Does your computer infect with W32/Ramnit.a? Do know what kind of virus it is? Is your security software being able to remove this Trojan Horse virus? Is it coming back over and over and you cannot find a way to get rid of it completely? Don’t be frustrated. If you are having a hard time in removing this virus, you can read the post below and aim yourself with manual removal method.
W32/Ramnit.a is being spread through internet and has infected uncountable computer via malicious links or pretending to be an innocent email attachment which contains Trojan installation packages. This Trojan horse virus is set behind attractive ads to fraud you click on it. The installation will be automatically started after clicking. We all know that this Trojan virus is categorized as a nasty virus which can infected all kind of operating system in your computer no matter you are using Windows XP, Windows Vista, Windows 7 or Windows 8. It is a newly created virus that aim with automatic injection so all programs which listed against user32.dll will be infected as soon as the system launches.
This virus usually gets into target system secretly without asking for the permission. That means you may not even notice its traits if you have clicked malicious link and intrude virus unwarily. It may permits to contact remote servers to download more harmful threats items to install into your system and enables hackers to use these to monitor the compromised computer remotely. Implementing harmful activities on the background and taking over the entire system should the first step it takes to infect your computer. Then your computer is acting more and more wired. You will be surprised at the times it crash or freeze after getting infected. If you don’t want the virus harm to both hardware and software component, removal is the best action you need to take.
W32/Ramnit.a is a malicious Trojan virus which can install itself into the computer system without your consent and awareness. It makes your computer work slowly and implants other nasty infections into the computer. To make things worse, this Trojan is a tool for the hacker to invade the infected computer to steal your information. It is recommended to remove it as quickly as possible. Users can follow the manual guide here to have this virus removed instantly.
