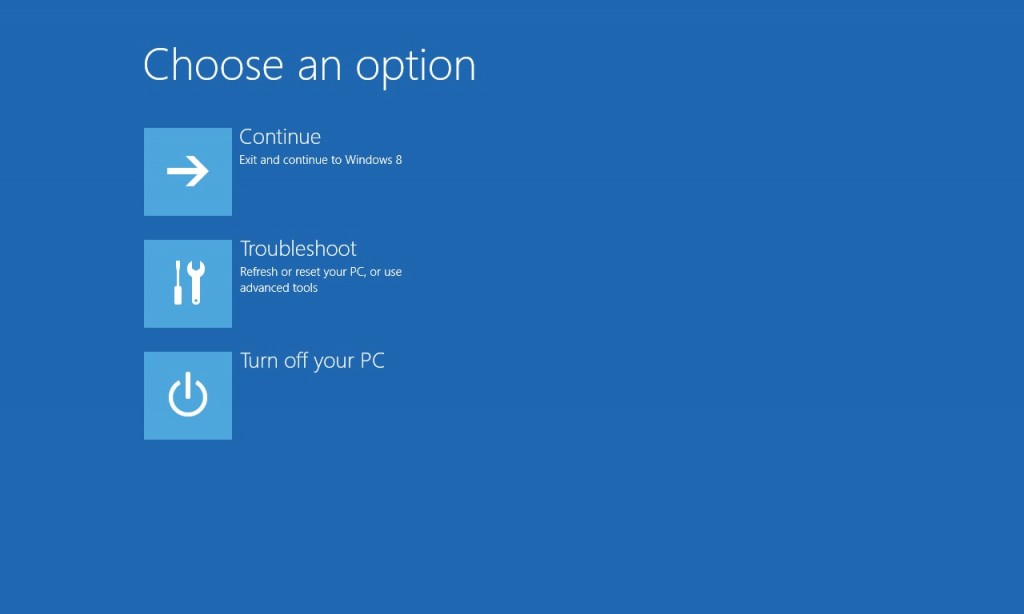
(3). If you do it right, you will see ‘Choose An Option’ screen. Choose ‘troubleshoot’
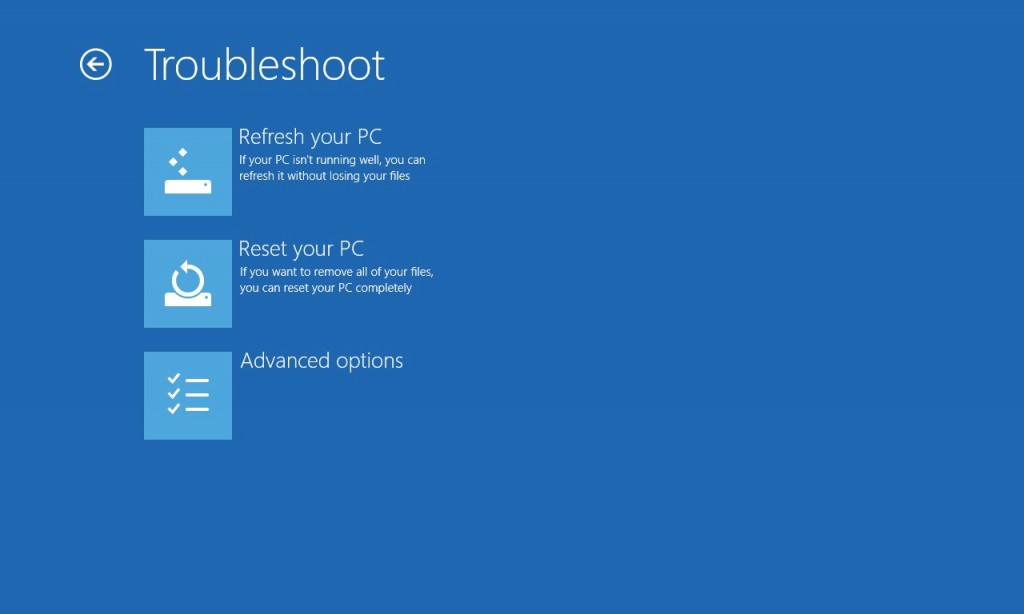
(4). Click on ‘Advance Options’
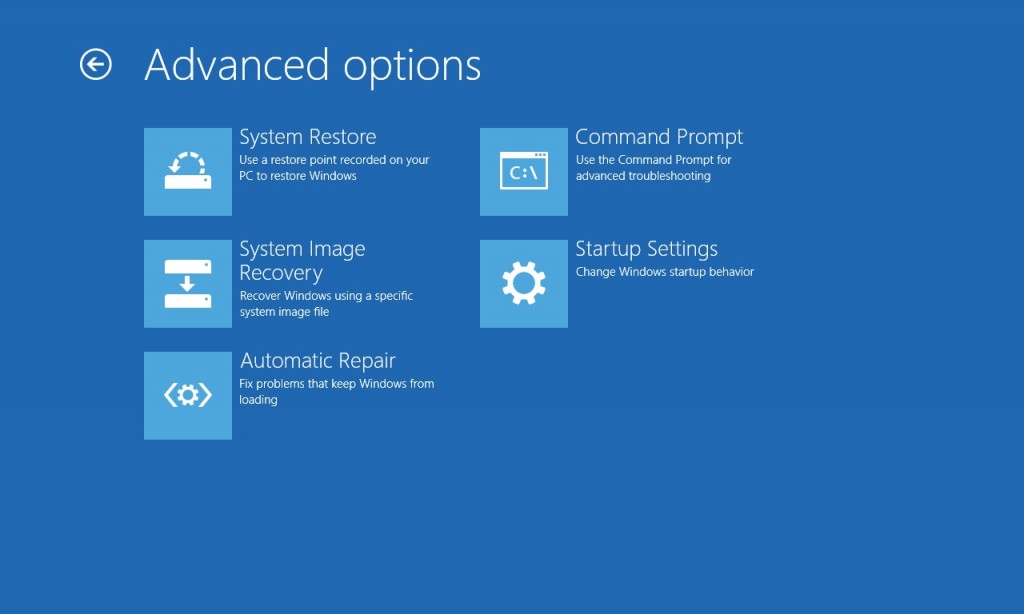
(5). Click on ‘Startup Settings’
(6). Click on ‘Restart’
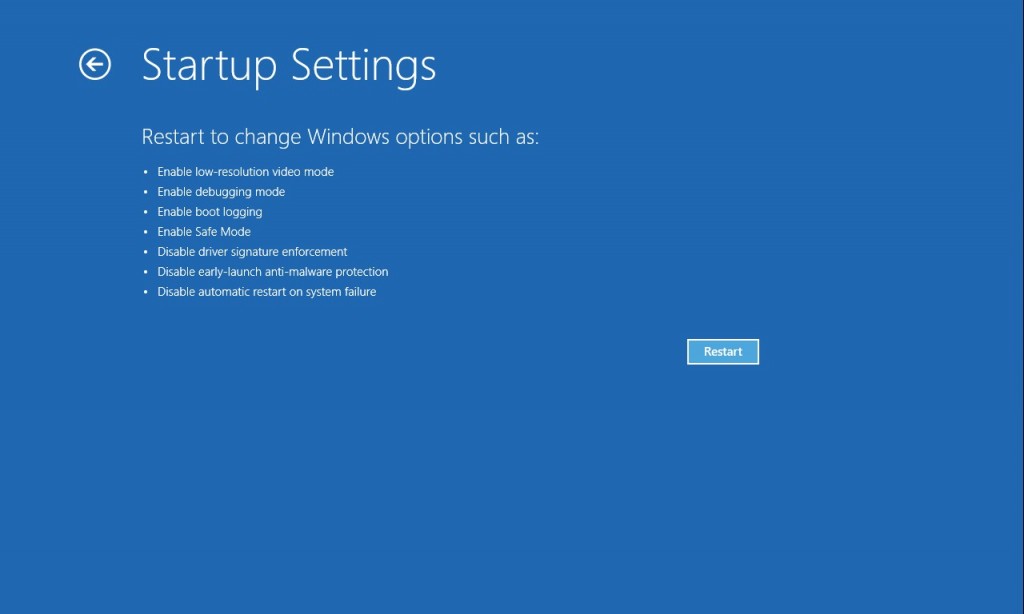
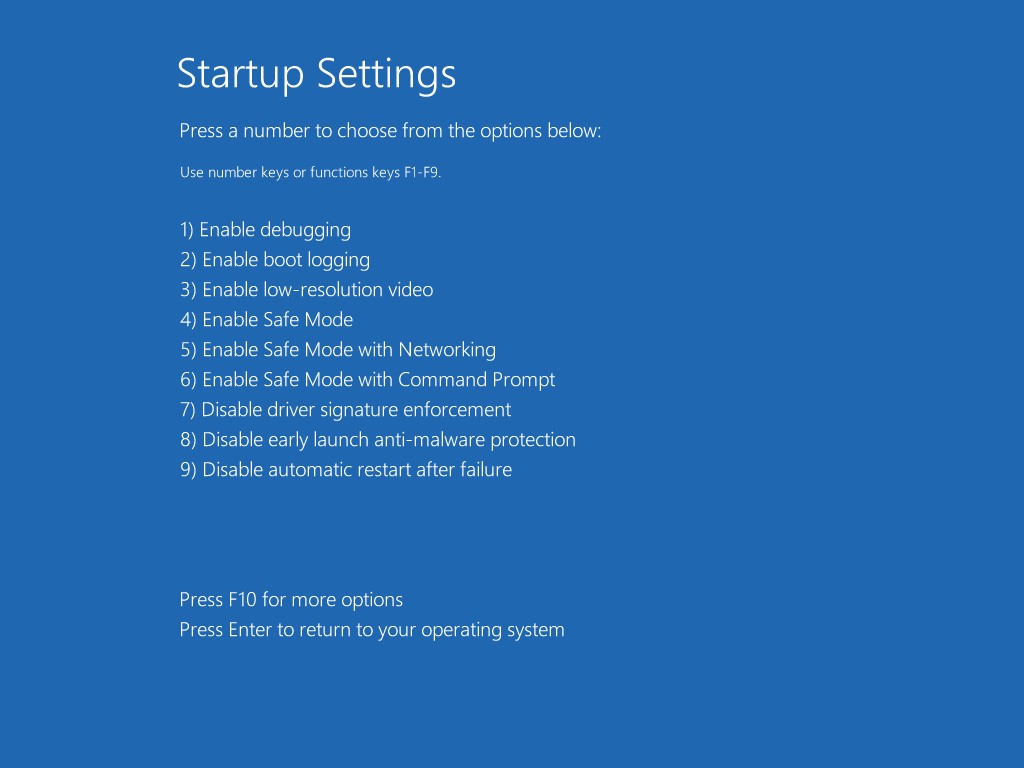
(7). The system will go through a reboot, please wait till you get the following screen. Choose ‘Enable safe mode with networking’ (or any other option you want to start up the system with)
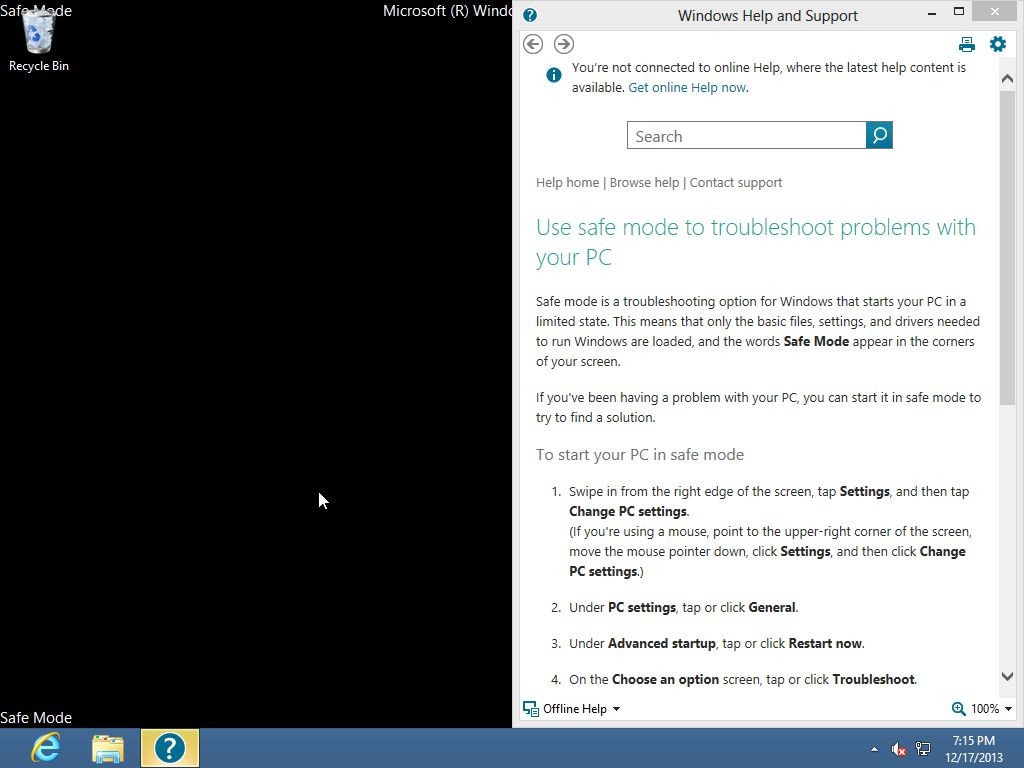
Then you can get into safe mode with networking in Windows 8 and see a desktop like this
2. Stop the Processes Related to Win 8 Protection 2014 in Windows Task Manager
For Windows 8
(1). Press Ctrl+Shift+Esc keys together to get Windows Task Manager
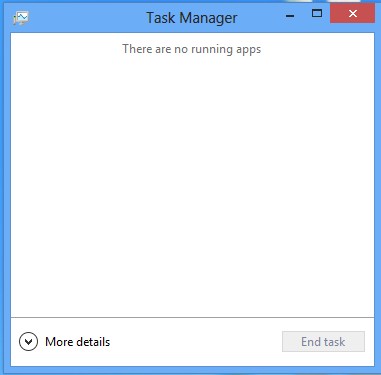
(2). Click More details
