After the invasion from Trojan Horse Backdoor Generic 12. Ceyl is successful, the running speed of the infected computer becomes very slow and many strange problems occur? Do not know how to delete it if various antivirus programs do not seem to be able to handle it successfully? By reading this article, you can get a good antidote to the infected computer.
Trojan Horse Backdoor Generic 12. Ceyl is a new computer Trojan virus which is able to hide in the target computer system deep. Some computer users can see the related warning from the antivirus program. However, the Trojan has the ability to stay firmly in the computer for the majority of antivirus programs cannot remove it. In general, if you are not careful when you use any cyber resources, your computer will be attacked easily by this terrible virus, such as accessing to suspicious web sites, downloading unknown free programs and opening unknown links.
In order to successfully run in the background of the infected computer system, Trojan Horse Backdoor Generic 12. Ceyl adds its malicious registry keys as well as files to the system. If you allows it to remain in the computer for a long time, other kinds of computer infections (including malicious programs, browser hijackers, worms or spyware) will continue to access your computer. So, you will receive all kinds of warnings constantly from the antivirus program. In addition, tolerating this Trojan virus is to encourage the virus to get evolved and makes the removal become more difficult. On the other hand, it facilitates the virus makers to remote into the infected computer without letting you know. They can implant key-logger and spyware to record your computer operating traces, corrupt your important documents and steal your private information stored in the computer. Therefore, you should try your best to fight against the virus. Unfortunately, Rootkit technology helps it root deep in the infected computer. Hence, antivirus programs cannot help you clean it effectively. If you are trapped in this case, you can consider to manual removal.
