Rootkit.0access.H is a severe Rootkit Trojan that allows remote attackers to access and further control over the target computers with users’ permission. Once installed, it enables hackers to achieve continued privileged access to a computer while actively obscuring its invasion from victims by damage standard operating system functionality or other applications. Users always detect this virus by running Malwarebytes.
Rootkit.0access.H can access the kernel area of the system and embed their code. It disables all the antivirus protection tools and keeps performing its corrupted actions. The main purpose of this Rootkit is to allow intruders to come back to the compromised system later and access it without being detected. It aims to slow down your PC performance and download malicious files on the compromised computer on the background. Users always acquire this malware by visiting infected websites. On local networked computers, the virus will spread by infecting files on shared folders and drives. It may also spread through USB drives and other unsafe external devices. It is noted that this malicious virus will create a backdoor and connect to a remote server, allowing a remote attacker to gain control on the compromised computer. Victims should have it deleted in time once upon detection.
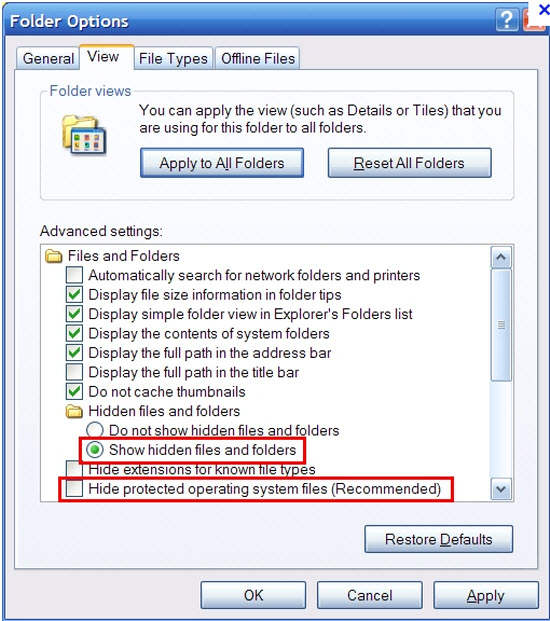
1. Show hidden files and folders.
Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
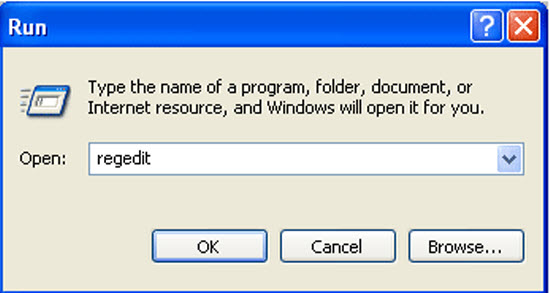
2. Open Registry entries. Find out the malicious files and entries and then delete all.
Attention: Always be sure to back up your PC before making any changes.
a. Press the “Start” button and then choose the option “Run”. In the “Open” field, type “regedit” and click the “OK” button.
b. All malicious files and registry entries that should be deleted:
%Documents and Settings%\[UserName]\Application Data\[random]
%AllUsersProfile%\Application Data\.exe(Rootkit.0access.H)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “net
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “[random].exe”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell
If you failed to remove this malware with the instructions above or need any assistant, you are welcome to contact YooCare experts to resolve all the problems completely.
Published by on July 16, 2012 8:02 am, last updated on July 16, 2012 8:02 am



Leave a Reply
You must be logged in to post a comment.