You open the browser and Rvzr2-a.akamaihd.net jumps out all of a sudden? Or when you open a new tab in the browser, you see its pop-up advertisements without rhyme or reason? Then your computer is surely infected with this browser hijacker virus. Being redirected to some strange websites constantly and receiving a lot of advertisements are very annoying, but you do not know how to stop it? How to remove this browser hijacking virus so as to make your browser settings restore? If you have no clue, you can read this article.
No matter what you want to do with the browser, including searching for information and browsing websites, you often see Rvzr2-a.akamaihd.net or advertisements from it, which is really an annoying thing. This infection is specially designed to hijack user’s browser to reach the purpose of seeking profits. It keeps displaying a large number of advertisements as well as sponsorship links to tempt you to click so that its developers are able to acquire pay-per-click income. It has the ability to help other suspicious websites increase visiting traffics and collect sales leads for various vendors by monitoring user’s search habits. You should pay special attention when installing software since a lot of free software installation packages contain additional installs, such as this browser hijacker virus we are talking about. Therefore, you had better choose the custom installation so that you can refuse any unfamiliar optional software. If you always click Agree, you will invite it into your computer. That is why many users do not know how it gets into the computer without warning.
You do not know that Rvzr2-a.akamaihd.net installs in your computer successfully until you see it occupying your browser. The infection will also put banner advertisements on your visiting webpage showing the things you are interested in or you are searching for. Because it remains active state, a large number of computer resources are taken over, resulting in slow computer running speed. In addition, some cyber criminals whose purpose is unknown are able to make use of the loopholes it brings to invade your computer and take in everything you store in the computer in a glance. Its Rootkit capability makes it possible to go deep into the target computer system. Except modifying your browser settings, it modifies system settings, adds malicious registry entries and evades antivirus software, which brings great difficulty for users to remove it. Thus, if you want to get rid of troubles, you need to remove all the malicious files and registry entries it puts in the computer manually.
It is able to become the startup page of your web browser via modifying browser settings. Whether you are using Internet Explorer, Safari, Google Chrome, Mozilla Firefox or Opera, you can see the browser is occupied by it completely. It may also install plug-ins, extensions and toolbars in the browser so as to record your search history as well as cookies. Furthermore, since it is capable of redirecting you to some other strange sites containing dangerous viruses or trying to tempt you to download free software, adware or games, your network security is facing tremendous risks. Your computer is very likely to be infected with vicious malware, spyware, worms and Trojans. All of these harmful computer threats can be hidden in the system. By using large amount of system resources, the hijacker also reduces the performance of the system greatly .
This hijacker has the ability to change the default browser settings and redirect you to random sites (usually sites play unreliable advertisements or even contain virulent Trojan viruses, spyware and other infections). You may have noticed that most browser hijackers won’t be detected by antivirus programs. The same goes to this one. Its considerable visitor volume benefits numerous product manufacturers, freeware developers and website promoters, thus, they are willing to maintain long-term relationship with it. Actually, the main reason for the failure detection of antivirus programs is its successful disguise. Through making use of advanced technology, it maintains the ability to combine its components with system files or to generate fake system files, which confuses computer users as well as antivirus programs. They cannot identify it accurately and timely, let alone remove it thoroughly. Therefore, manual removal is the best choice to drive it away from your computer. In this case, you are advised to delete every file generated by it manually so as to spare all later trouble. The manual removal needs to be handled carefully so as to avoid any subsequent damages. Users can follow the manual guide here to have the hijacker removed instantly.
