Is there a security warning about Trojan.Win32.Inject.gzuj constantly popping up on your computer? What is it doing on your computer? Is it an unstoppable Trojan by antivirus software? If it is not removed from your computer, will you lose your important data and personal files? What is the best way to get rid of the Trojan completely?
As a vicious Trojan, Trojan.Win32.Inject.gzuj is able to detect system vulnerabilities and then lead off an attack. Whatever way it uses to get in the computer, destructive activities will be implemented right after it successfully settles down on the infected computer. By cleaning its logs, it is able to bypass the antivirus programs since antivirus programs cannot identify its key part. As the Trojan always has the ability to modify the default system settings, it will disable all system protection software and tools brazenly in order to avoid being removed. In this case, the virus wins the chance to weaken the system and make it vulnerable to other threats. As a result, a growing number of other Trojan horse, worms and malware can easily sneak into the computer to make things worse.
Hiding in the infected computer, Trojan.Win32.Inject.gzuj makes many computer users encounter more and more exceptions in the system. It is capable of making some changes in the system registry, resulting in a lot of dysfunction symptoms. For example, this disgusting Trojan will damage or delete important registry entries, which causes system failure or disordered system. Missing some important registry files, the system will face more terrible problems like not being able to start properly, easy to get stuck and a large number of pop-up system errors. All the chaos together will drive many computer users crazy for they do not know how to deal with the terrible mess. It is noted that the ultimate goal of the Trojan is to steal information which is useful for the virus makers. The collected information may be personal information, login credentials and online whereabouts. All of these data will be made use of by the virus makers in the generation of money. The Trojan needs to be removed as soon as possible to protect your computer and personal information.
