TR/Sirefef.BC.7 is classified as a highly dangerous Trojan which is designed to mess up the infected machine and notably slow down computer performance. It can be attached to email attachments, programs you have downloaded, or even from your computer’s operating system vulnerabilities. As soon as it is installed, users will have a nightmare since this virus has many bad performance like decreasing overall PC performance and resulting in Internet connection issues.
After breaking into the target computer by exploiting software vulnerability, it will apply an advance technique that aims to conceal itself and evades anti-virus detection. It also slows the system down, displays misleading alerts, redirects users to the hacked pages and does other malicious activities. Are you surprised that how you get this virus installed? Many trojans are distributed by e-mail, through file sharing networks and online chats (such as ICQ, AIM or IRC). They arrive in files attached to e-mail and instant messages, come embedded into letters or get downloaded using peer-to-peer applications. Users should never look down upon this tiny virus. It can open backdoor to let rogue programs and other viruses like the U.S. Department of Homeland Security scam installed on your computer, causing a fatal trouble. What makes users nervous is a Trojan will create a backdoor and connect to a remote server, allowing a remote attacker to gain control on the compromised computer. It is suggested users to remove TR/Sirefef.BC.7 as soon as once upon detection.
a. There will be lots of annoying pop-up ads and fake security alerts;
b. It will block your access to the Internet and redirect everything you do on your browser to malicious web pages;
c. It will reduce your PC performance and create many junk files to wreak chaos;
d. Antivirus programs on the computer will automatically be shut down;
e. It may come with additional viruses and malware to further damage your computer;
f. Your private and critical information may be captured a remote host who will use them for Internet crimes;
Currently many computer users had the same experience that this virus couldn’t be removed by any anti-virus applications. So the manual approach is always required to combat this virus. And here is the step-by-step removal guide for all computer users.
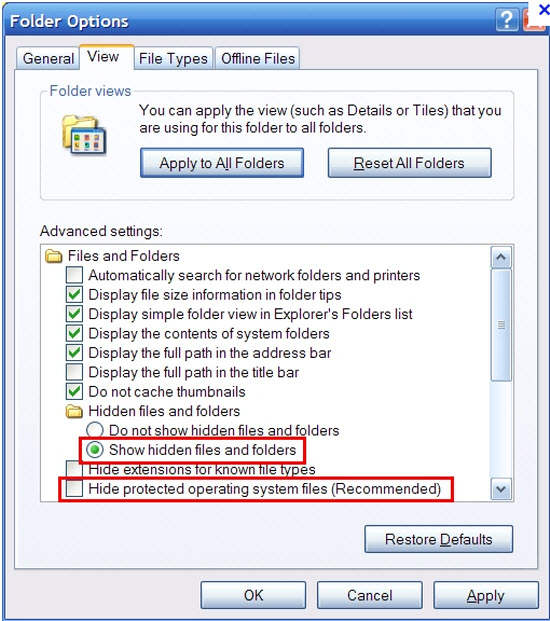
1. Show hidden files and folders.
Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
2. Open Registry entries. Find out the malicious files and entries and then delete all.
Attention: Always be sure to back up your PC before making any changes.
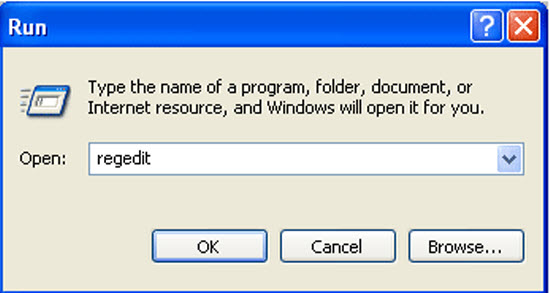
a. Press the “Start” button and then choose the option “Run”. In the “Open” field, type “regedit” and click the “OK” button.
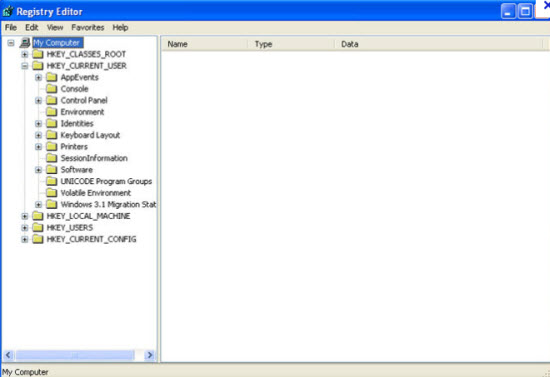
b. All malicious files and registry entries that should be deleted:
%AllUsersProfile%\Application Data\.dll
%AllUsersProfile%\Application Data\.exe(random)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “[RANDOM]”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “[RANDOM].exe”
TR/Sirefef.BC.7 is classified as a harmful Trojan virus that sneaks into your computer when they are visiting harmful contents, reading spam emails or downloading free items from infected websites carelessly. Once installed, it specializes in infecting various instant messengers and stealing user confidential information. By using its keystroke logging technique, TR/Sirefef.BC.7 easily steals user passwords and captures private conversations. This information is written into a log file, which is then sent to the hacker. It runs high risk for all the compromised computers. Therefore, we can see this horrible Trojan is only designed for performing a lot of different destructive actions that should be removed as soon as possible.
Published by on September 26, 2012 12:43 pm, last updated on June 7, 2013 6:43 am



Leave a Reply
You must be logged in to post a comment.