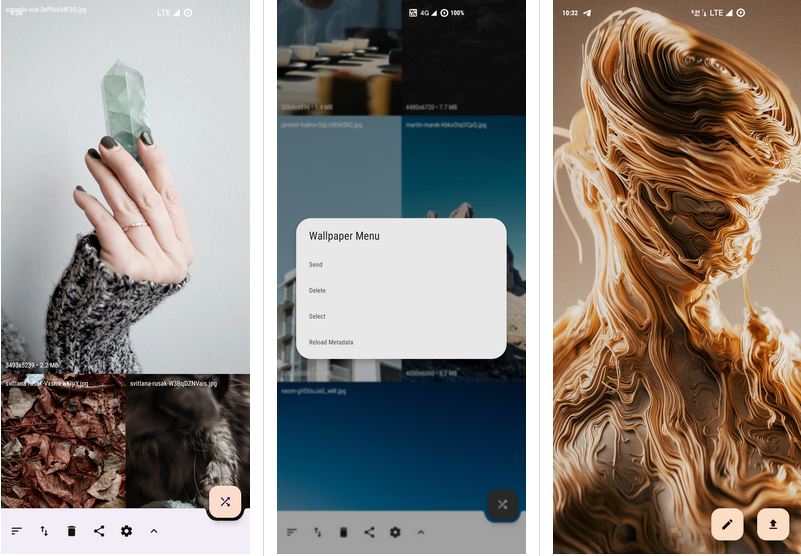
Peristyle: Build Your Local Wallpaper Library
Is there anyone like me, who has a million online wallpaper apps in his phone, but still prefers to use locally saved wallpapers? But with so many files, it’s not only not so convenient to use, but also makes the album app become bloated and complicated. Why can’t we treat these local wallpapers as a wallpaper app, and Peristyle is one such tool you can use to effectively organize these wallpapers in one place!
Published by YooCare Editor on May 28, 2024 2:11 am and last modified on May 28, 2024 2:16 am.
Artificial Intelligence (AI) is a very young technology, dating back to the 1950s, but it wasn’t until 2006 when scientists came up with the concept of deep learning that AI really came into the spotlight. The AI we’re talking about today is specifically the ChatGPT-induced AI boom, and more specifically, we’re actually talking about “generative AI”.
Generative AI is an artificial intelligence technology that can create or generate new content based on existing data. It’s like a robot that can draw and paint, and after it learns thousands of paintings, it’s able to draw a new one on its own. This kind of AI works in areas such as music, text, images, and video by understanding patterns and regularities in data and then applying that knowledge to create something new. In short, generative AI is an intelligent system that can ‘imagine’ and create new things.
