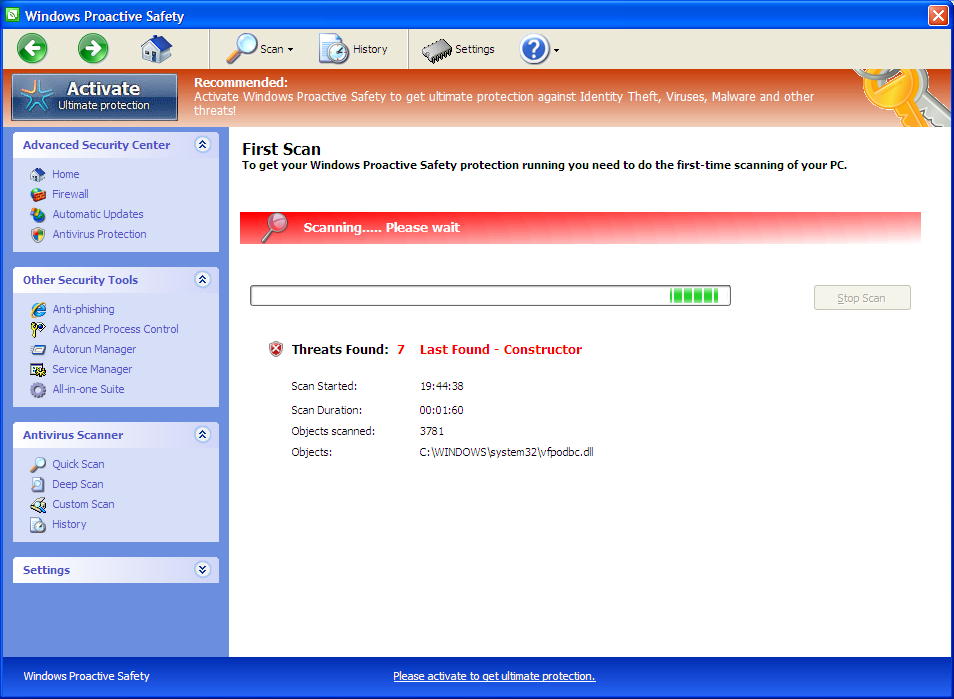
Windows Proactive Safety is classified as a fake security application among the FakeVimes family of rogue security programs. It is designed to scare unwary users into thinking their computer are at risk so as to extort their money. This program contains no legitimate anti-malware capabilities. Users should ignore the fake warning by this rogue program and take measures to remove it as soon as possible.
Undoubtedly, this rogue program can make chaos once it is on board. It gets installed on a user’s computer by using Trojan viruses that get downloaded from malicious websites. It will block any legitimate security programs already installed on the system which may lead to its removal first, then it begins to scan your computer, showing you lots of non-existent infection. You will be shown a lot of popups, nag screens and fake security alerts, that states that your computer is infected and offering to buy or activate the full version of the fake antivirus. In fact, all of these alerts and warnings are just a fake. Don’t be taken in. Windows Proactive Safety should be eliminated at once instead of being paid.

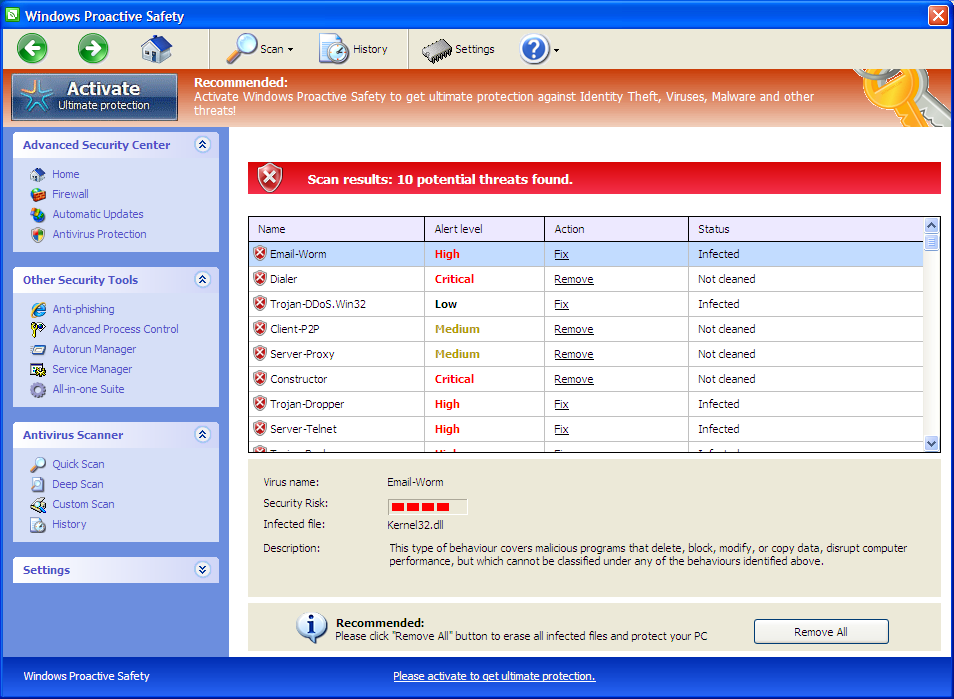
It can bypass the legit security tools and destroy your computer secretly.
