Because the computer operation speed becomes slow suddenly, you use the antivirus program to scan the entire system and you see Trojan.Ransom.ED in the scan result? Then you do not hesitate to click the Remove button of the antivirus program. But after restarting the computer, the performance still does not improve. You scan the computer once again and find that the Trojan virus is still there? In this case, what can you do to cast off its entanglement? This article has the information you want.
Trojan.Ransom.ED is a terrible Trojan virus. It has the ability to enter the computer secretly when you do not perceive and start malicious activities immediately. It makes full use of security vulnerabilities in Windows operating systems to attack computer initiatively. So far there have been many innocent computer users becoming its victims. In addition, your computer will be occupied if you visit a malicious web site, download a suspicious free program and open a spam email attachment. You do not know your computer is infected until your antivirus program gives you alerts.
Once installing itself in the computer successfully, Trojan.Ransom.ED begins to change system settings, simultaneously adding malicious files and registry entries to the target system forcedly, which makes it possible to avoid troubles and remain active in the backdoor to control the infected computer easily. Your computer will be very strange. The currently running program or even the computer will suddenly shut down without prior notice to you. You know, too many abnormal shutdowns can cause not only system damages but also hardware damages. It is also able to hide your important files, slow down the computer and even lead to system collapse. Moreover, other viruses will be injected into the infected computer, which will further damage the computer. With the extra help from these viruses, this Trojan can sleep without any anxiety. It is capable of monitoring your computer using traces and transmitting the gathered information back to the virus makers. No one can predict how they will deal with the information. Therefore, you must remove the Trojan horse as soon as possible since time is pressing. But it is hidden deeply in your computer by pretending to be a part of the system. The stiff antivirus programs are difficult to find out all its malicious components. Thus, manual removal is the most effective method.