1. It has the ability to download additional components and other infections in the target computer in order to fully complete its penetration.
2. It is able to cause system crash and destroy some of your programs in the infected computer.
3. It facilitates the virus makers to intrude your computer remotely without letting you know.
4. It is capable of collecting your browsing history and other private data.
The Trojan is a dangerous threat. It can collect your personal information and send you more malicious infections. You will see some unnecessary things appearing on the computer but you cannot get rid of them. It also slows down the computer seriously. Therefore, your computer is in a dangerous situation. You must know that it will help the network criminals to steal your valuable information and damage your computer. Therefore, you should find an effective way to get rid of it.
1. End Relevant Processes
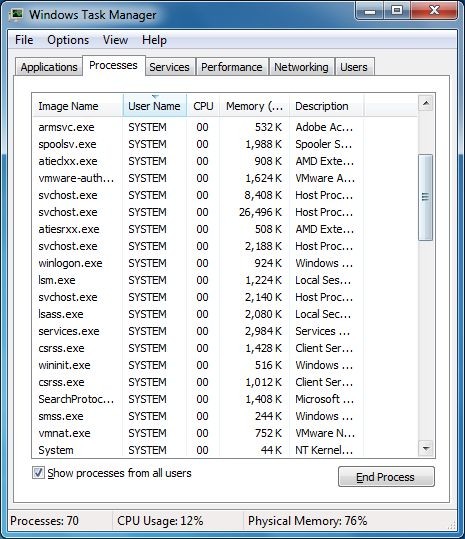
(1). Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab
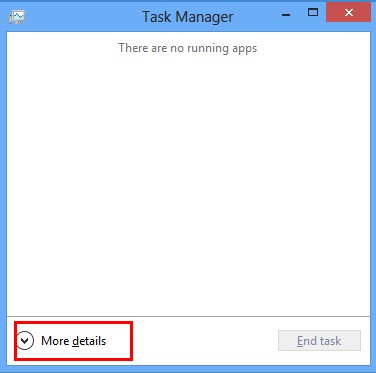
*For Win 8 Users:
Click More details when you see the Task Manager box
And then click Details tab
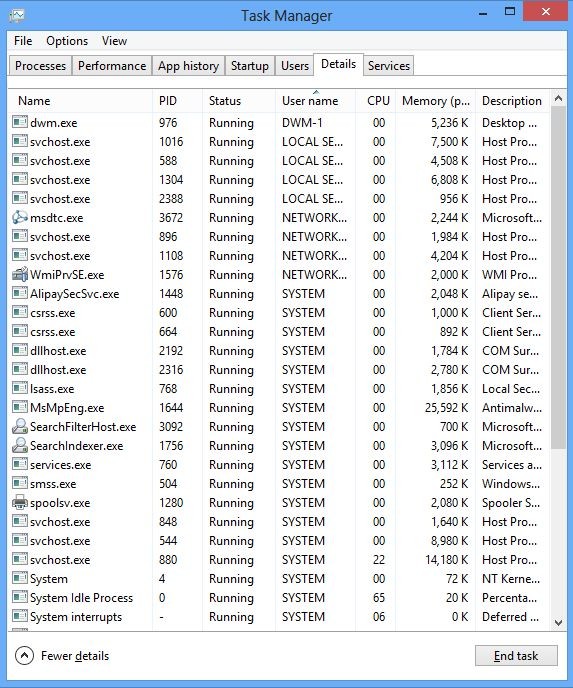
(2). Find out and end the processes of the Trojan Horse
2. Show Hidden Files
(1). Click on Start button and then on Control Panel
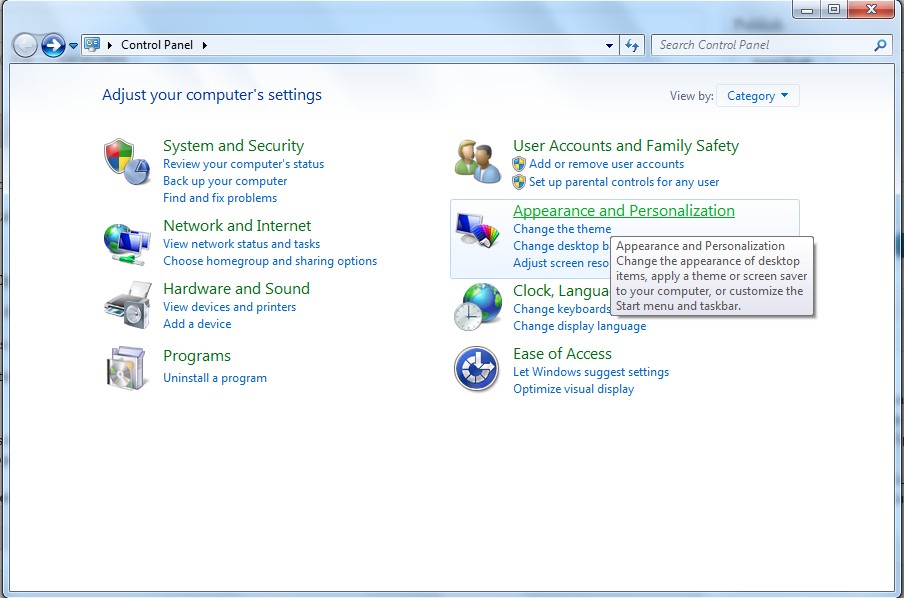
(2). Click on Appearance and Personalization
(3). Click on Folder Options
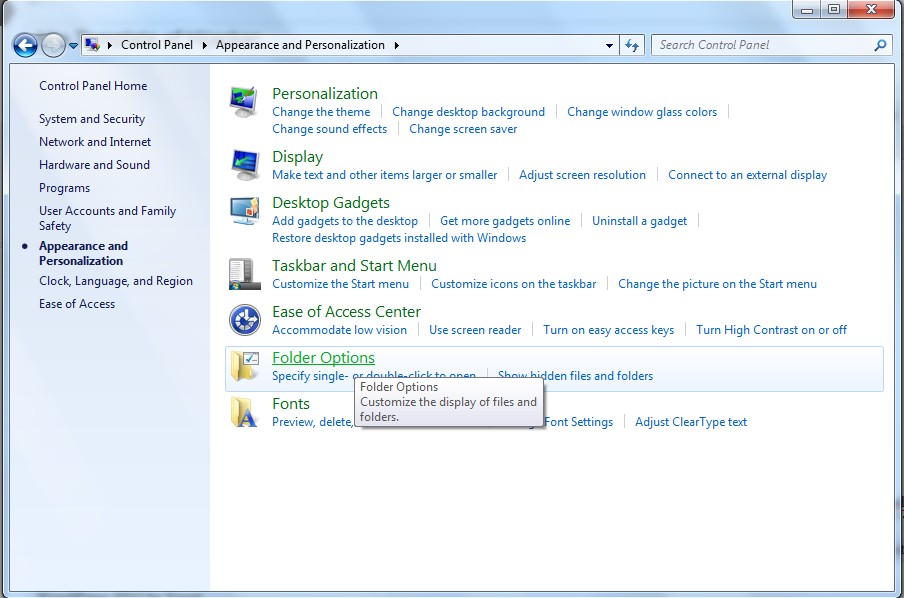
(4). Click on the View tab in the Folder Options window
(5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
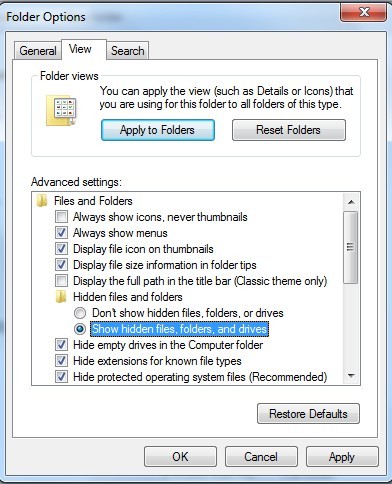
(6). Click OK at the bottom of the Folder Options window
*For Win 8 Users:
Press Win+E together to open Computer window, click View and then click Options
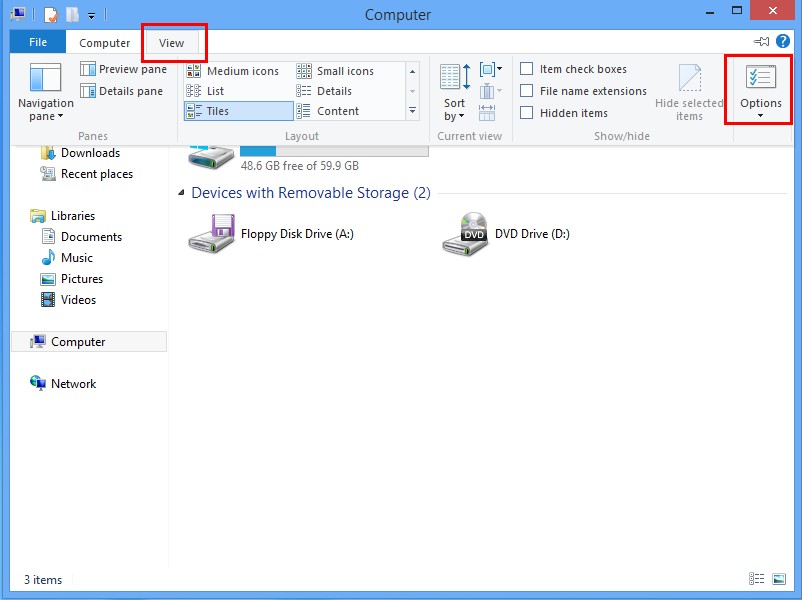
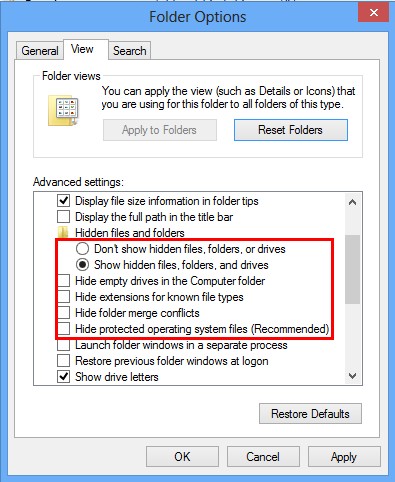
Click View tab in the Folder Options window, choose Show hidden files, folders, and drives under the Hidden files and folders category
3. Delete Relevant Registry Entries and Files
(1). Delete the registry entries of Trojan Horse Backdoor Generic 12. Ceyl through Registry Editor
Press Win+R to bring up the Run window, type “regedit” and click “OK”
While the Registry Editor is open, search and delete the related registry entries
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Random’
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
(2). Find out and remove the associated files
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
%AllUsersProfile%\Application Data\~random
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
Trojan Horse Backdoor Generic 12. Ceyl is a highly dangerous Trojan virus. It enters the computer secretly and many computer users even do not know when it begins the attack. Because it needs a large amount of computer system resources to run in the background, the infected computer responds slowly. It also modifies system files and leads to blue screen of death or system crash. It has the ability to spread other Trojans and worms to the computer. Worst of all, it helps the cyber criminals to access your computer and collect your personal information. Therefore, you need to delete the Trojan Horse from your computer as early as possible.
The above manual removal is quite dangerous and complicated, which needs sufficient professional skills. Therefore, only computer users with rich computer knowledge are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by on October 27, 2014 7:51 am, last updated on October 27, 2014 7:51 am



Leave a Reply
You must be logged in to post a comment.