Got infected with Trojan Horse Generic 31.AYES and do not know how to remove it completely? Does your anti-virus software perform normally to delete the virus entirely? If not, how to delete this nasty virus successfully and completely? Learn from this post and follow removal guide below to remove the Trojan horse safely.
Trojan Horse Generic 31.AYES is categorizes as a dangerous virus such as Trojan Horse Backdoor generic15 BYNL that would mess up the infected computer. It usually sneaks into your computer though junk mail attachment, malicious pop-up or fishy website visiting. It can break out the security defense to link up with hacker for further illegal purpose such as track down your online behaviors, note down your bank account and password. It will also slow down your computer performance and poor network connection. It is a disaster to your computer due to its’ high degree of danger because it loads many evil progresses to run out of memory. This result usually leads to system frozen or crashed. It may permit to contact remote servers. Imaging that there is a criminal in your computer and watches every step on your daily network activities. So terrible!!
To be noticed, it is not only infect the computer by also usually comes with other dangerous malwares. For example, key logger, adware and even spyware. It opens a backdoor to download extra infections into the target PC and activates other malwares itself. As a result, computer resources are highly taken up and system sluggish to crash down from time to time. In a word, this nasty virus should be removed as soon as possible. Failure to remove it not only would result in possible damage to the windows operating system and your PC hardware components, also would increase the chance of letting cyber criminals take advantages of your stolen financial data. With such a terrible infection, there is no wonder why the computer are not able to run as normal as before. To remove such nasty virus, you should consider a way that both efficient and effective – manual removal.
Manual removal is a complicated and risky process, so please back up all important data before making any changes on your computer. Here are some instructions to handle with the Trojan horse manually, and be cautious when going through the following steps.
※ It will allow cyber-criminals to break into the infected computer without noticed
※ It disables executable program and cause system crash
※ It will change your registry settings and key value which makes it hard to be removed
※ It will display numerous fake infections of exaggerated security threats
※ It violates your privacy and records your data in the infected computer.
1. Press Ctrl+Alt+Del keys together and stop processes of this virus in the Windows Task Manager.
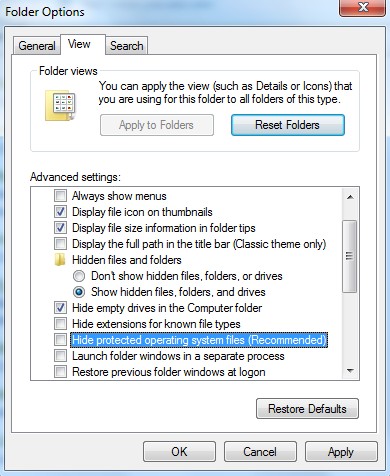
2. Go to Folder Options from Control Panel. Under View tab, select Show hidden files and folders and uncheck Hide protected operating system files (Recommended), and then click OK. Remember to back up beforehand.
3. Press Windows+ R keys and search for regedit in Run. Delete associated files and registry entries related to Trojan Horse Generic 31.AYES from your PC completely as follows:
%APPDATA%\[RANDOM CHARACTERS].js
%APPDATA%\[RANDOM CHARACTERS].pad
%USERPROFILE%\Start Menu\Programs\StartUp\runctf.lnk
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” = ’0′
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments “SaveZoneInformation” = ’1′
4. Reboot the computer normally to take effective, when the above steps are done.
Trojan Horse Generic 31.AYES, like the other members in Trojan family Trojan Horse Dropper.Generic8.AVYY, is a notorious virus that used by hacker to take advantages of PC users. It is a malignant infection that makes use of system vulnerabilities in target system and encourages remote attacking. With the help of it, cyber criminals can easily access to the infected system and execute many dodgy actions such as stealing private info and monitoring PC. It is made to compromise PC users’ rights and violates personal affair. It messes up the infected computer, breaks the rules plus interfer the daily life of the owner of the infected computer. If you ever notice it in your computer, remove it fast and completely!
Friendly Reminder: If you still find it hard to follow the removal guide above smoothly, please contact YooCare: PC experts 24/7 online will offer you the most effective tech support to remove infection completely.
Published by on June 12, 2013 12:12 pm, last updated on June 12, 2013 12:12 pm



Leave a Reply
You must be logged in to post a comment.