Does your computer suffer from Exploit.CVE-2014-1761.Gen virus? You have tried a lot of methods but still cannot get rid of it? And even your antivirus software fails to catch up with this annoying infection? In fact, it should be removed manually rather than wasting valuable time searching for free but useless antivirus software.
Exploit.CVE-2014-1761.Gen is classified as a very complex computer virus, because it can bypass the protection of the antivirus to get into the computer secretly without letting you know and bring you constant pain. This hateful virus designed by hackers who have good computer skills is able to damage your computer as well as collect valuable information for illegal interests. Therefore, it should be removed as soon as possible. You will suffer more if you let it stay in the computer for a long time.
More specifically, Exploit.CVE-2014-1761.Gen has the ability to bring the following effects: 1) it can record your online activities and can be used by the cyber criminals to acquire your important information; 2) it can help more viruses, malware and spyware to get into your computer through the creation of system defects; 3) it can also delete the important files and registry keys in the computer system; 4) the system stability will be threatened. Therefore, there is no doubt that you should get rid of the hateful virus from your computer as soon as possible to avoid any unnecessary damages.
1. It has the ability to download additional components and other infections in the target computer in order to fully complete its penetration.
2. It is able to cause system crash and destroy some of your programs in the infected computer.
3. It facilitates the virus makers to intrude your computer remotely without letting you know.
4. It is capable of collecting your browsing history and other private data.
Because the antivirus software cannot deal with Exploit.CVE-2014-1761.Gen successfully, manual removal is the most effective way to deal with this stubborn virus. Manual process ensures a complete remove but it also needs a better computer skills. The following are some manual steps for you:
1. End Relevant Processes
(1). Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab
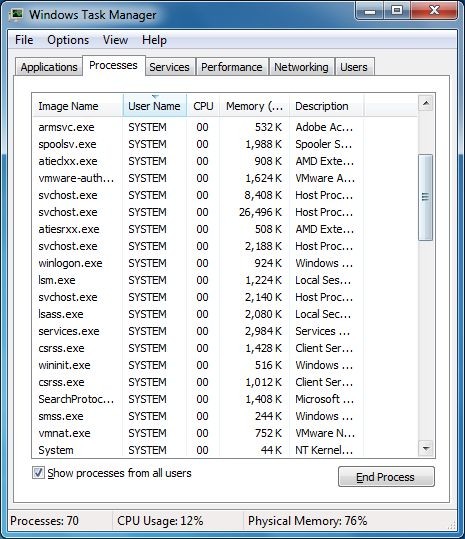
*For Win 8 Users:
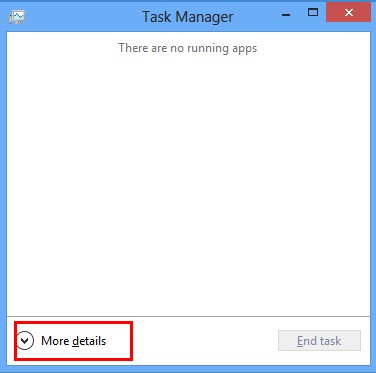
Click More details when you see the Task Manager box
And then click Details tab
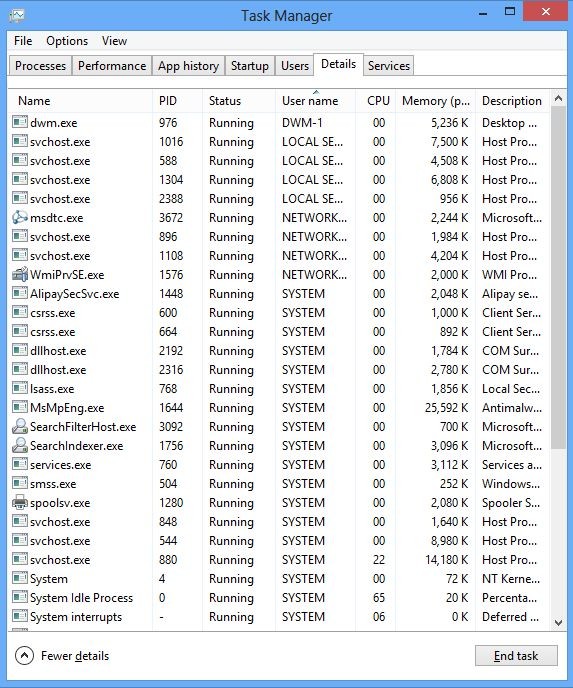
(2). Find out and end the processes of Exploit.CVE-2014-1761.Gen
2. Show Hidden Files
(1). Click on Start button and then on Control Panel
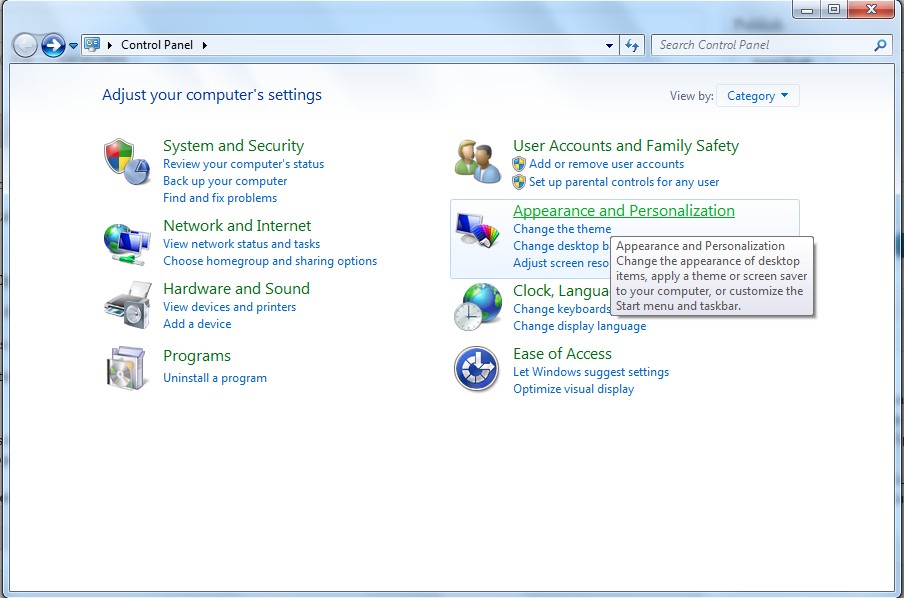
(2). Click on Appearance and Personalization
(3). Click on Folder Options
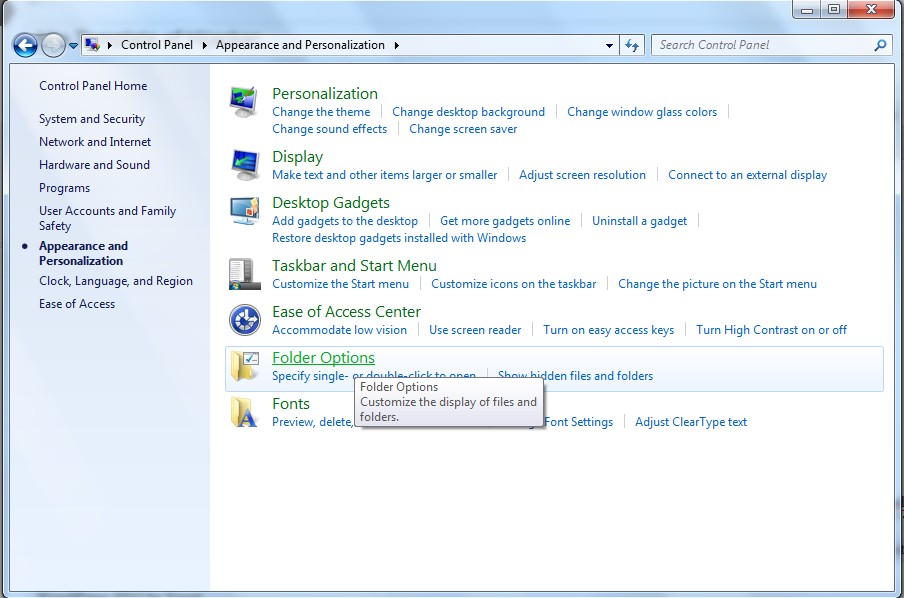
(4). Click on the View tab in the Folder Options window
(5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
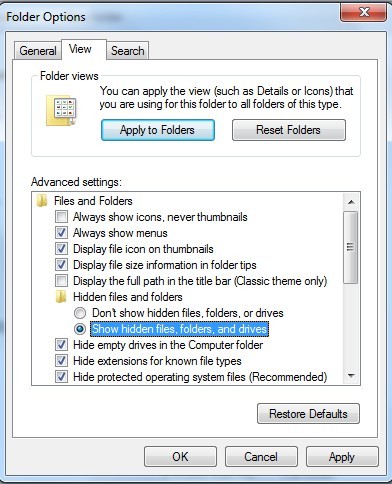
(6). Click OK at the bottom of the Folder Options window
*For Win 8 Users:
Press Win+E together to open Computer window, click View and then click Options
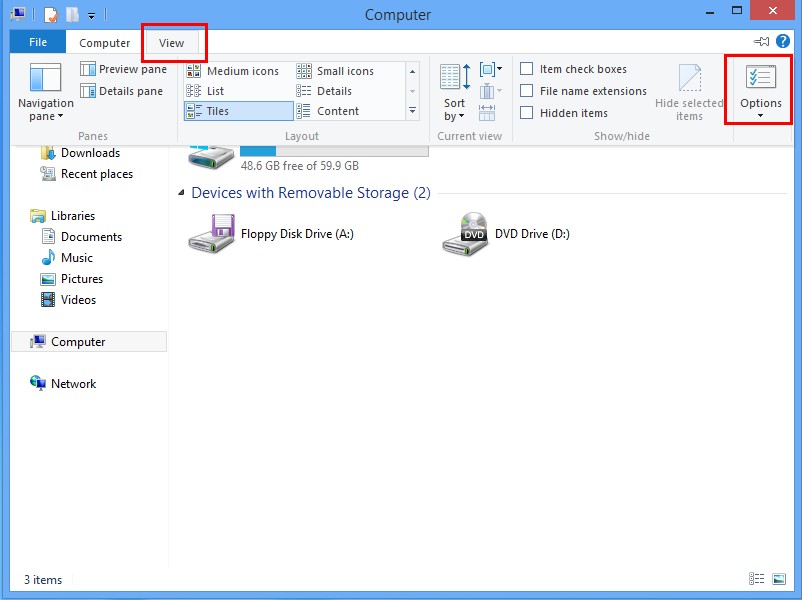
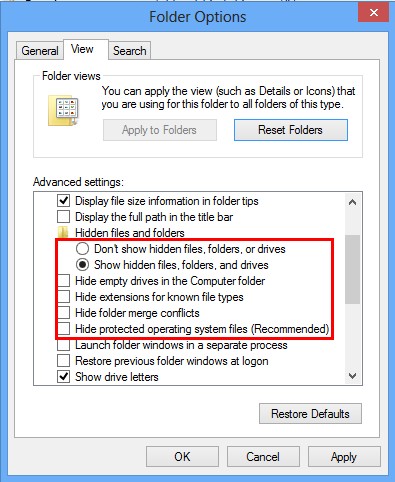
Click View tab in the Folder Options window, choose Show hidden files, folders, and drives under the Hidden files and folders category
3. Delete Relevant Registry Entries and Files
(1). Delete the registry entries of Exploit.CVE-2014-1761.Gen through Registry Editor
Press Win+R to bring up the Run window, type “regedit” and click “OK”
While the Registry Editor is open, search and delete the related registry entries
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
(2). Find out and remove the associated files
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
As mentioned before, Exploit.CVE-2014-1761.Gen is able to bypass the antivirus protection. Why? We can find the answer from one of the consequences. The most dangerous factor of this Trojan virus is to allow the third party to access the fragile system and record all the computer using traces as well as personal information. Therefore, the hacker will need to block the antivirus software. Because this kind of infection can be widely disseminated through the network, you should be careful when using the Internet. Accessing suspicious web sites, opening junk email attachments or downloading unknown free software can give this tricky infection a chance to enter the computer. Once we find that the computer is infected with it, we should take immediate actions to remove it as early as possible.
The above manual removal is quite dangerous and complicated, which needs sufficient professional skills. Therefore, only computer users with rich computer knowledge are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by on July 13, 2014 6:09 am, last updated on July 13, 2014 6:11 am



Leave a Reply
You must be logged in to post a comment.