What is the Exploit:Java/Obfuscator.AH? How can it enter the computer? Why is my antivirus program unable to stop and remove it? What kind of damages this virus can bring to my computer system? Is there a good way to completely get rid of this annoying virus?
Exploit:Java/Obfuscator.AH is classified as a malicious computer virus created by hackers to mess up your computer and collect your valuable information without letting you know. Because the virus is especially designed by hackers with evil purposes, it has the ability to bypass most of antivirus programs to sneak into your computer. That is why it still can get into your computer successfully even if the computer is equipped with an antivirus program. The virus is very dangerous! First of all, it will weaken the system to create loopholes in the system in order to bring in more viruses helping hackers to remote into the computer. Other effects of the virus include replacement of the system data and files, redirecting the browser and slowing down the speed of the computer.
Trojan viruses, browser hijackers, fake antivirus software and ransomware can be seen everywhere in the Internet world. But the Exploit:Java/Obfuscator.AH virus is different, because it is invisible in your computer. You should not underestimate the power of the virus. It is able to sneak into your computer without your consciousness with the help of other online resources. It can not only reduce the computer performance but also bring in many problems such as blue screen of death and random restart. It is very active in the system backdoor. All your activities in the infected computer are not safe because it allows the virus makers to connect to the infected computer. You must feel terrible, if you know that there is someone watching you no matter what you do. Your personal information may be stolen, if you do not remove the virus in time. It has the ability to delete the default important system files and then inject its malicious files so that the antivirus programs cannot remove it successfully.
1. It has the ability to download additional components and other infections in the target computer in order to fully complete its penetration.
2. It is able to cause system crash and destroy some of your programs in the infected computer.
3. It facilitates the virus makers to intrude your computer remotely without letting you know.
4. It is capable of collecting your browsing history and other private data.
What is the best way to get rid of Exploit:Java/Obfuscator.AH? Here we suggest manual removal. The following are some manual steps on how to get rid of this kind of virus. Because it has the ability to change, you may not be able to find out some of the files listed below. In other words, professional knowledge is needed to process the manual removal. You are recommended to do a backup in advance.
