Do you know anything about Exploit:JS/Dotcaf.A? You may have found that your computer has become super slow but can’t figure out the problem. You believe your antivirus program installed on the computer is able to protect your computer from any cyber threat. No wonder you’re surprised to see the antivirus program pops up alert to tell you that the computer is infected with Exploit:JS/Dotcaf.A. Why antivirus program cannot deal with it? Is there any way to completely deal with the nasty infection? Yes, now there is a manual method to delete the virus completely. Learn more from this post.
Exploit:JS/Dotcaf.A is classified as an severe and malicious Trojan horse which explicitly concentrates in attacking Windows operating system. Once the nasty virus gets sneaked, the infected computer will encounter a degraded performance as it keeps taking up the high resource of the CPU so that it takes a long time for users to run some programs. And this threat can stop the users from normal web surfing and the computer may get stuck when they go online. It is capable to alter browser homepage settings and annoy users by redirecting them to infected websites. It also tricks users to download malicious softwares and convince them to purchase its useless licensed version product. What is worse, the Trojan can damage important files as its own will, and as a result it makes those files permanently inaccessible.
Exploit:JS/Dotcaf.A can corrupt your windows registries by adding malicious payloads and as a result a lot of strange files instead of the original files emerge on the computer without your consent. The antivirus may detect it but can’t deal with it successfully because once you delete it from one location, it immediately create another copy and spread itself in the computer quickly. It is capable to track your Internet activity and collect the valuable personal information like bank card details, IP address, email contact and etc. Besides, this dangerous Trojan would provide a