Published by YooCare Editor on May 25, 2024 1:13 pm and last modified on May 26, 2024 2:16 am.
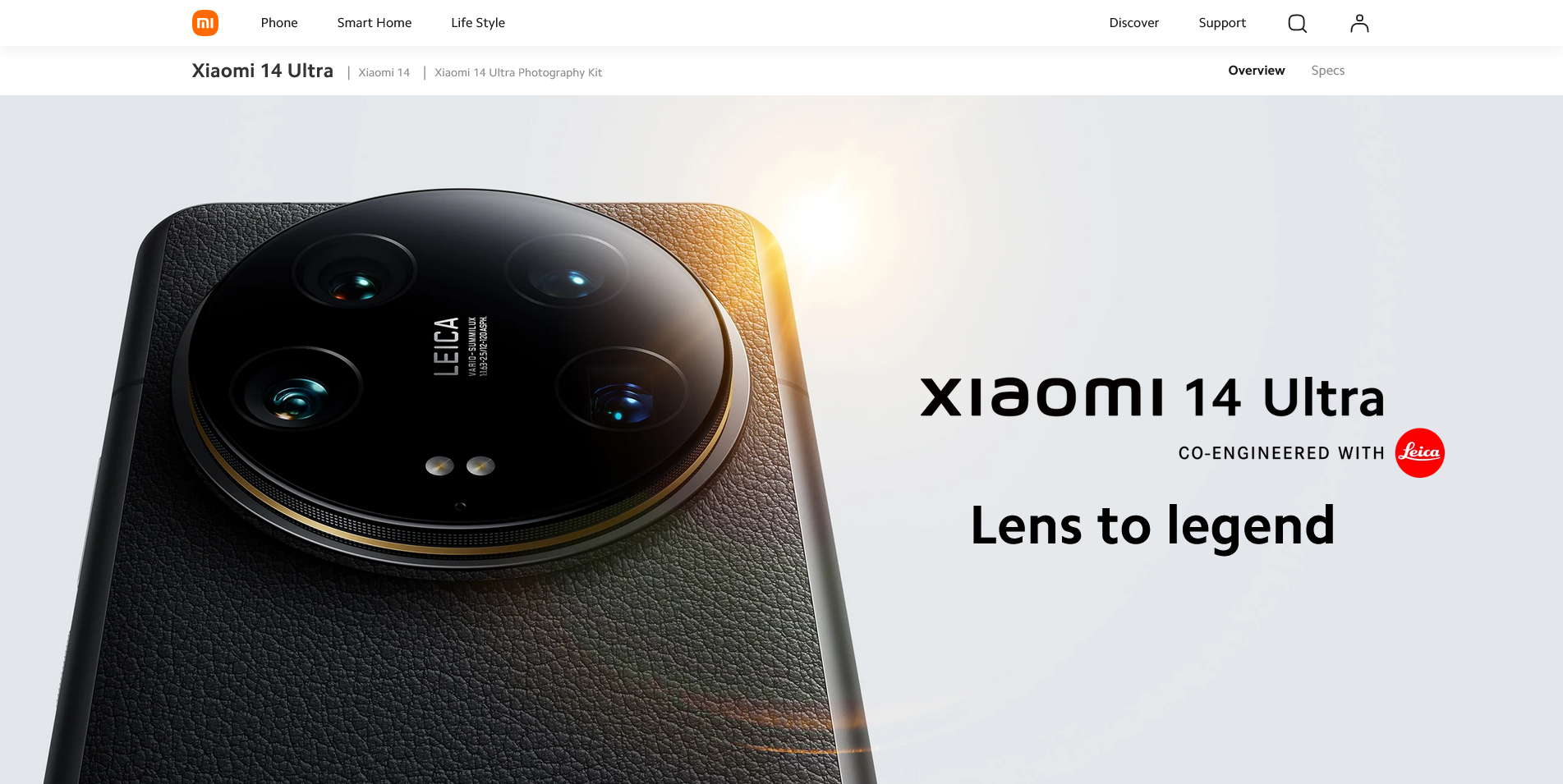
A little over a month ago, I got the Xiaomi 14 Ultra (and its camera grip kit) to replace the Xiaomi 12 Pro I was holding. On the one hand, the performance of my previous phone was a bit poor, with some of the games you know about dropping frames, especially with WeChat videos open at the same time, so it was time for an update. On the other hand, the previous Xiaomi 13 Ultra’s focus on photography really impressed me a bit, but I also saw some problems with the design of the phone, so I didn’t get my hands on it. And with this launch, I can feel that these previous issues, especially the center of gravity, have been greatly improved on the 14 Ultra. In addition, I have recently come to realize that not every moment of the day is suitable for carrying a camera with me when I travel. And cell phone photography is now quite sophisticated and can be a good complement to a camera for informal outings. This has given me a growing need to own a phone with better image quality.All of these reasons stacked together led to my decision to make my first purchase of the Xiaomi Mi 14 Ultra, which coincided with some recent work changes that coincided with a near two-week vacation to travel to Japan, and I got to experience the phone’s strengths and weaknesses in depth in the process.
Read the rest of this post »
Published by YooCare Editor on April 18, 2024 12:35 am and last modified on April 18, 2024 12:40 am.