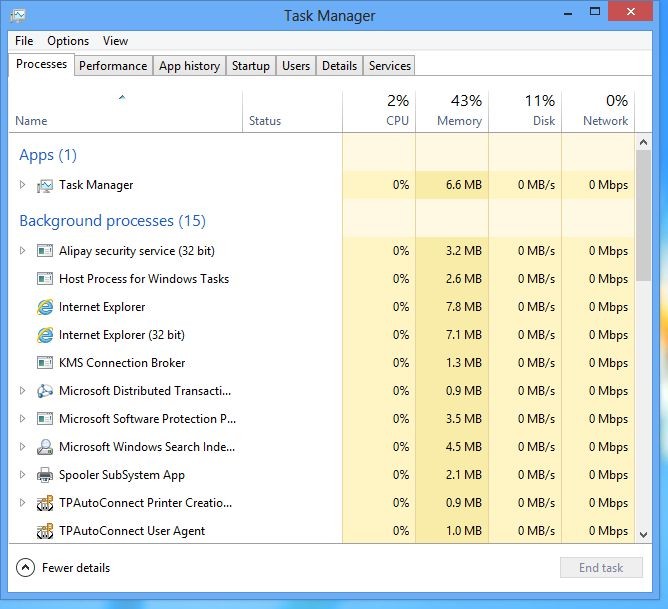
(3). Then scroll down to end the virus processes
3. Show Hidden Files
(1). Press Win+R to get Run option
(2). Type in Control Panel and hit enter to get Control Panel
(3). Click on Appearance and Personalization
(3). Click on Folder Options
(4). Click on View tab in Folder Options window
(5). Tick Show hidden files, folders, and drives under Hidden files and folders tab
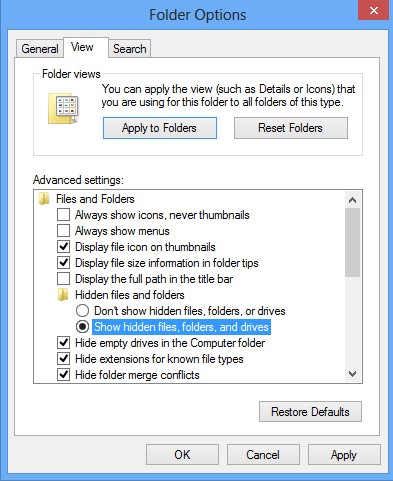
(6). Click Apply to take effect, then click OK at the bottom of the Folder Options window
4. Delete Virus Files
(1). Using Registry Editor to delete or adjust all the related registry entries of Win 8 Protection 2014 scam virus
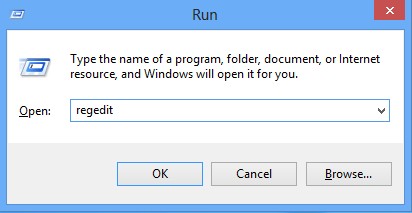
*Guides to open Registry Editor:
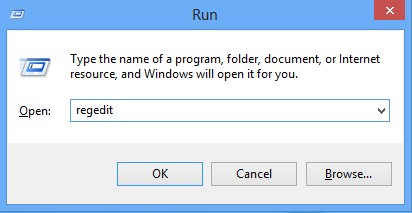
Press Win+R key together to get the Run box, type in ‘regedit’ then click OK, Registry Editor window will pop up