back door by exploiting system security flaws for cyber criminals sitting remotely to take control of your computer. And it brings other threats including spyware, malware and ransomware to mess up the computer hand in hand. Anyway, this Trojan is such a harmful infection which needs to be removed completely before it starts wreaking havoc on the system.
Exploit:JS/Dotcaf.A allows cyber-criminals to break into the infected computer without being noticed and it could disable executable programs installed on your computer and cause system crash. Also it will change important settings on your computer to allow remote control from cyber criminals. Other than that, it will modify your registry settings and important key value to make it difficult to be removed.
Manual removal is suggested here if the antivirus program in your computer can’t deal with it. The most guaranteed way to get rid of the Trojan Exploit:JS/Dotcaf.A without reinstalling the system or formatting the hard disk is manual removal. Here are some basic steps to achieve this point. However, removing the virus manually requires high skills in order to determine which files to delete for the Trojan infection is changing with the passage of time. You are also suggested to do a backup before starting.
1. End Relevant Processes
(1). Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab
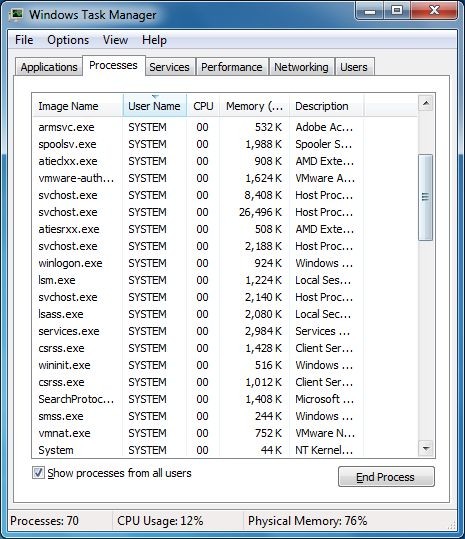
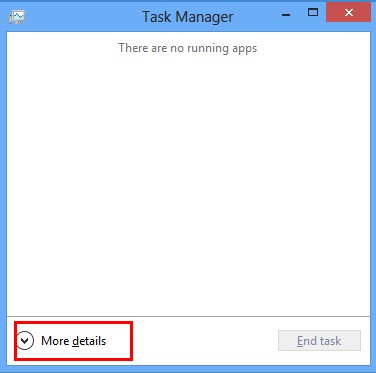
*For Win 8 Users:
Click More details when you see the Task Manager box
And then click Details tab
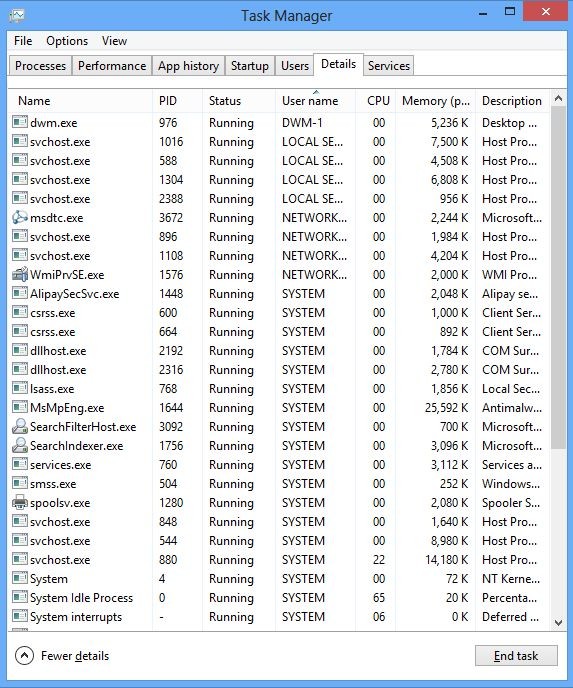
(2). Find out and end the processes of Trojan Exploit:JS/Dotcaf.A
2. Show Hidden Files
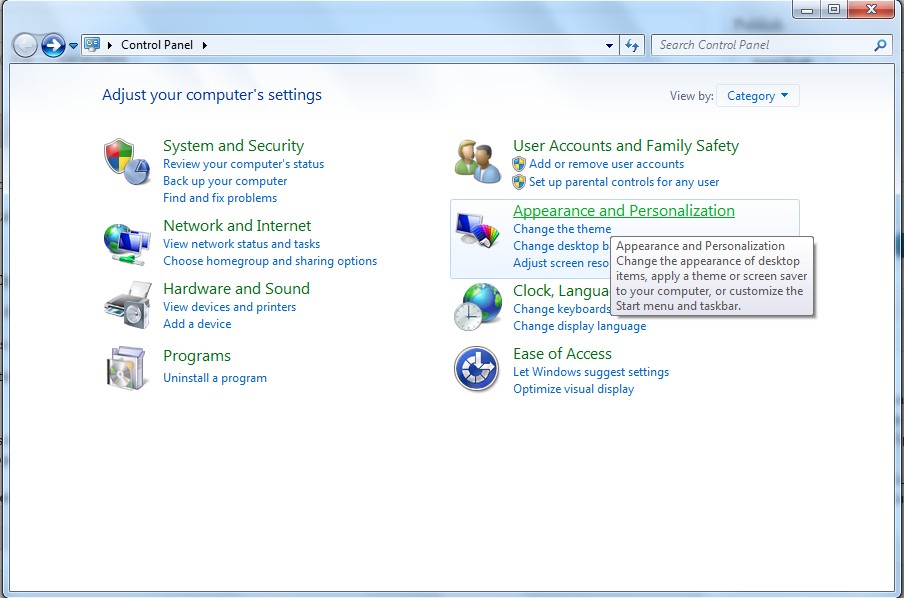
(1). Click on Start button and then on Control Panel
(2). Click on Appearance and Personalization
(3). Click on Folder Options
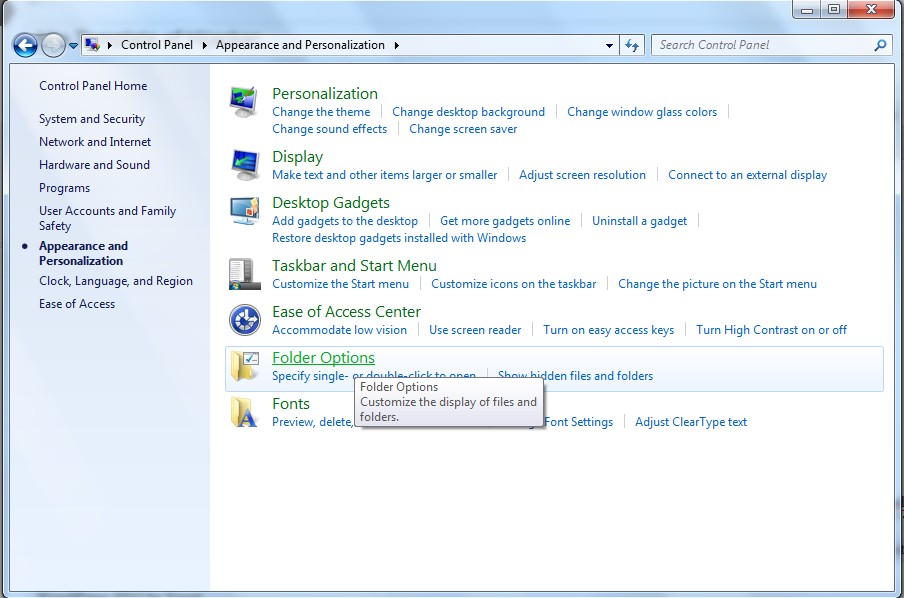
(4). Click on the View tab in the Folder Options window
(5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