1. It has the ability to download additional components and other infections in the target computer in order to fully complete its penetration.
2. It is able to cause system crash and destroy some of your programs in the infected computer.
3. It facilitates the virus makers to intrude your computer remotely without letting you know.
4. It is capable of collecting your browsing history and other private data.
The malicious Trojan.Ransom.ED can install itself into the computer system without your consent and awareness. It makes your computer work slowly and implants other nasty infections into the computer. To make things worse, this Trojan is a tool for the cyber criminals to invade the infected computer to steal your information. Through making use of advanced technology, it maintains the ability to combine its components with system files or to generate fake system files, which confuses computer users as well as antivirus programs. They cannot identify it accurately and timely, let alone remove it thoroughly. Therefore, manual removal is the best choice to drive it away from your computer. In this case, you are advised to delete every file generated by it manually so as to spare all later trouble. The manual removal needs to be handled carefully so as to avoid any subsequent damages. Users can follow the manual guide here to have the hijacker removed instantly.
1. End Relevant Processes
(1). Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab
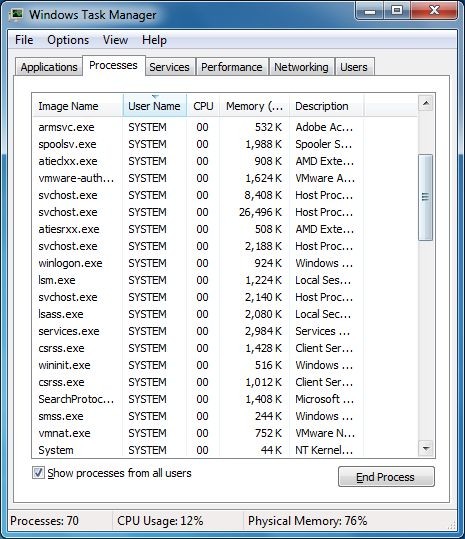
*For Win 8 Users:
Click More details when you see the Task Manager box
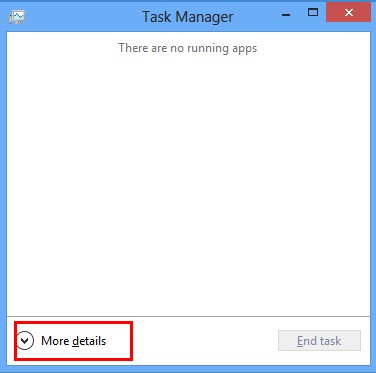
And then click Details tab
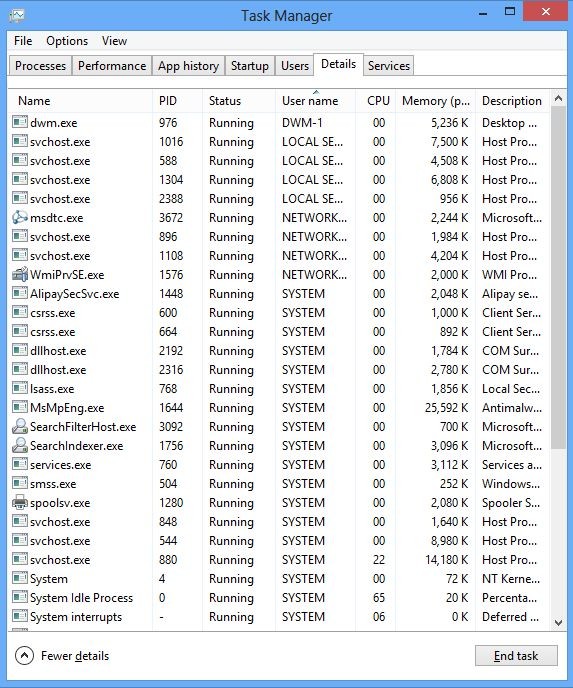
(2). Find out and end the processes of Trojan.Ransom.ED
2. Show Hidden Files
(1). Click on Start button and then on Control Panel
(2). Click on Appearance and Personalization