* Internet Explorer:
(1). Click Start, type: Manage browser add-ons
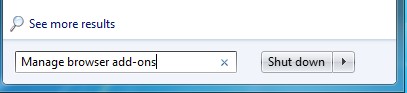
(2). Hit Enter on your keyboard
(3). Click Manage add-ons and disable all the suspicious add-ons
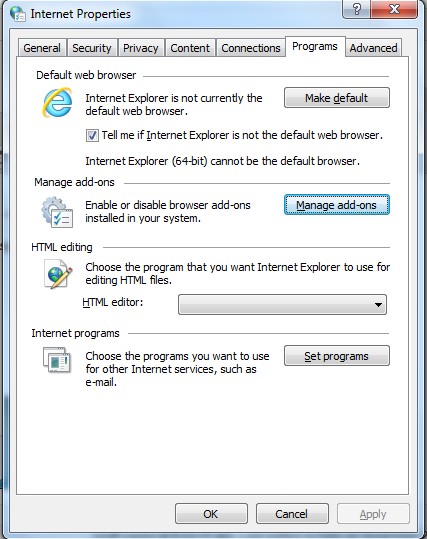
* Firefox:
(1). Click the Firefox menu and click Add-ons
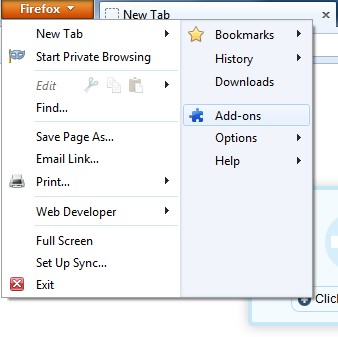
(2). Click Extensions, select the related browser add-ons and click Disable
* Google Chrome:
(1). Click the Customize and Control menu button → Tools → click Extensions
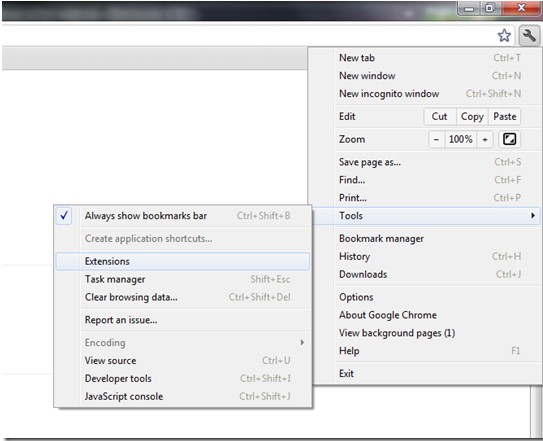
(2). Select the related Extension and click Disable
(1). Press Ctrl+Alt+Delete together to bring out Windows Task Manager, click Processes tab
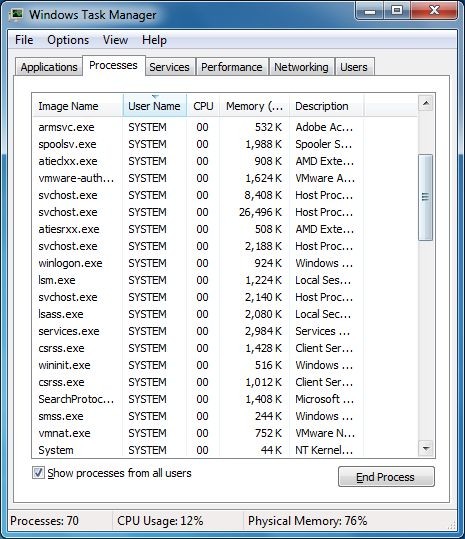
(2). Find out and end its processes
(1). Click on the Start button and then on Control Panel
(2). Click on the Appearance and Personalization
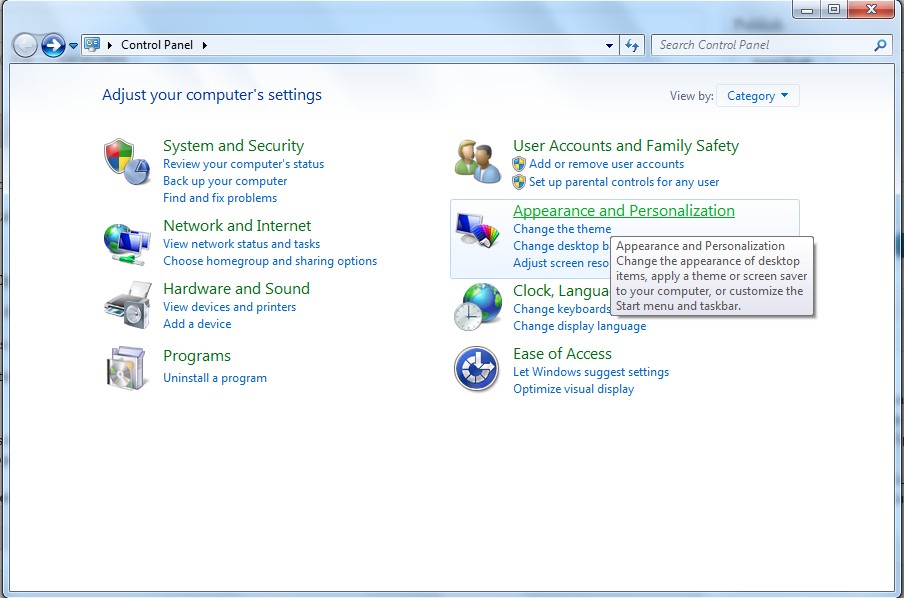
(3). Click on the Folder Options
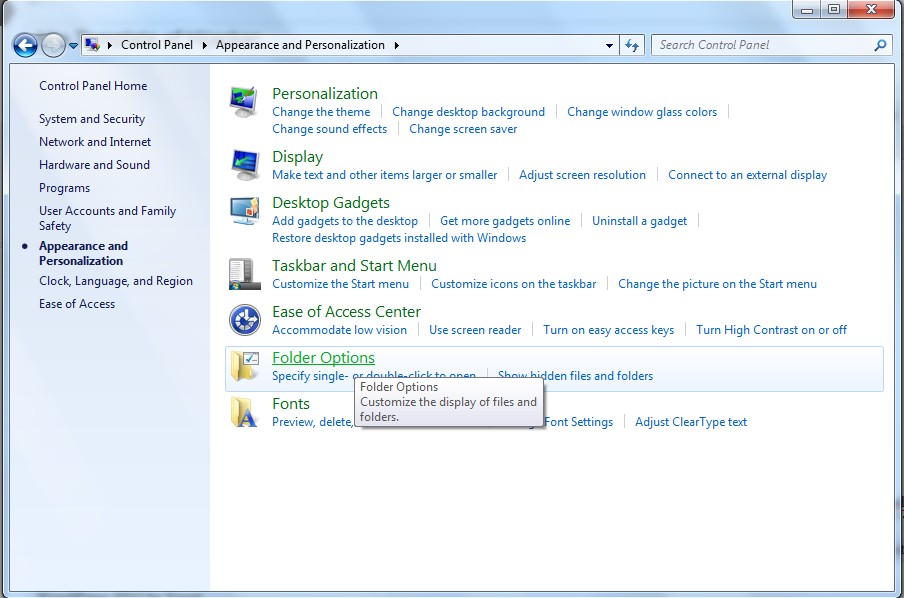
(4). Click on the View tab in the Folder Options window
(5). Choose the Show hidden files, folders, and drives under the Hidden files and folders category
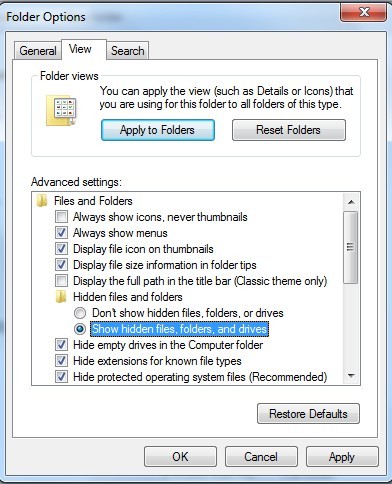
(6). Click OK at the bottom of the Folder Options window
(1). Delete the registry entries of Rvzr2-a.akamaihd.net through Registry Edit
Guides to open registry editor: Click “Start” menu, hit “Run”, then type “regedit”, click “OK”
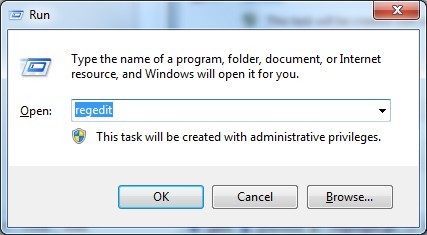
While the Registry Editor is open, search and delete its registry entries
(2). Find out and remove its malicious files in the system
You should know how the Rvzr2-a.akamaihd.net browser hijacker virus sneaks into your computer. You may install a free program that is bundled with it, such as a game package, fake system optimization software and an unknown video player. Users are advised to read the terms and conditions when installing programs into the computer. In order to expand the scope of influence, it has promoting agreements with many free programs. After the installation, it entangles your browser closely, which makes you feel very bored and powerless. If your computer has more than one browser (Internet Explorer, Firefox, Google Chrome or Opera), the virus will choose which browser it would like to infect (or infects all!) depending on your browser use habits and the security situation of the computer. It analyzes your browsing behaviors and promotes advertisements according to your preferences. What is worse, it makes the target computer vulnerable to remote attacks initiated by cyber criminals. Thus, you should have Rvzr2-a.akamaihd.net removed as early as possible.
The above manual removal is quite dangerous and complicated, which needs sufficient professional skills. Therefore, only computer users with rich computer knowledge are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by on December 11, 2013 5:53 am, last updated on December 12, 2013 6:56 am



Leave a Reply
You must be logged in to post a comment.