Does your computer keep detecting Rootkit.Win32.BackBoot.gen virus? What to do to get rid of this pesky virus even if your antivirus program fails to remove it? Learn more here to find out an effective manual guide to completely remove this Trojan horse now.
Rootkit.Win32.BackBoot.gen is categorized as a seditious Rookit that infiltrates your computer without your permission or knowledge with the use of security exploits. If you think this small virus is nothing to be worried about, you are completely wrong. Once installed, it can modify your system setting, disable antivirus program and display numerous annoying advertisements on your computer. This type of virus is designed to hide the existence of certain processes or programs from normal methods of detection and enable continued privileged access to a computer. It could be a disaster to PC users because it wreaks chaos on your PC as soon as it is downloaded.
It can provide an attacker with full access via a backdoor, permitting unauthorized access to your computer without your consent. This type of virus also captures your system, can easily steal your login and password details. It is hard to be detected or removed because it always conceals its presence by showing only legitimate process running on the system. In the background, it downloads and executes other malware, delivers advertisements to your computer, and even blocks programs from running. To sum up, users are recommended to remove this threat as quickly as possible to make sure that you terminate the infection completely and safeguard the system against similar intruders.
It can bypass the legit security tools and destroy your computer secretly.
It prevents you from opening some application because the files are corrupted.
It can make your browser redirected to all kinds of malicious websites.
It is able to allow remote hacker access the compromised system for illicit purpose.
Currently many computer users had the same experience that this virus couldn’t be removed by any anti-virus applications. So the manual approach is always required to combat this virus. And here is the step-by-step removal guide for all computer users.
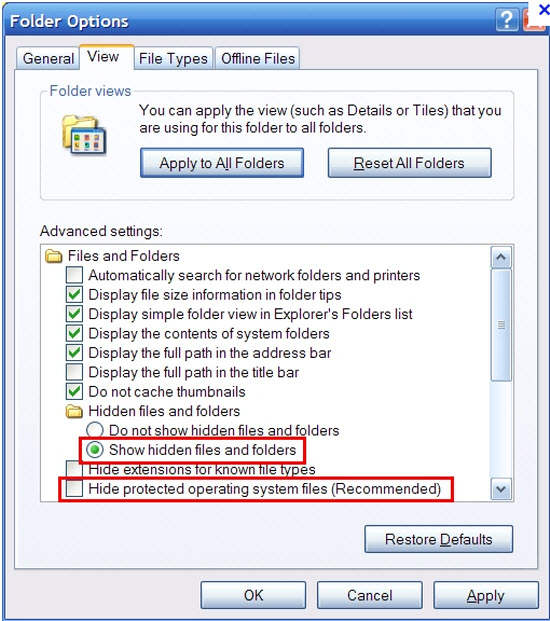
1. Show hidden files and folders.
Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
2. Open Registry entries. Find out the malicious files and entries and then delete all.
Attention: Always be sure to back up your PC before making any changes.
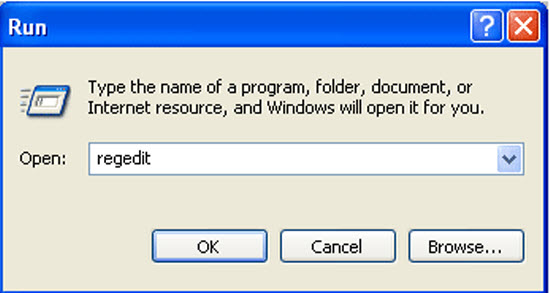
a. Press the “Start” button and then choose the option “Run”. In the “Open” field, type “regedit” and click the “OK” button.
b. All malicious files and registry entries that should be deleted:
%windir%\$NtUninstallKB<decimal number>
%APPDATA%\<hexadecimal string>
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Regedit
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “[RANDOM]”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “[RANDOM].exe”
Rootkit.Win32.BackBoot.gen is a tricky virus, it will hide itself on the background to escape from the detection by a legitimate antivirus program, also it will destroy and steal private confidential information from the infected system. Users always get this virus installed when they are clicking some malicious ads or visiting some malicious sites, as well as opening unknown downloaded files. If you have these activities online, then there may be a reason that you have this Trojan on your computer. No matter how did you get this virus, you must understand Rootkit.Win32.BackBoot.gen represents security risk for the compromised system and its network environment. You should have it deleted without any hesitation.
Important Notice: Manual removal always needs expertise. If you are afraid of making mistake during the removal, please contact experts from Yoocare Online Tech Support for further help.
Published by on June 3, 2013 4:14 am, last updated on April 3, 2014 7:07 am



Leave a Reply
You must be logged in to post a comment.