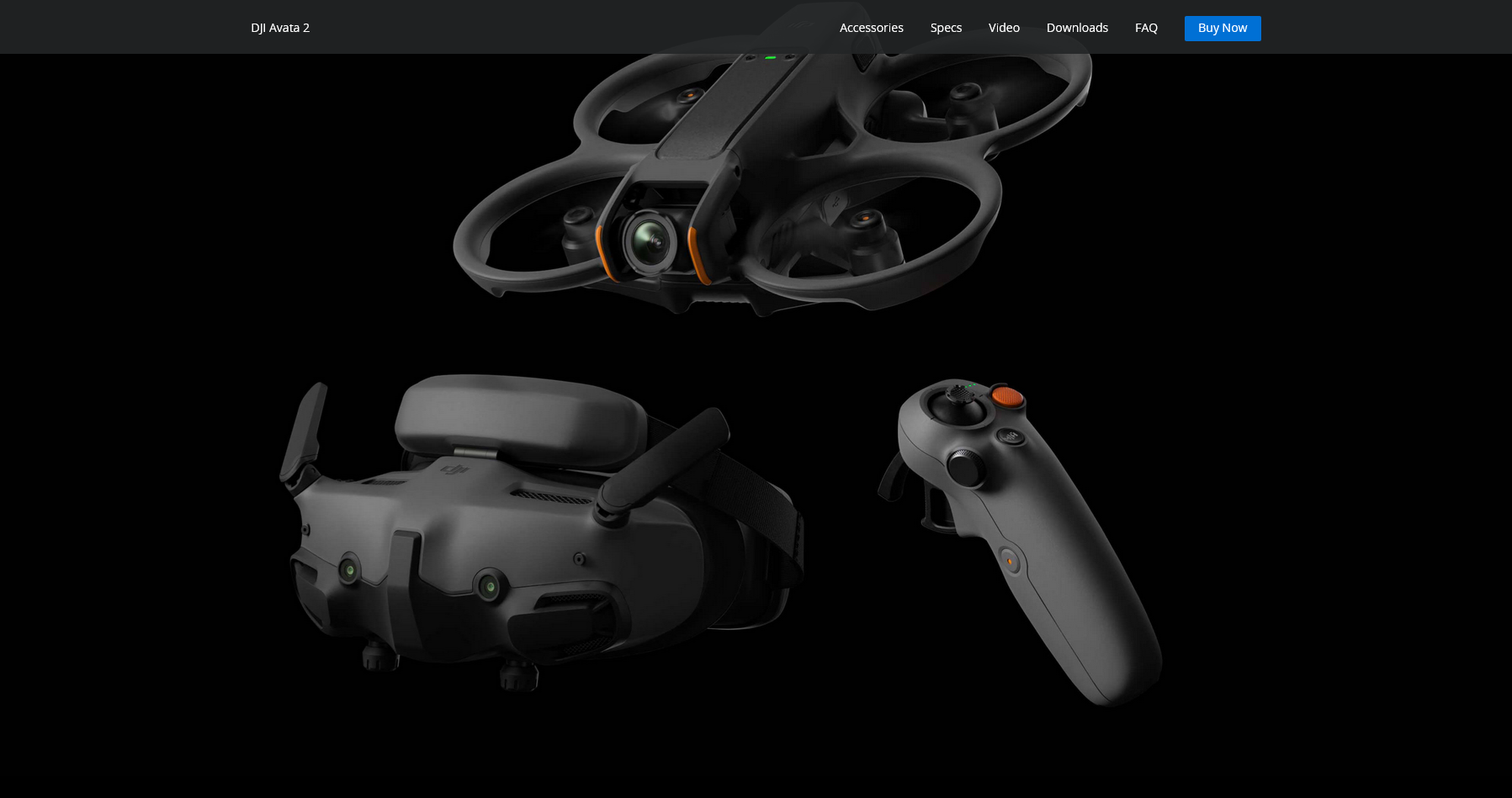
DJI Avata 2 has just bee released. Drones are flying higher and higher – becoming image creation tools, agricultural irrigation, and power and water surveys. It seems like you’d be laughed at if you said you wanted to buy one just to fly left and right at low altitudes. So after playing with the DJI Avata 2 for a while, no matter how many people play with it, for me, it’s finally what I imagined it would be – a proper and justifiable toy for adults.
Read the rest of this post »
Published by YooCare Editor on April 16, 2024 3:32 am and last modified on April 25, 2024 3:35 am.