1. It has the ability to download additional components and other infections in the target computer in order to fully complete its penetration.
2. It is able to cause system crash and destroy some of your programs in the infected computer.
3. It facilitates the virus makers to intrude your computer remotely without letting you know.
4. It is capable of collecting your browsing history and other private data.
The malicious Trojan.Win32.Inject.gzuj can install itself into the computer system without your consent and awareness. It makes your computer work slowly and implants other nasty infections into the computer. To make things worse, this Trojan is a tool for the cyber criminals to invade the infected computer to steal your information. Through making use of advanced technology, it maintains the ability to combine its components with system files or to generate fake system files, which confuses computer users as well as antivirus programs. They cannot identify it accurately and timely, let alone remove it thoroughly. Therefore, manual removal is the best choice to drive it away from your computer. In this case, you are advised to delete every file generated by it manually so as to spare all later trouble. The manual removal needs to be handled carefully so as to avoid any subsequent damages. Users can follow the manual guide here to have the hijacker removed instantly.
1. End Relevant Processes
(1). Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab
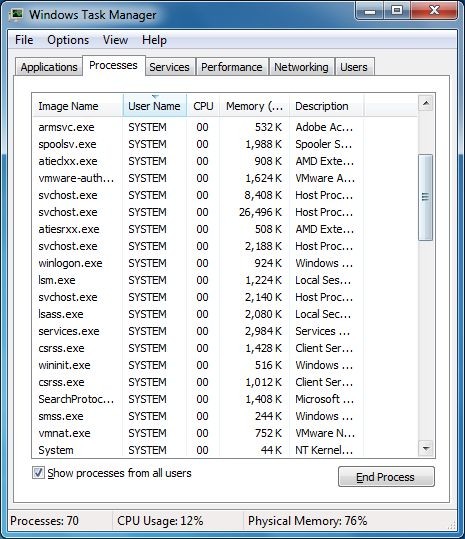
*For Win 8 Users:
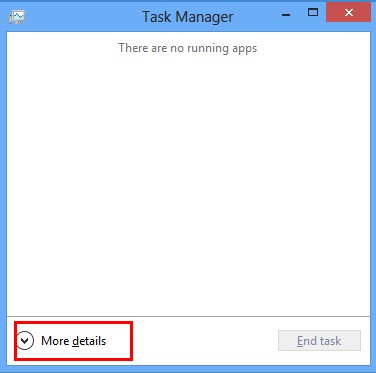
Click More details when you see the Task Manager box
And then click Details tab
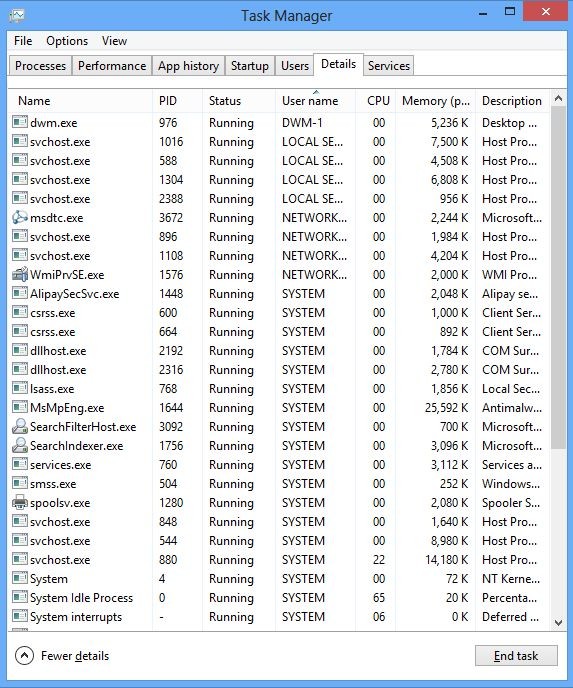
(2). Find out and end the processes of Trojan.Win32.Inject.gzuj
2. Show Hidden Files
(1). Click on Start button and then on Control Panel
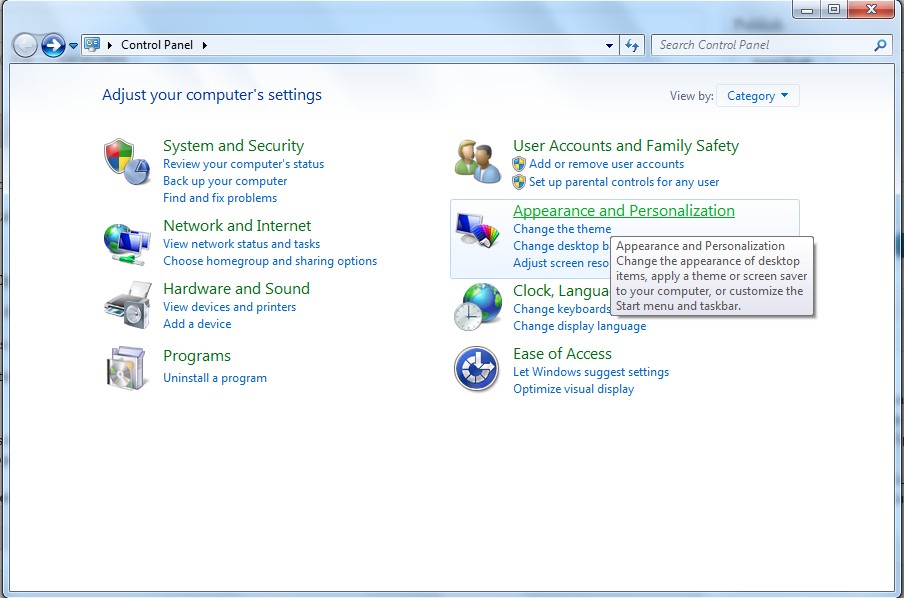
(2). Click on Appearance and Personalization
(3). Click on Folder Options
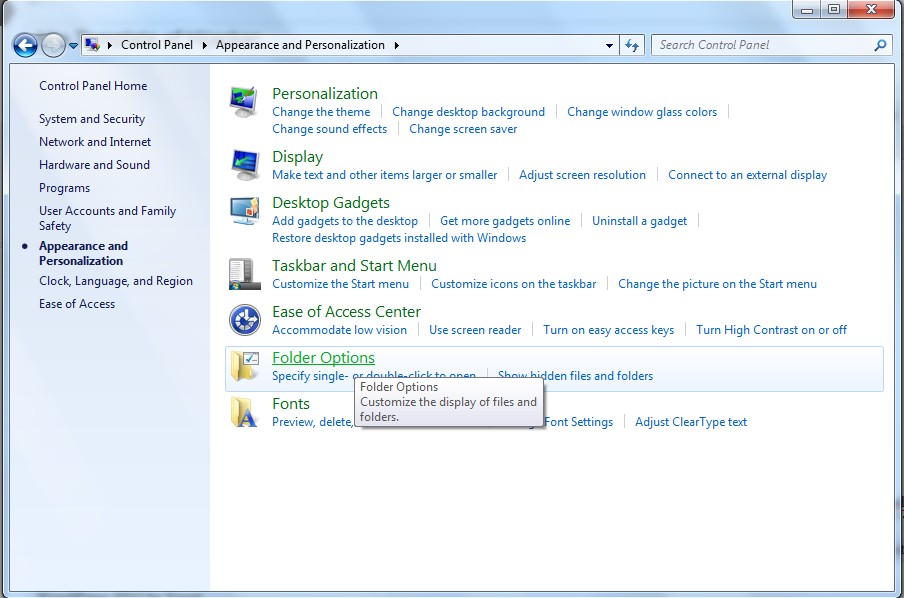
