Unable to remove Rootkit.Boot.Pihar.c virus? Does your computer randomly reboot after being infected? Learn more to find out an effective removal guide to clean up this harmful virus immediately.
Rootkit.Boot.Pihar.c is a stealthy virus that can be installed without your permission. It allows cyber criminals to gain administrator-level access to the targeted computer system once it is downloaded. This virus tends to hide its presence on the compromised PC system so that it is particularly difficult to remove from a computer by running antivirus programs.
When it is running, the nasty Rootkit drops a lot of .TMP files in the Temp folder which will install the other malicious components damaging your system in the background. One of the victims said that after infected, the computer began to randomly reboot and give him a page fault or page not found type error message on the BSOD. In both safe and normal mode, he could login to the computer and use it anywhere from only 30 seconds-5 minutes, then the blue screen occurs. Like other Rootkits, it can display pop-up windows, severely disrupt the system, steal confidential information, relay it to a remote server, and perform other dangerous operations associated with the worst malware threats. Hence, users must remove this malware as soon as possible once upon detection.
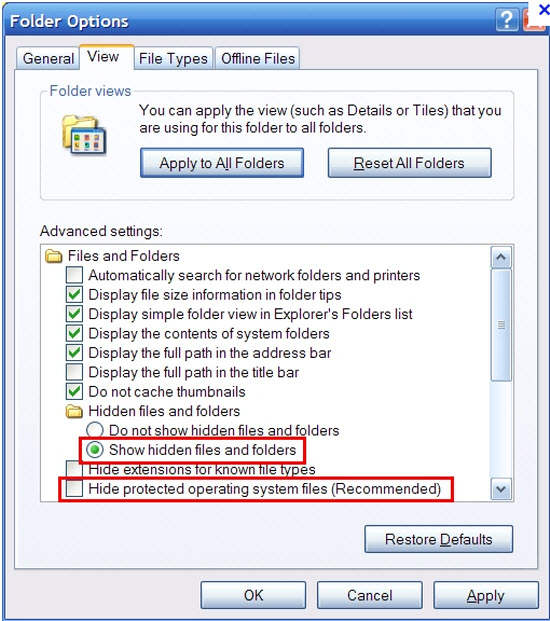
1. Show hidden files and folders.
Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
2. Open Registry entries. Find out the malicious files and entries and then delete all.
Attention: Always be sure to back up your PC before making any changes.
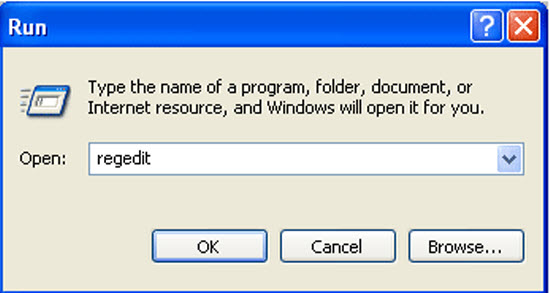
a. Press the “Start” button and then choose the option “Run”. In the “Open” field, type “regedit” and click the “OK” button.
b. All malicious files and registry entries that should be deleted:
C:\WINDOWS\system32\_VOID[RANDOM].dat
C:\WINDOWS\system32\uactmp.db
C:\WINDOWS\Temp\_VOID[RANDOM]tmp
C:\WINDOWS\_VOID[RANDOM]\
C:\WINDOWS\system32\UAC[RANDOM].db
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “net
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “[random].exe”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell
If you failed to remove this malware with the instructions above or need any assistant, you are welcome to contact YooCare experts to resolve all the problems completely.
Published by on July 26, 2012 7:09 am, last updated on July 26, 2012 7:09 am



Leave a Reply
You must be logged in to post a comment.