Redmi Held a New Product Conference
On April 10th, the Redmi brand (Redmi) held a new product launch event, introducing several new products including the Redmi Turbo 3 smartphone, the Redmi Pad Pro tablet, the Mi Home Pro 1.5 horsepower fresh air conditioner, the Redmi MAX 100-inch 2025 model TV, and the Xiaomi TV S, among others.
Read the rest of this post »
Published by YooCare Editor on April 11, 2024 1:09 am
Apple Jing’an is the eighth Apple Retail Store in Shanghai, the 57th in Greater China, and one of the most highly anticipated. It’s been seven years since the store was closed for renovation in 2017, and on March 21st, Apple Jing’an will finally be opened.
Read the rest of this post »
Published by YooCare Editor on March 23, 2024 2:04 am and last modified on April 11, 2024 3:05 am.

February 20, 2023 , Fuji released the digital side-axis camera X100 VI, priced at around 2,000 bucks. The discussion about whether the Fujifilm X100 VI is worth it or not, and whether it’s worth the price increase is also clamoring.
Read the rest of this post »
Published by YooCare Editor on February 12, 2024 2:03 am and last modified on April 11, 2024 3:05 am.
Are you Unlocator fans? Do you know that Unlocator discount coupon is important during the signup? Who do you need discount coupon? It becomes popular to shop online. It is cheaper when you purchase the same product online than you do at the local shop. When you sign up a service online, you also can save big. For example, you get extra discount by applying Unlocator coupon code during the payment process. Sometimes, the company releases coupon and accept code for extra discount. Once our team receives Unlocator coupon code, we display on our website instantly. So you won’t miss the chance to save big. If the coupon code is not available, you also can use promotion for special deal at low cost. Let’s learn how to get the best deal with Unlocator coupon code. Get 100% Valid Discount. Read the rest of this post »
Published by YooCare Editor on January 20, 2024 9:21 am and last modified on June 11, 2024 2:06 am.
Unlocator is a Smart DNS and VPN service that allows users to bypass geo-restrictions and access content from different regions, while also providing privacy and security features. Now it becomes a powerful and popular VPN service powered by Smart DNS. With the background of solid security company, it delivers reliable and advanced Internet security and privacy solution. To keep you safe, Unlocator uses strong AES-256 encryption and supports various VPN protocols like OpenVPN, IKEv2, and IPSec for secure connections. These most secure protocols are supported by this VPN provider. It encrypts your connection to the Internet to prevent others from snooping in on your messages and conversations. You are safe to conduct important activities even on public WiFI hotspot. It has a wide and fast network with global servers in various countries. The combination of server locations and Smart DNS can assist you to hide your real location and unblock restricted contents. The VPN gives you the freedom to consume the content you value most. You will be able to bypass Internet censorship and defeat geo-restriction. Unlocator offers IP addresses from different cities and countries to replace and protect your real IP address which is your online ID. That prevents tracking and annoying ads. It is a great tool to protect privacy. The provider has no log policy and does not access your private online activities. This is a risk-free service as there is a “no question asked” 30-day money back guarantee. The price also is affordable. For more layer of protection, it provides bundles of VPN and security packages. Unlocator is worth a try.
Published by YooCare Editor on January 20, 2024 7:55 am and last modified on June 10, 2024 8:12 am.
Rewind: Music Time Machine
Platform: iOS and Android
Keywords: music, player
Teachers often say “you’re the worst class I’ve ever brought up”, audiences often say “the aesthetics of the entertainment has been seriously downgraded”, and music lovers often say “the music scene has regressed by twenty years”, in that case, try to turn on Rewind, and let it bring you back to the era of your favorite music through time and space, Rewind spans over 50 years, and allows you to go back to the 60’s, the era when psychedelia was flourishing, the late 70’s when punk and disco were popular, or the wave of electronic music at the beginning of the millennium. Rewind spans 50 years, so you can go back to the ’60s when psychedelia was booming, the late ’70s when punk and disco were big.
Read the rest of this post »
Published by YooCare Editor on January 16, 2024 7:53 am and last modified on April 10, 2024 10:14 am.


