Exploit:Java/CVE-2013-2465 virus has been on many of my recent MSE scans and they never seem to get rid of it. My computer is running with Win 7 64x btw. It appeared within about a month or so. Is there any way I can remove this virus completely without coming back?
Exploit:Java/CVE-2013-2465 virus, as similar as Exploit.Java.CVE-2013-1493, is a typical detection for a JavaScript Trojan which can be found by Microsoft Security Essentials. It proliferates via a hacked website that hosts and advertises a malevolent Java applet exploiting the CVE-2013-2465 vulnerability. Generally speaking, this threat attacks PCs using a vulnerable version of Java. It can be used to download and install other malware infections onto the affected computer system.
When this virus is downloaded on your computer, it slows down the whole speed of the corrupted PC by adding large amount of worthless files to occupy the system resources. Thus, your PC may crash or react slowly, also some normal applications are hard to launch as they keep freezing. This kind of threat will open a doorway on infected computer to allow remote attacker to gain full access. That means your confidential information, for instance, credit card, login numbers could be sent to the hackers without consciousness. More than that, the visible symptom will keep annoying you because as soon as you log in Windows, a lot of constant pop ups will show on your screen and won’t allow you to close them. In a word, this pesky virus can mess up your system files and then lead to system damage, it should be removed as soon as possible.
a. There will be lots of annoying pop-up ads and fake security alerts;
b. It will block your access to the Internet and redirect everything you do on your browser to malicious web pages;
c. It will reduce your PC performance and create many junk files to wreak chaos;
d. Antivirus programs on the computer will automatically be shut down;
e. It may come with additional viruses and malware to further damage your computer;
f. Your private and critical information may be captured a remote host who will use them for Internet crimes;
Exploit:Java/CVE-2013-2465 Virus is able to disable antivirus programs so that it cannot even be detected or removed by antivirus programs, you need to manually remove it out of the computer. And in case that any mistake might occur and cause unpredictable damages, please spend some time on making a backup beforehand. Then follow these steps given as below:
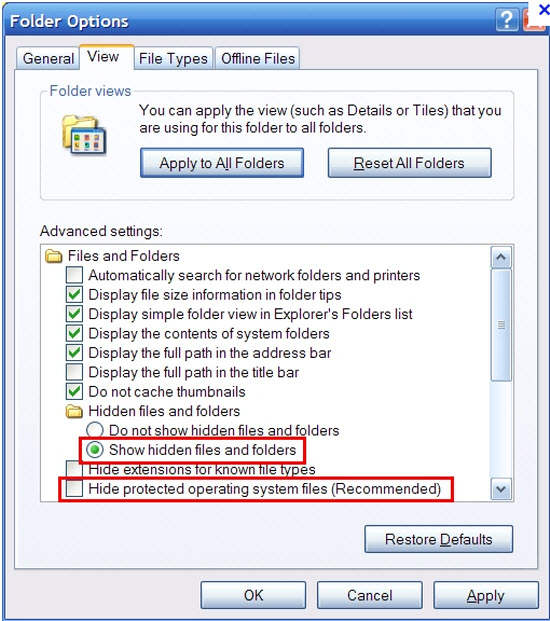
1. Show hidden files and folders.
Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
2. Open Registry entries. Find out the malicious files and entries and then delete all.
Attention: Always be sure to back up your PC before making any changes.
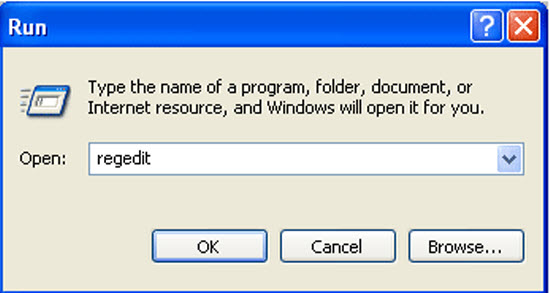
a. Press the “Start” button and then choose the option “Run”. In the “Open” field, type “regedit” and click the “OK” button.
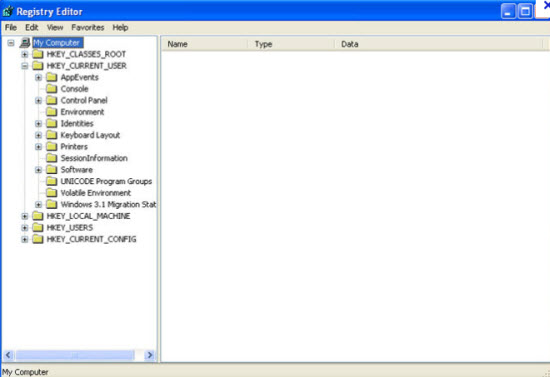
b. All malicious files and registry entries that should be deleted:
%AppData%\Protector-.exe
%Documents and Settings%\[UserName]\Application Data\[random]
%AllUsersProfile%\Application Data\.dll
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “net
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “[random].exe”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\”Shell”
Exploit:Java/CVE-2013-2465 Virus can carry out various harmful activities on the compromised computer such as slowing down dramatically, making your system crash randomly. When it is running in the background, you may see random files and folders created in your computer. Also numerous unexpected messages may come in front of you when you are working. You may get this virus when open the unknown email and click the strange link attached in it. The other situation you get it installed is when you download free applications and movies from the Internet. This threat is capable of capturing essential system resources as well as making process or application running unstable on the infected computer system. And the most importantly, it may collect sensitive details on the infected computer and transfer it to a remote cyber-crook. Therefore, it is highly recommend users to get rid of this Trojan as soon as it is detected.
Note: If you are confused with the manual guide above, please contact experts from Yoocare Online Tech Support for further help.
Published by on September 23, 2013 1:07 am, last updated on September 23, 2013 1:07 am



Leave a Reply
You must be logged in to post a comment.