(1). Click on the Start button and then on Control Panel
(2). Click on the Appearance and Personalization link
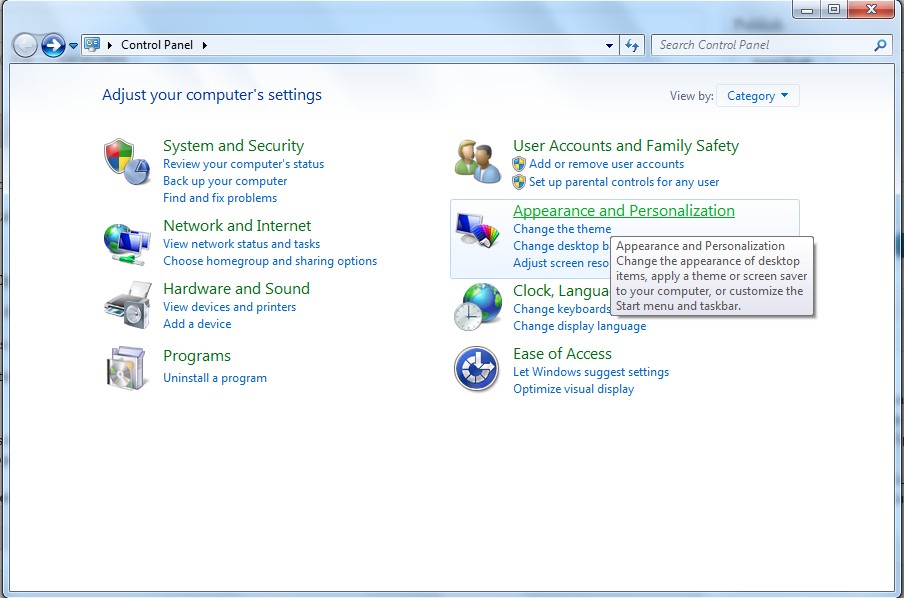
(3). Click on the Folder Options link
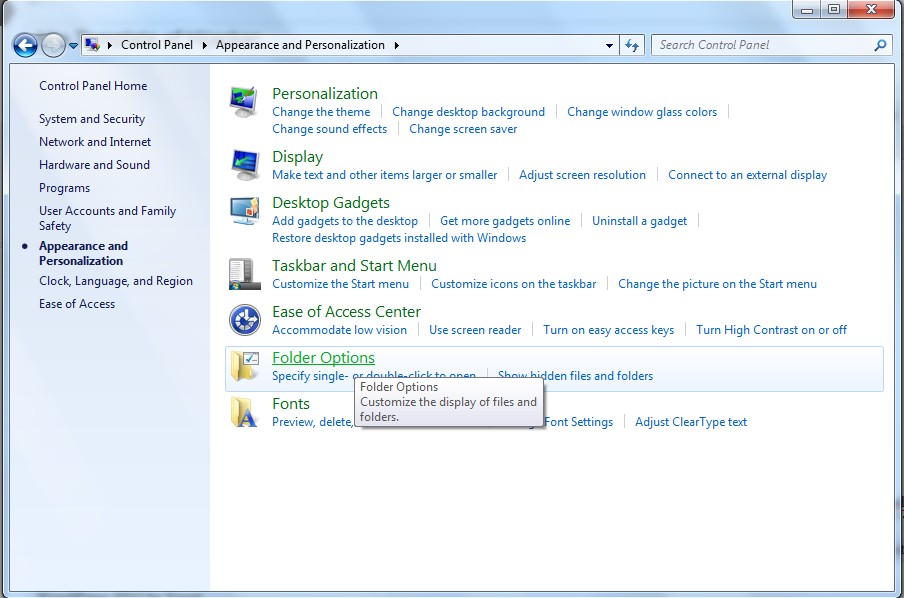
(4). Click on the View tab in the Folder Options window
(5). Choose the Show hidden files, folders, and drives under the Hidden files and folders category
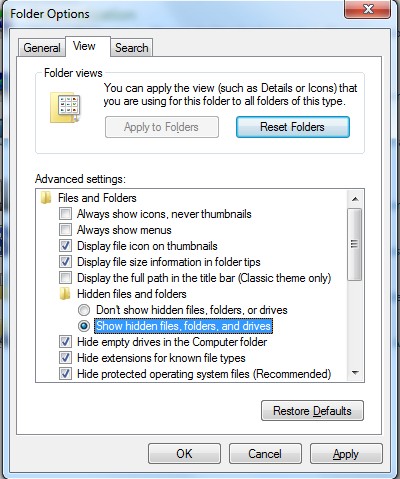
(6). Click OK at the bottom of the Folder Options window.
(1). Delete the related registry entries through Registry Edit
Guides to open registry editor: Click “Start” menu, hit “Run”, then type “regedit”, click “OK”
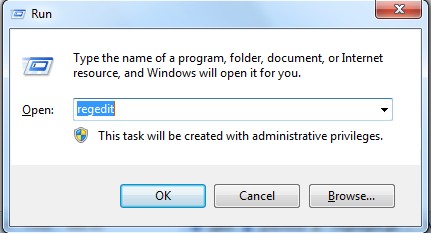
While the Registry Editor is open, search and delete the following registry entries listed below:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Random’
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
(2). Find out and remove the associated files of this Trojan virus.
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%AllUsersProfile%\Application Data\random
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
Generally speaking, being a stubborn Trojan horse like W32/Ramnit.a, its setting will be precisely created. This virus might change computer setting to permit remote server connection to download more harmful threats into the infected computer and also allow hackers remotely monitor the infected computer. Computer usually hard to use after such infection because RAM is almost full and programs are no responding at every steps. It also strives to log keystrokes that PC users typed in the infected account so that it can record down the browser histories and sensitive data. You need more time to active or open a program or file. Failure to remove it would cause hardware problem.
You can contact from YooCare Online Tech Support for further help if you still have no confidence on doing removal yourself.
Published by on September 21, 2013 4:06 am, last updated on September 21, 2013 4:30 am



Leave a Reply
You must be logged in to post a comment.