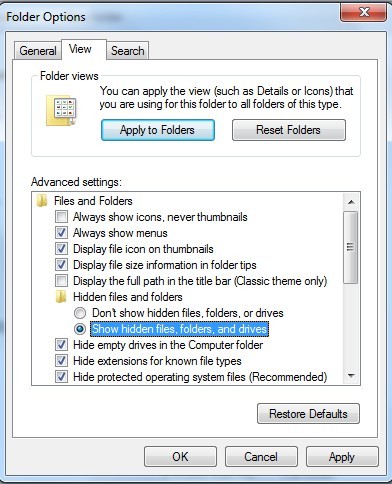
(6). Click OK at the bottom of the Folder Options window
*For Win 8 Users:
Press Win+E together to open Computer window, click View and then click Options
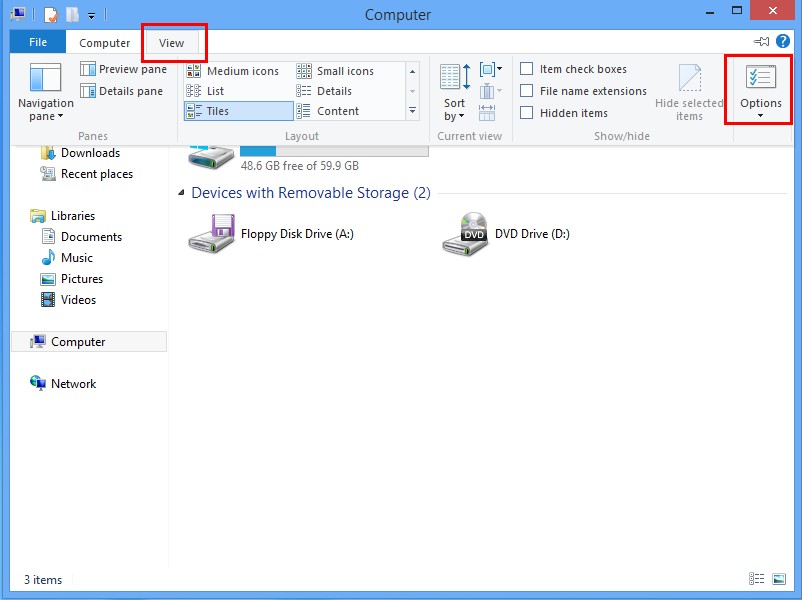
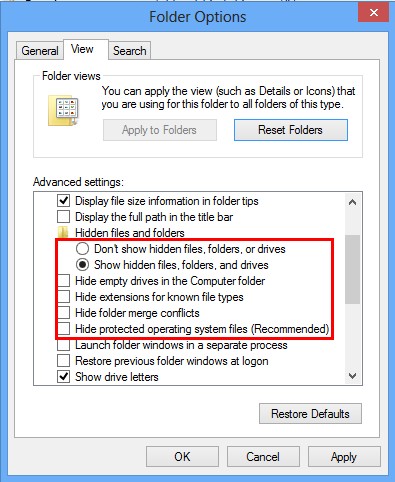
Click View tab in the Folder Options window, choose Show hidden files, folders, and drives under the Hidden files and folders category
3. Delete Relevant Registry Entries and Files
(1). Delete the registry entries of Trojan Exploit:JS/Dotcaf.A through Registry Editor
Press Win+R to bring up the Run window, type “regedit” and click “OK”
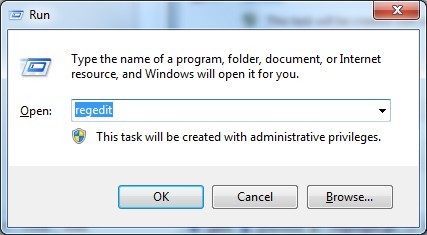
While the Registry Editor is open, search and delete the related registry entries
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Random’
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
(2). Find out and remove the associated files
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
%AllUsersProfile%\Application Data\~random
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
Exploit:JS/Dotcaf.A can make full use of the loopholes in the system to help other infections to intrude into the computer. It is created to collect your vital information for their own profit. Once installed, it is able to bundle with malicious codes in the system and facilitates the hacker to attack your computer secretly. In a word, it can make system become very vulnerable when it is active in the backdoor. And it is a vicious Trojan which can bypass antivirus programs to escape any detection and removal. Therefore the manual removal method proved to be a best way to completely get rid of the virus.
The above manual removal is quiet complicated, which needs sufficient professional skills to process. Therefore, only computer users with sufficient computer skills are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by on October 24, 2014 12:34 pm, last updated on October 24, 2014 12:48 pm



Leave a Reply
You must be logged in to post a comment.