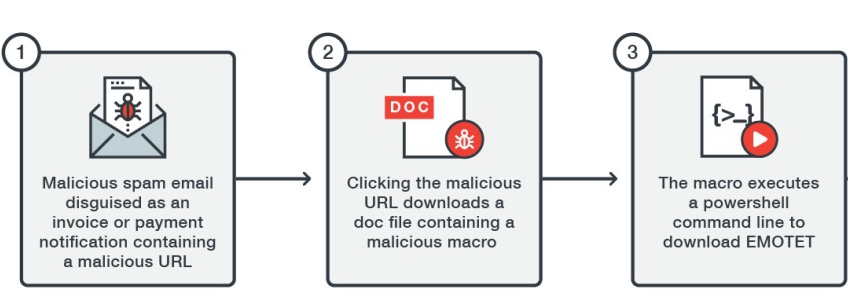
The TA505 cyber espionage group has been active again recently. In the past few weeks, the organization has launched attacks against the UAE, Saudi Arabia, India, Japan, Argentina, the Philippines and South Korea. Their main targets were various countries’ financial institutions.
Since 2014, TA505 cyber espionage organization has been remaining active. In the past few years, the organization successfully launched a large number of large-scale network attacks by using the banking Trojans Dridex and extortion software Locky and Jaff. TA505 mainly used the new malware Gelup and FlowerPippi in the attack against Asian countries which is different from the past attacks.
On June 11, the TA505 cyber espionage organization launched a spam campaign against the UAE, Saudi Arabia and Morocco. The spam attachment used in this attack was a .html or .xls file. After the attached HTML file is run, the Excel file containing the malicious Excel 4.0 macro will be downloaded. After executing the malicious macro, it will download the FlawedAmmyy installation package file and install the FlawedAmmyy RAT.
If the attachment is an .xls file, the file itself contains malicious Excel 4.0 macro code. When it is executed, it downloads the FlawedAmmyy installation package file and installs the FlawedAmmyy RAT.
On June 13, researchers again intercepted spam attack samples that added .doc files in addition to the previous .html and .excel files.
On June 14, the researchers saw that the TA505 continued to attack the UAE. The attack methods and techniques used were similar to those of the previous one. The attack sent spam through the Amadey botnet, which used a Wizard (.wiz) file. The ultimate goal is still to download and install the FlawedAmmyy RAT.
On June 18th, most of the spam topics intercepted by researchers were tempting and deceiving users to click. They included message such as “your RAKBANK tax invoice”, “tax exemption” or “confirmation letter”. The attachment was also an Excel or Word document with the above .html file with malicious macros. The ultimate goal is to download and install FlawedAmmyy RAT and Amadey. It then sends an “EmailStealer” message stealer that steals Mail Transfer Protocol (SMTP) credentials and email addresses from the victim’s machine.
Researchers have found at least hundreds of SMTP credentials on their C&C servers, more than one million email addresses, 80% of which were .com or .ae top-level domains.
On June 17, AsiaInfo security researchers intercepted a large number of spam attacks against Asian banks. These messages used the theme of “Emirates NBD Electronic Declaration” or “Visa Cancellation” to trick users into clicking email attachments with malicious Excel file. After running it, it will download the ServHelper loader.
On June 20th, researchers again intercepted spam attacks against Japan, the Philippines, and Argentina. The email attachments were also .doc and .xls files with macro viruses. The difference was that macro viruses would eventually download undisclosed malicious Software FlowerPippi and Gelup. Gelup malware is written in C++. The difference is the obfuscation technique and the UAC bypass feature, which can effectively prevent static and dynamic debugging analysis. FlowerPippi has a back door and download function.
On the same day, the researchers also intercepted spam attacks against South Korea. Unlike previous attacks, the email did not contain attachments. Instead, malicious URLs were embedded in the body of the email once they were accessed. A malicious URL that downloads .doc and .xls files containing macro viruses. The ultimate goal is also to download the FlawedAmmyy RAT. With the increasing cyberattacks, it is very important to install a piece of reliable security software on your device.
Published by on July 18, 2019 2:23 am, last updated on July 18, 2019 2:24 am



Leave a Reply
You must be logged in to post a comment.