1. End Relevant Processes
(1). Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab
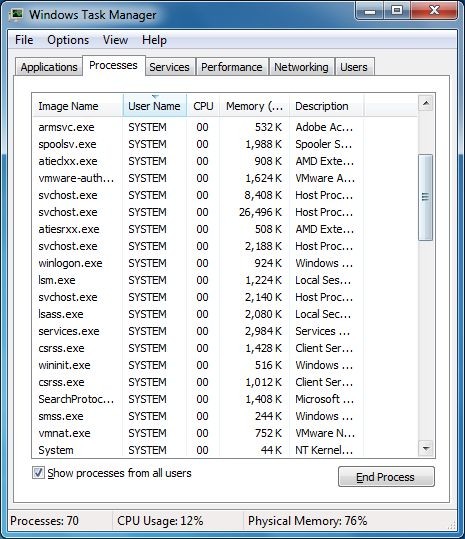
*For Win 8 Users:
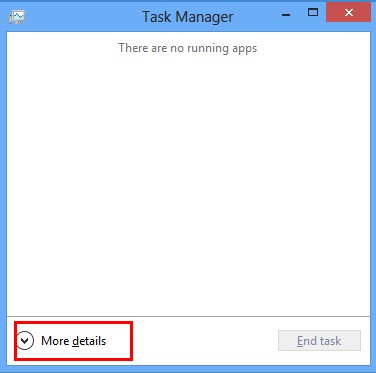
Click More details when you see the Task Manager box
And then click Details tab
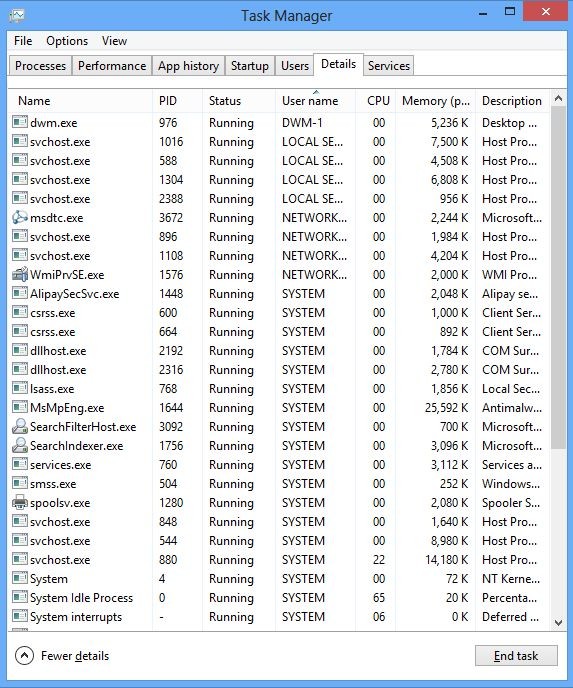
(2). Find out and end the processes of Exploit:Java/Obfuscator.AH
2. Show Hidden Files
(1). Click on Start button and then on Control Panel
(2). Click on Appearance and Personalization
(3). Click on Folder Options
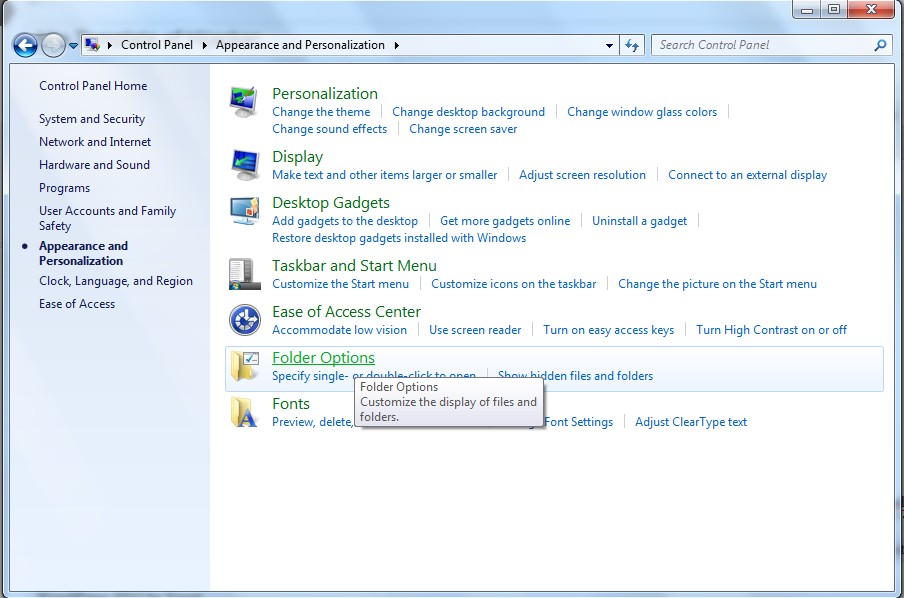
(4). Click on the View tab in the Folder Options window
(5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
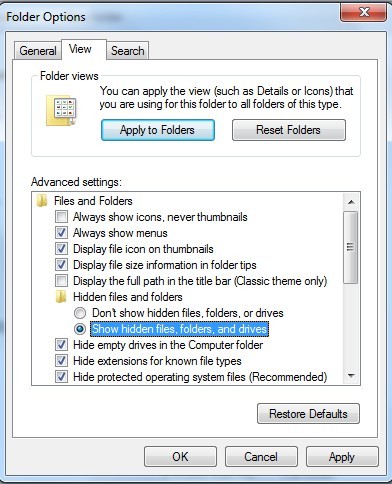
(6). Click OK at the bottom of the Folder Options window
*For Win 8 Users:
Press Win+E together to open Computer window, click View and then click Options
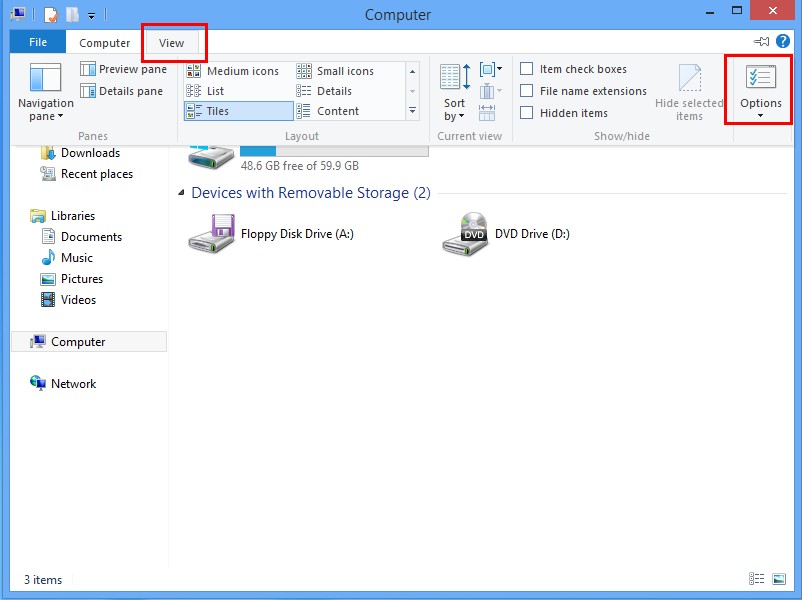
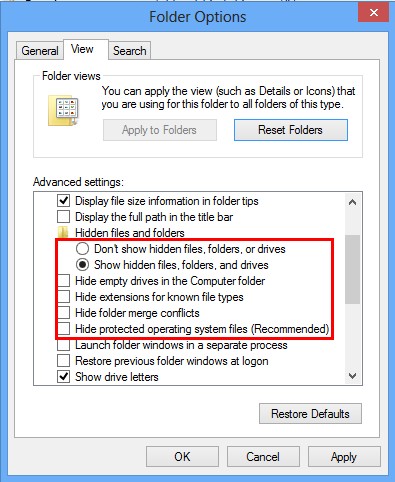
Click View tab in the Folder Options window, choose Show hidden files, folders, and drives under the Hidden files and folders category
3. Delete Relevant Registry Entries and Files
(1). Delete the registry entries of Exploit:Java/Obfuscator.AH through Registry Editor
Press Win+R to bring up the Run window, type “regedit” and click “OK”
While the Registry Editor is open, search and delete the related registry entries
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Random’
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
(2). Find out and remove the associated files
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
%AllUsersProfile%\Application Data\~random
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
Do you always get some security warnings and pornography pop-up ads? Exploit:Java/Obfuscator.AH is the origin. It has the ability to implant more and more computer virus infections such as browser hijackers, worms, fake antivirus programs and malicious software into the computer to seriously mess up the computer. Therefore, you may encounter a lot of other issues with this hateful virus in your computer. Antivirus programs are unable to delete it completely from your computer. Thus, manual removal is an effective method to fix your computer instead of formatting the hard disk which will result in the reduction of hard disk’s life.
The above manual removal is quite dangerous and complicated, which needs sufficient professional skills. Therefore, only computer users with rich computer knowledge are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by on December 1, 2014 4:09 am, last updated on December 1, 2014 4:09 am



Leave a Reply
You must be logged in to post a comment.