It prevents you from opening some application because the files are corrupted.
It can make your browser redirected to all kinds of malicious websites.
It is able to allow remote hacker access the compromised system for illicit purpose.
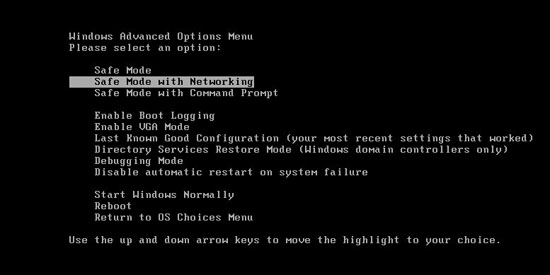
1. Reboot your computer to safe mode with networking. As your computer restarts but before Windows launches, tap “F8” key constantly.
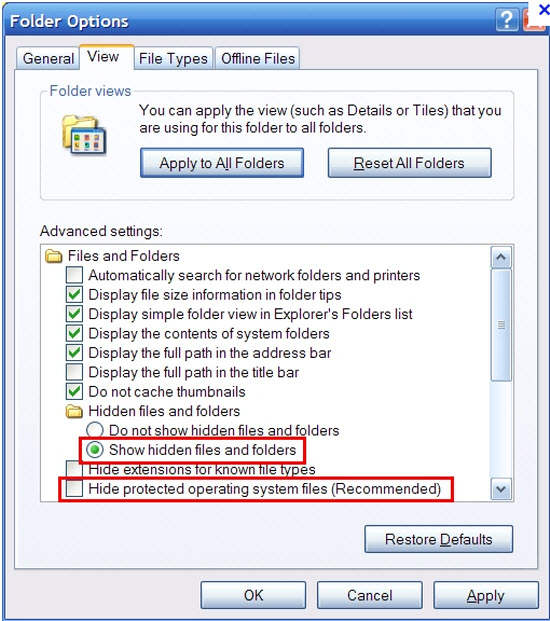
2. Show hidden files and folders.
Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
3. Open Registry entries. Find out the malicious files and entries and then delete all.
Attention: Always be sure to back up your PC before making any changes.
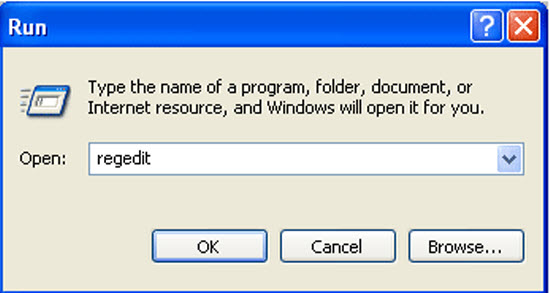
a. Press the “Start” button and then choose the option “Run”. In the “Open” field, type “regedit” and click the “OK” button.
b. All malicious files and registry entries that should be deleted:
%AppData%\Protector-[random].exe
%AppData%\result.db
%UserProfile%\Desktop\Windows Proactive Safety.lnk
%AllUsersProfile%\Start Menu\Programs\Windows Proactive Safety.lnk
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\
Inspector = %AppData%\Protector-[random].exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\a.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\aAvgApi.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\About.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\ackwin32.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ad-Aware.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\adaware.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\advxdwin.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdwarePrj.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\agent.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\agentsvr.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\agentw.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\alertsvc.exe\
Debugger = svchost.exe
HKEY_LOCAL_MACHINE\software\microsoft\Windows NT\CurrentVersion\Image File Execution Options\alevir.exe\
Windows Proactive Safety Virus Removal Guide is As Similar As Windows Maintenance Guard virus.
Manual removal of Windows Proactive Safety needs computer literacy, Please take cautions before performing the steps above. If you failed to remove this Malware, you are welcome to contact YooCare agents to fix the problem.
Published by on June 21, 2012 2:15 am, last updated on November 13, 2012 5:33 pm



Leave a Reply
You must be logged in to post a comment.