Have you got infected with W3i.IQ5.fraud? Do not familiar with this Trojan? How to delete this nasty Trojan successfully and completely? Learn from this post and follow removal guide below to remove the Trojan horse safely.
W3i.IQ5.fraud is a hazardous Trojan that PC user usually may get infected by clicking malicious attachment or unsafe link. It is dangerous because it can cause system frozen or crashed and steal sensitive user information to use them for illegal purpose. It changes computer settings, disables security programs and brings in other malicious malware. It will steal financial information and allow hackers remotely control the infected computer.
Generally speaking, W3i.IQ5.fraud is a tricky virus. It sneaks into computer system through vulnerable network channel. Once it is installed, it may change your desktop background and show various fake security messages. It prevents normal programs from taking effective by destroying them. This virus runs automatically when you turn the infected computer on. Then it hides behind system progress and starts to prepare for malicious intention. Once it infects the target system, it takes control of targeted computer quickly and degrades system performance to disable all the anti-virus programs and firewall. This would enable hackers to invade your computer. Later it permits hacker to contact remote servers to download more harmful threats items to install into your system and enables hackers to use these to monitor the compromised computer remotely. It can also destroy necessary system files, make the computer exposed to outer more severe threats. Also, it starts to collect confidential information such as email address, phone number, and credit card numbers and transfers to third party, leading to financial loss or privacy invasion. It is an annoying virus because it will disconnect internet frequently, hijack browses of the infected system and cause many unwanted programs on the computer. Thus, don’t hesitate to remove W3i.IQ5.fraud virus once it is found.
※ It will allow cyber-criminals to break into the infected computer without noticed
※ It disables executable program and cause system crash
※ It will change your registry settings and key value which makes it hard to be removed
※ It will display numerous fake infections of exaggerated security threats
※ It violates your privacy and records your data in the infected computer.
Manual removal is a complicated and risky process, so please back up all important data before making any changes on your computer. Here are some instructions to handle with the Trojan horse manually, and be cautious when going through the following steps.
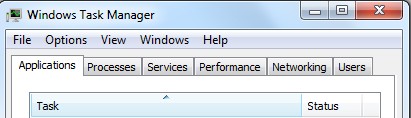
1. Press Ctrl+Alt+Del keys together and stop virus processes in the Windows Task Manager.
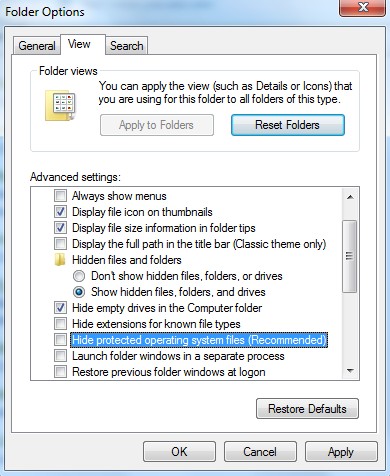
2. Go to Folder Options from Control Panel. Under View tab, select Show hidden files and folders and uncheck Hide protected operating system files (Recommended), and then click OK. Remember to back up beforehand.
3. Press Windows+ R keys and search for regedit in Run. Delete associated files and registry entries related to W3i.IQ5.fraud from your PC completely as follows:
%APPDATA%\[RANDOM CHARACTERS].js
%APPDATA%\[RANDOM CHARACTERS].pad
%USERPROFILE%\Start Menu\Programs\StartUp\runctf.lnk
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” = ’0′
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments “SaveZoneInformation” = ’1′
4. Reboot the computer normally to take effective, when the above steps are done.
This Video Shows You How to Safely Modify Windows Registry Editor:
In a word, W3i.IQ5.fraud is harmful to your computer. It will affect system and bring in other malicious software, key logger or Trojan into the target computer. It breaks through a security loophole, lessen the security level so that cyber criminals or hacker can easily remote control the infected computer. It will allow hackers to steal the information that puts all of the files and user info at high risk. When you detect it on your computer, remove it fast before it causes more financial lost or system damage on your computer.
Friendly Reminder: If you still find it hard to follow the removal guide above smoothly, please contact YooCare: PC experts 24/7 online will offer you the most effective tech support to remove infection completely.
Published by on March 31, 2013 7:30 am, last updated on March 31, 2013 7:31 am



Leave a Reply
You must be logged in to post a comment.