(2). Find out and remove the associated files of this fake Antivirus
In conclusion: Many computer users install antivirus programs in the computer in order to prevent the computer from being attacked by various viruses from the Internet. However, not all of the antivirus programs are real computer protection tools. This Win 8 Protection 2014 is a fake one. Ordinary computer users do not have the ability to distinguish fake antivirus software from real antivirus software. So knowing about the common characteristics of rogue antivirus will help us to reduce unnecessary losses. For example, this fake antivirus program we focus on here is able to be installed without permission. You may not know when it gets in the computer. It has the ability to escape most legal antivirus protection tools to sneak into the computer. Sometimes it can even replace the legitimate antivirus software, letting itself stay in the computer well at ease. It will start automatically every time you start the computer, scan the computer and then report to you that your system has many dangerous infections which should be removed as soon as possible. But you will notice that other antivirus applications in the computer do not detect anything. And when you try to use it to remove all these detected problems, you will be required to pay for its full version. In fact, computer hackers are behind the Win 8 Protection 2014. Therefore, this unfriendly software should not stay in the computer for a long time.
The above manual removal is quite dangerous and complicated, which needs sufficient professional skills. Therefore, only computer users with rich computer knowledge are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by on September 12, 2014 6:55 pm, last updated on September 22, 2014 9:17 am



Leave a Reply
You must be logged in to post a comment.