Have no idea of how to remove Win32/Lyposit.B Trojan Virus when you find that it appears in your computer? How dangerous would this Trojan virus be? All kinds of antivirus programs are able to catch it but cannot remove it completely. This post shows you the manual removal guide of Win32/Lyposit.B.
Win32/Lyposit.B is a destructive Trojan virus developed by hackers, which is capable of infecting your computer system and steals your confidential data via implanting more other malicious files and programs into your computer. Win32/Lyposit.B comes into your system through spam email attachments, unknown “Free” software or visiting malicious websites.
Once installed, Win32/Lyposit.B can modify important system files and Windows Registry settings, which will keep itself active in the background to allow hackers to intrude your computer system. The virus takes up high resources, considerably slows down your computer and even messes up your system. Moreover, it can drop many other threats into your computer, which make your computer vulnerable to remote attacks. Hackers monitor your online activities and collect your sensitive information including banking details or important social numbers for illegal use. Therefore, you should keep alert if you find it in your computer and remove it as soon as possible before it destroys your computer.
Win32/Lyposit.B is a tricky Trojan virus. Even though some antivirus software may block it temporarily, it will pop up again to scare you if it has not been removed completely. The hacker can easily access your system for he can change the antivirus settings after landing successfully on your system. It needs and only can be removed manually so that it is completely kicked off from your computer.
Win32/Lyposit.B is detected as a nasty Trojan horse and no antivirus software can block it completely. This stubborn Trojan horse hides deep in Win32 system files both in normal mode and safe mode with networking of Windows XP, Windows Vista and Windows 7.
1. Show hidden files
