I currently use AVG Internet protection on my Dell laptop. Last night I encountered a malware problem on a free download. AVG keeps saying it found Trojan Horse36.BAHP virus but never took any actions to quarantine it. When I have tried to remove it, AVG says “Cannot be removed. Data is not valid”. The virus appears to affect the functioning of my PC. Everything is extremely slow on my computer. How do I get rid of it? Any help will be appreciated.
Trojan Horse36.BAHP is categorized as Trojan virus that can disable your firewall and current antivirus program and then break into a vulnerable system without any knowledge until it is detected by AVG. This is a nasty virus and computer users may get infected by it after clicking on some malicious links, downloading free software from the internet which usually contains potentially unwanted programs or other infections, browsing sites with bad reputation or opening the infected email attachments. Once it is installed, the virus modifies crucial system files to set itself run automatically therefore every time turn the PC on, an annoying alert will keep popping up every few seconds saying your PC has been infected. However, any actions to delete the virus are unavailable. You will get error message like “Cannot be removed. Data is not valid” or others as long as you click on “Remove” option on AVG. Trojan Horse36.BAHP is certainly a stubborn virus and it is suggested users remove it manually instead.
As similar as other types of Trojan virus, this one can also perform many evil actions on the infected system as soon as it is installed. It can take control over users’ computer systems and make some important services or programs unusable. So you may get the same problem that when you try to go online or open a program, the window hangs up and you get errors saying “Not Responding” or “Windows Explorer is stop working”. Various problems such as Blue Screen of Death, system crash or program corruption may also happen on the machine. In addition, the virus endangers the privacy of computer users. It may corrupt users’ important documents and collect users’ sensitive information or data for the malicious purposes. This Trojan also opens a backdoor secretly that can make other viruses and spyware get into the computer and wreak chaos. In a word, it is urgent to remove Trojan Horse36.BAHP virus once upon detection.
Slow down your PC speed notably.
Add other dangerous Trojan or Spyware to your system secretly.
Allow the hacker to access your entire system.
Collect all your personal information and transfer to a remote hacker.
Destroy critical system files and make PC unstable.
From malicious drive-by-download scripts from corrupted porn and shareware / freeware websites.
Through spam email attachments, media downloads and social networks.
When clicking suspicious pop-ups or malicious links.
Open unknown email or download media files that contain the activation code of the virus.
Note: No matter how the virus accesses your PC, users should know that there are no tools can remove this pesky Trojan automatically at this moment, it is suggested users not spend much time in downloading or paying any security software which claims can delete this stubborn virus. It is totally useless. To completely get rid of Trojan Horse36.BAHP virus, professional manual guide is needed.
Currently many computer users had the same experience that this virus couldn’t be removed by any anti-virus applications. So the manual approach is always required to combat this virus. And here is the step-by-step removal guide for all computer users.
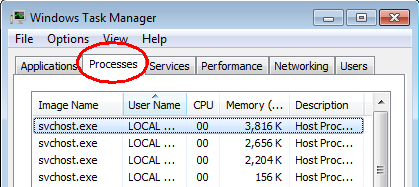
1. End the malicious process from Task Manager.
Once Trojan Horse36.BAHP virus is installed, computer user may notice that CPU usage randomly jumps to 100 percent. At any time Windows always has many running processes. A process is an individual task that the computer runs. In general, the more processes, the more work the computer has to do and the slower it will run. If your system’s CPU spike is constant and remain at a constant 90-95%, users should check from Task Manager and see if there is a suspicious process occupying system resources and then end it immediately.
(The name of the virus process can be random.)
Press Ctrl+Shift+Esc to quickly bring up Task Manager Window:
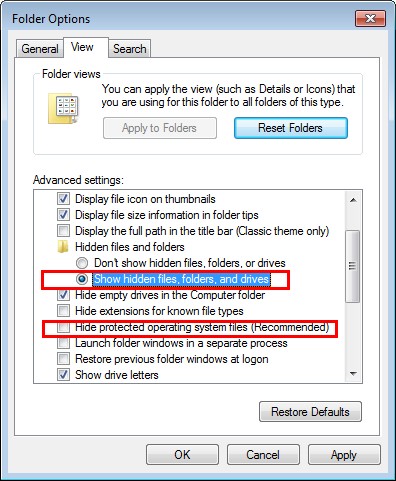
2. Show hidden files and folders.
Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
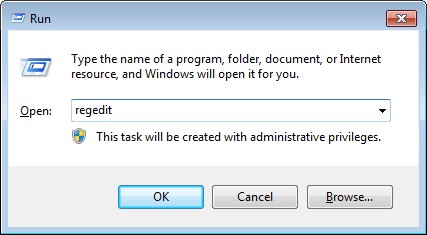
3. Open Registry entries. Find out the malicious files and entries and then delete all.
Attention: Always be sure to back up your PC before making any changes.
a. Press Windows key + R to open Run box. In the “Open” field, type “regedit” and click the “OK” button.
Then a Registry Editor window will pop up as the following picture shows:
b. Search malicious files and registry entries and then remove all of them:
%AllUsersProfile%\[random]
%AppData%\Roaming\Microsoft\Windows\Templates\[random]
%AllUsersProfile%\Application Data\.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\[random]
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Temp
Trojan Horse36.BAHP is classified as a highly dangerous Trojan that aims to attack Windows operating system including Windows XP, Windows Vista, Windows Vista, Windows 7 and even Windows 8 (Windows 8.1). It is designed by cyber criminals to steal account information, passwords, online banking data and credit card information from the target users. Usually the virus is distributed via spam email attachments or hacked web sites. It also can be installed when users download or update share programs or games from the Internet. The virus can record your keyboard activities and collect your confidential information like user names, passwords, and credit card data so you need to get rid of it with no delay.
Note: If you are not knowledgeable enough to be able to distinguish the location of this virus, or you are afraid of making mistake during the manual removal, please contact experts from Yoocare Online Tech Support for further help.
Published by on March 15, 2015 6:59 am, last updated on March 15, 2015 6:59 am



Leave a Reply
You must be logged in to post a comment.