(4). Click on the View tab in the Folder Options window
(5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
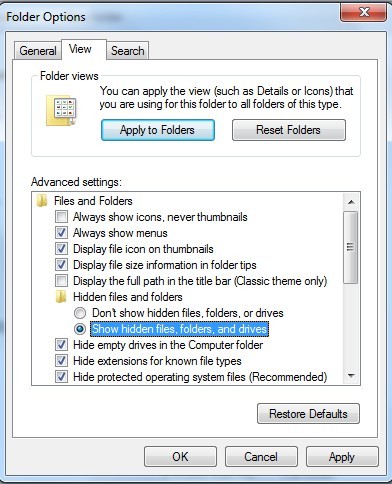
(6). Click OK at the bottom of the Folder Options window
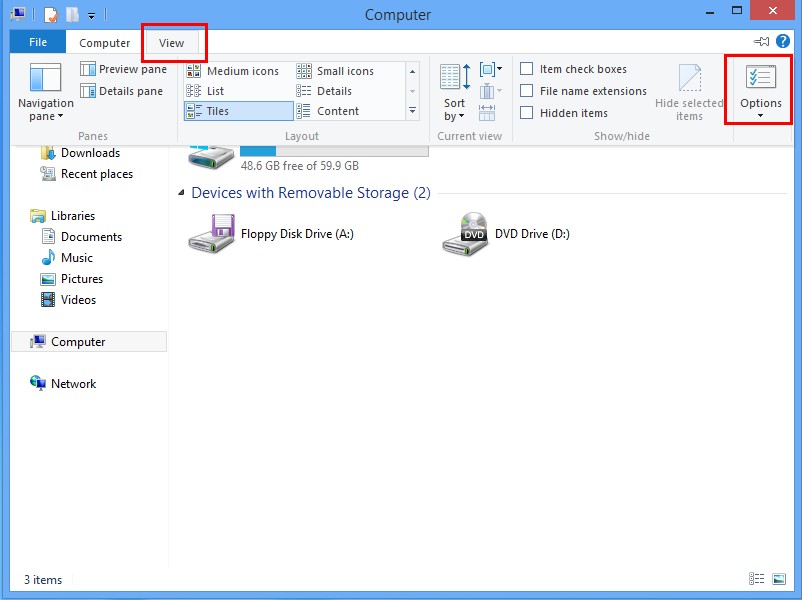
*For Win 8 Users:
Press Win+E together to open Computer window, click View and then click Options
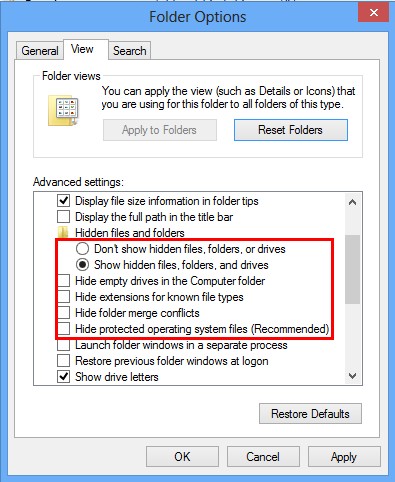
Click View tab in the Folder Options window, choose Show hidden files, folders, and drives under the Hidden files and folders category
3. Delete Relevant Registry Entries and Files
(1). Delete the registry entries of Trojan.Win32.Inject.gzuj through Registry Editor
Press Win+R to bring up the Run window, type “regedit” and click “OK”
While the Registry Editor is open, search and delete the related registry entries
(2). Find out and remove the associated files
Trojan.Win32.Inject.gzuj is considered as a harmful Trojan virus, which has so many cunning tricks to deceive ignorant computer users and invade their system secretly. It is able to perform a lot of furtive movements in the background so as to destroy the defenseless computer gradually. It is a good helper for the cyber criminals. With this nasty Trojan in the system, cyber criminals can remotely control the target computer and cause unpredictable damages. As a result, innocent users’ online activities are monitored all the time. Cyber criminals will use the opportunity to record the user’s confidential information such as login passwords, online banking account details, ID number and other financial transactions, which is not just invasion of privacy, but also a potential risk of losing personal assets. Therefore, it is imperative to immediately remove Trojan.Win32.Inject.gzuj.
The above manual removal is quite dangerous and complicated, which needs sufficient professional skills. Therefore, only computer users with rich computer knowledge are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by on February 18, 2014 12:14 pm, last updated on February 18, 2014 12:14 pm



Leave a Reply
You must be logged in to post a comment.