(1). Click on the Start button and then on Control Panel
(2). Click on the Appearance and Personalization link
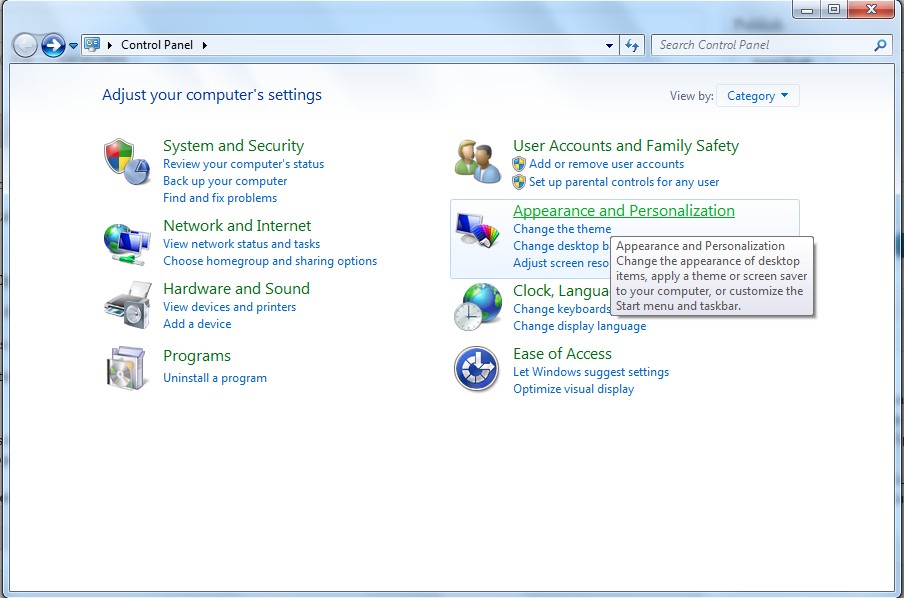
(3). Click on the Folder Options link
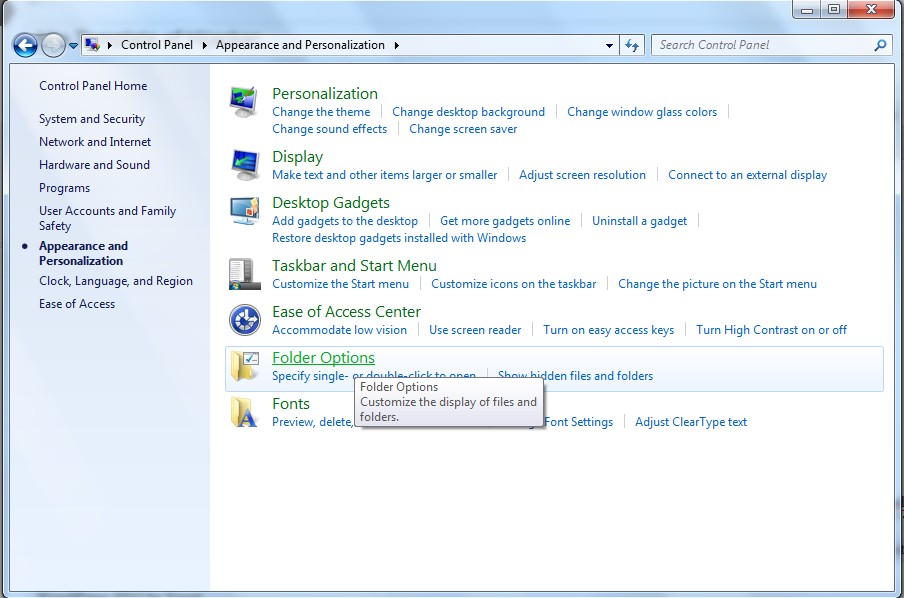
(4). Click on the View tab in the Folder Options window
(5). Choose the Show hidden files, folders, and drives under the Hidden files and folders category
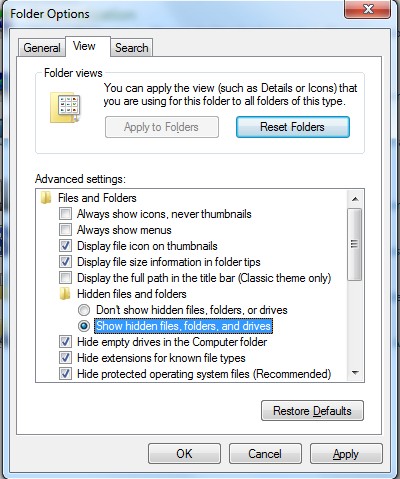
(6). Click OK at the bottom of the Folder Options window.
2. Delete virus files
(1). Delete the related registry entries to Win32/Lyposit.B virus through Registry Edit
Guides to open registry editor: Click “Start” menu, hit “Run”, then type “regedit”, click “OK”
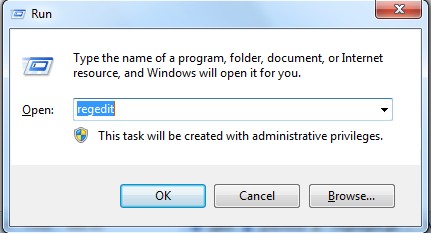
While the Registry Editor is open, search and delete the following registry entries listed below:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Inspector’
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
(2). Find out and remove the associated files of this Trojan virus.
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%AllUsersProfile%\Application Data\~
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “.exe”
In summary, Win32/Lyposit.B is a malicious Trojan virus which can install itself into the computer system without your consent and awareness. It is able to record your online activities and send them remotely to hackers. The Trojan virus makes your computer work slowly like a snail, simultaneously implant other nasty infections onto your computer. To make things worse, this Trojan is a tool for the hacker to invade your infected computer to steal your information including credit card, bank account information and individual privacy. We recommend you to remove it as quickly as possible to avoid further damages and losses.
If you have no idea how to do about that, please contact experts from YooCare Online Tech Support for further help.
Published by on December 13, 2012 12:06 am, last updated on June 11, 2013 7:21 am



Leave a Reply
You must be logged in to post a comment.