The FBI is suggesting users of consumer-grade routers and network-attached storage devices to reboot them as soon as possible to fight back Russian-engineered malware that has infected hundreds of thousands devices.
Researchers from Cisco’s Talos security team first disclosed the existence of the malware on Wednesday. The detailed report said the malware infected more than 500,000 devices made by Linksys, Mikrotik, Netgear, QNAP, and TP-Link. Known as VPNFilter, the malware allowed attackers to collect communications, launch attacks on others, and permanently destroy the devices with a single command. There are a persistent stage 1 and non-persistent stages 2 and 3 to VPNFilter. According to how the malware works, rebooting will clear out stages 2 and 3 and mitigate most problems.
Cisco said in a report, “The VPNFilter malware is a multistage, modular platform with versatile capabilities to support both intelligence collection and destructive cyberattack operations.” As the malware could collect data from the user and even perform a large-scale destructive attack, Cisco recommends that owners of SOHO or network attached storage (NAS) devices be especially cautious with this type of attack. As it’s unclear how compromised device gets infected in the first place, officials are urging users of all routers and NAS devices to reboot. Here is what the official wrote:
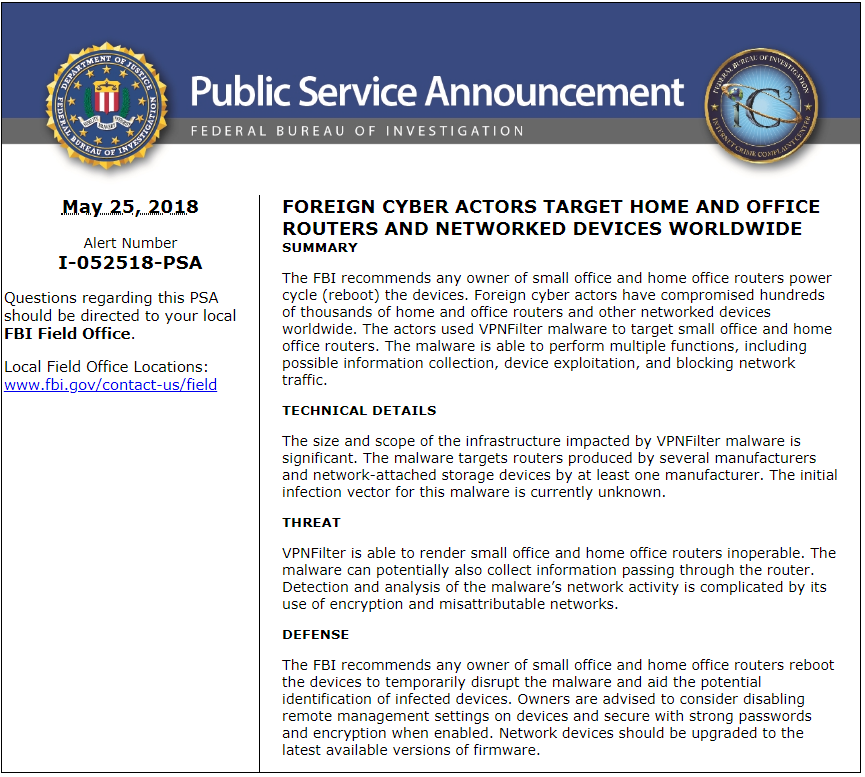
“The FBI recommends any owner of small office and home office routers reboot the devices to temporarily disrupt the malware and aid the potential identification of infected devices,” FBI officials warned. “Owners are advised to consider disabling remote management settings on devices and secure with strong passwords and encryption when enabled. Network devices should be upgraded to the latest available versions of firmware.”
The Justice Department also issued a similar warning, urging users to reboot their routers. “Owners of SOHO and NAS devices that may be infected should reboot their devices as soon as possible, temporarily eliminating the second-stage malware and causing the first-stage malware on their device to call out for instructions,” the department said in a statement. “Although devices will remain vulnerable to reinfection with the second-stage malware while connected to the Internet, these efforts maximize opportunities to identify and remediate the infection worldwide in the time available before Sofacy actors learn of the vulnerability in their command-and-control infrastructure.”
Cisco advised all users to perform a factory reset of their devices, which would clear out even stage 1 of the malware. If you are not good at computer, you are suggested to contact computer experts for help or router manufacturer for instructions. The reset will remove any configuration settings stored on the device, so users will have to restore those settings once the device initially reboots.
Published by on May 28, 2018 2:42 am, last updated on May 28, 2018 2:43 am



Leave a Reply
You must be logged in to post a comment.