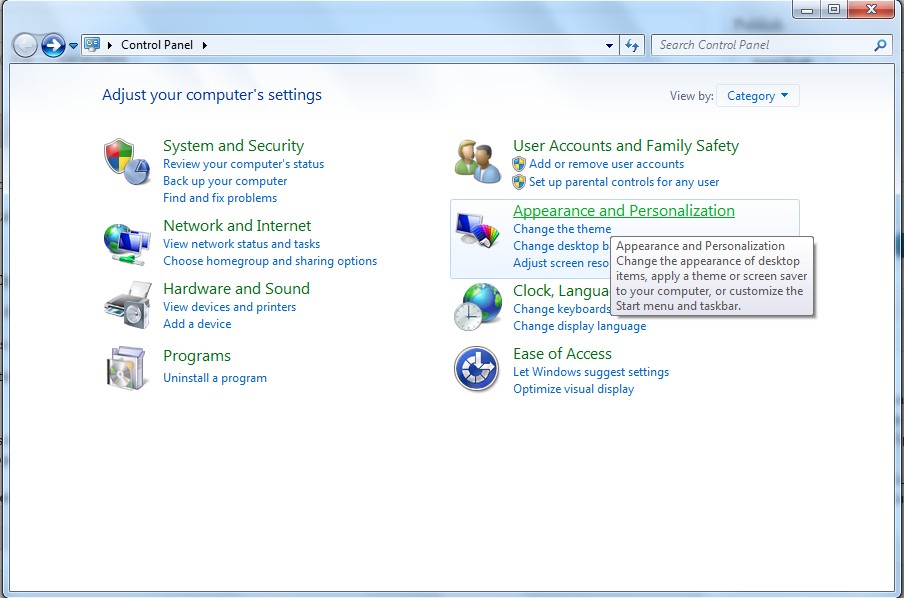
(3). Click on Folder Options
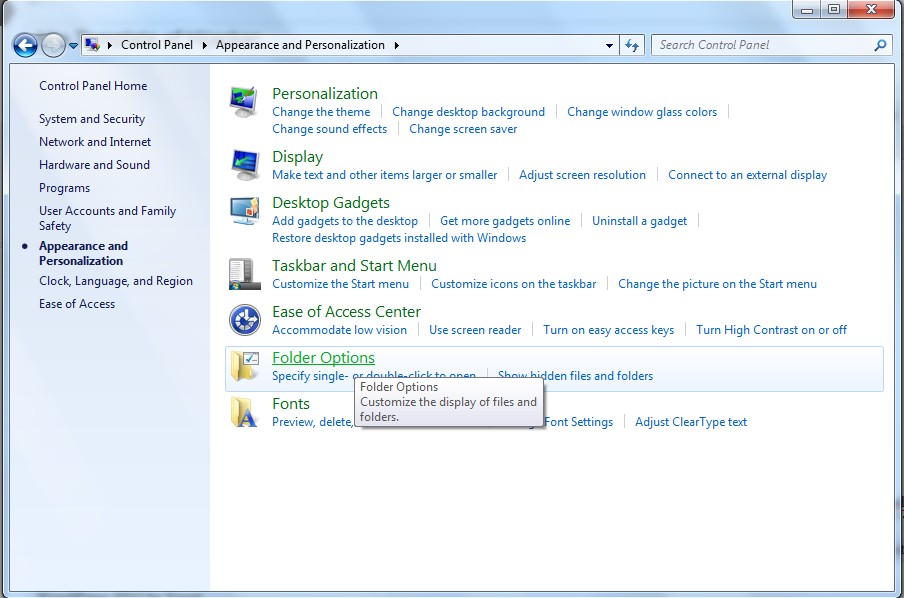
(4). Click on the View tab in the Folder Options window
(5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
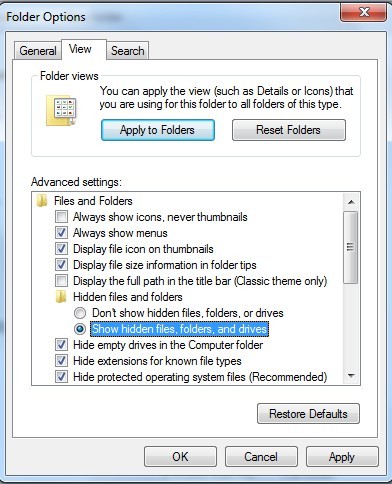
(6). Click OK at the bottom of the Folder Options window
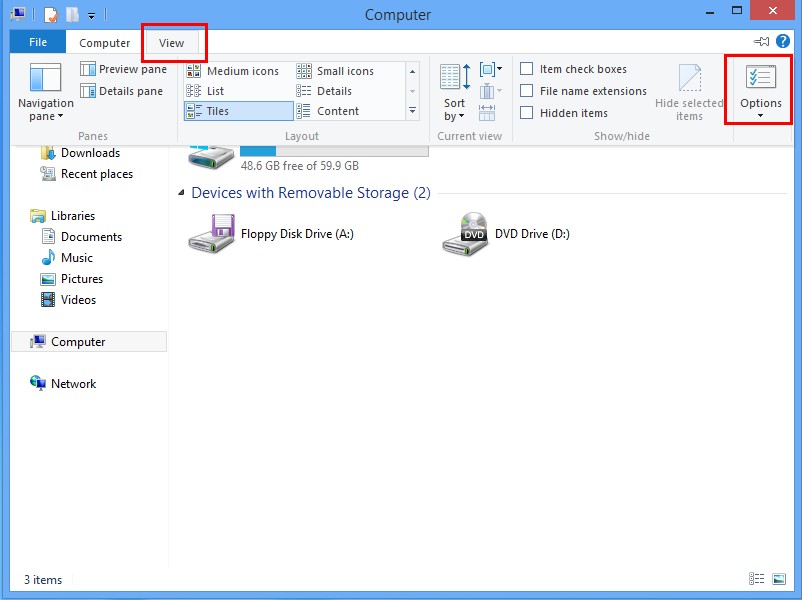
*For Win 8 Users:
Press Win+E together to open Computer window, click View and then click Options
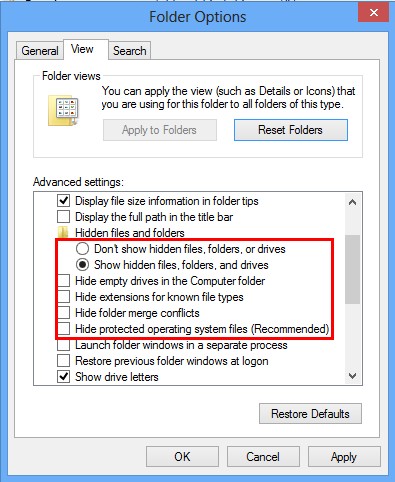
Click View tab in the Folder Options window, choose Show hidden files, folders, and drives under the Hidden files and folders category
3. Delete Relevant Registry Entries and Files
(1). Delete the registry entries of Trojan.Ransom.ED through Registry Editor
Press Win+R to bring up the Run window, type “regedit” and click “OK”
While the Registry Editor is open, search and delete the related registry entries:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
(2). Find out and remove the associated files.
%AllUsersProfile%\random.exe
%AllUsersProfile%\Application Data\~random
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
In short, Trojan.Ransom.ED is a very nasty Trojan horse virus that can mess up your computer seriously. It will help cyber criminals to steal your financial information as well as collecting your contacts’ email addresses so as to send them spam emails or even viruses in your name. The result cannot be imagined if cyber criminals collect and use your personal information illegally. It also leads to blue screen of death and other computer problems, preventing you from using the computer normally. You should eliminate this threat as soon as possible. Even if it cannot be completely removed by the antivirus software, you can also take manual removal.
The above manual removal is quite dangerous and complicated, which needs sufficient professional skills. Therefore, only computer users with rich computer knowledge are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by & last updated on January 2, 2014 10:39 am



Leave a Reply
You must be logged in to post a comment.