Help!!!Backdoor.Poison.bta is detected by anti-virus, but it keeps coming back when I restart my computer, can it be removed manually and completely? This post will show you the way to remove this virus completely.
Backdoor.Poison.bta is a current malware virus from the notorious Trojan horse family, which can terminate program running on the infected computer. This vicious Trojan is extremely difficult to remove via a normal anti-virus. It invades into the computer system via malicious websites, junk mails and even when you download mail attachments which are malicious nature. Once it is through to the PC, it copies itself to the start up code of the system in order to get started automatically whenever you log into the computer system.
In general, this virus will change system registry settings which enables itself to be activated automatically every time when you start the infected computer. It can exploit system vulnerability, which slows down the computer considerably. It is very annoying to spend a long long time on performing any task on the computer. Moreover, this Trojan is able to implant other malware and spyware into the infected computer, which will further destroy the system and even lead to system crash. What is worse, it is active in the background to facilitate cyber criminals to invade your computer. Your online traces and personal information may be recorded and you have no awareness of that. Thus, it is highly recommended to remove it as quickly as possible.
#The Trojan allows cyber criminals to visit your computer remotely without your consent.
#The Trojan is related to system crash and files fragmentation, and it can disable your executable programs.
#The Trojan redirects your specified websites to other harmful websites and changes your computer settings at random.
#It brings other types of threats to your computer such as malware, adware parasites and spyware.
#It records your browser history and computer data to violate your privacy and compromise security.
Malicious as the Trojan horse is, it takes your computer at great risk by damaging your system, files and programs. Also, this malicious Trojan corrupts your computer along with other types of threats like malware and spyware. Moreover, you will come across many unexpected troubles when surf the web, for example, the Trojan can redirect your web search results to hazardous contents. Even the best anti-virus software is also disabled and difficult to take effective to delete any type of viruses entirely. If you haven’t sufficient skills of handling with system files, please don’t delete anything that you are not sure. In this situation, manual removal is appreciated. Also, PC professionals online will help you delete the Trojan completely at a quick time.
Manual removal is a complicated and risky process, so please back up all important data before making any changes on your computer. Here are some instructions to handle with the Trojan horse manually, and be cautious when going through the following steps.
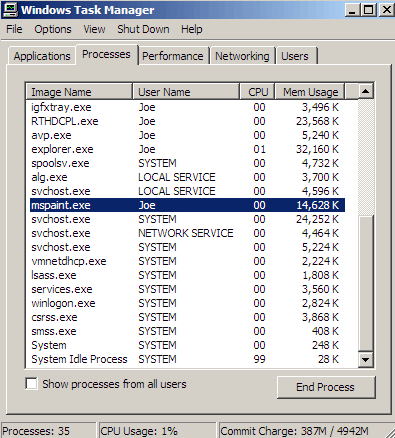
1. Press Ctrl+Alt+Del keys together and stop the virus processes in the Windows Task Manager.
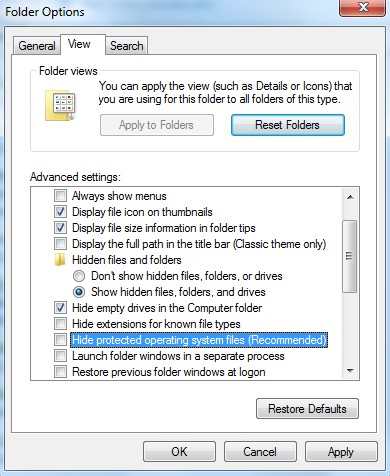
2. Go to Folder Options from Control Panel. Under View tab, select Show hidden files and folders and uncheck Hide protected operating system files (Recommended), and then click OK. Remember to back up beforehand.
3. Press Windows+ R keys and search for regedit in Run. Delete associated files and registry entries related to the virus from your PC completely as follows:
%AllUsersProfile%
%AllUsersProfile%\Application Data\~r
%AllUsersProfile%\Application Data\~dll
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “ ”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” = ’1′
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments “SaveZoneInformation” = ’0′
4. Reboot the computer normally to take effective, when the above steps are done.
In summary, Backdoor.Poison.bta is a dangerous Trojan virus that is extremely harmful to the computer. Running programs and even the computer will shut down automatically, which may damage the system or hard disk seriously. Besides, it facilitates the cyber criminals to access the infected computer in the backdoor. Your online traces are recorded and you know nothing. It activates automatically every time you start the computer. Thus, to protect your computer and your privacy, you shall remove this dangerous Trojan immediately.
Friendly Reminder:If you still find it hard to follow the removal guide above smoothly, please contact YooCare: PC experts 24/7 online.
Published by on June 25, 2013 5:52 am, last updated on June 27, 2013 8:08 am



Leave a Reply
You must be logged in to post a comment.