Exploit:Win32/Pdfjsc.AU Virus infection on my new laptop. AVG warns me this Trojan horse but don’t have the ability to remove it completely, my friend suggests me remove this virus manually but I have no idea how to do that. Is there a brief guide that I can follow? Any help will be appreciated.
Exploit:Win32/Pdfjsc.AU is a malicious Trojan horse that can infect All the Windows OS including XP, Vista, 7 and 8. PC users may get this virus when they visit unsafe webpage or download and install the programs. Once they are attacked by this Trojan horse, Some suppose that they can remove this threat by their security tools, however, most of the advanced anti-virus programs are not able to get rid of it completely because Exploit:Win32/Pdfjsc.AU can change its name and position once it has been installed successfully. This virus can cause a great damage on the infected PC PC users ignore this virus infection. It is suggest that PC users should remove this nasty virus process immiediately and manually.
 Generally speaking, this Exploit:Win32/Pdfjsc.AU will cause terrible damage on the infected system. Not only can it change system settings like desktop image, homepage and default browser but also bring other viruses from the malicious sites. PC users will suffer browser hijack redirect, rogue program and even the malware after being attacked by Exploit:Win32/Pdfjsc.AU Trojan horse. This Trojan horse virus has been a top virus on the Internet, it needs to be removed completely before it causes further damage.
Generally speaking, this Exploit:Win32/Pdfjsc.AU will cause terrible damage on the infected system. Not only can it change system settings like desktop image, homepage and default browser but also bring other viruses from the malicious sites. PC users will suffer browser hijack redirect, rogue program and even the malware after being attacked by Exploit:Win32/Pdfjsc.AU Trojan horse. This Trojan horse virus has been a top virus on the Internet, it needs to be removed completely before it causes further damage.
How did you get Exploit:Win32/Pdfjsc.AU virus on your computer? Usually these kinds of the viruses will be planted to some programs especially free programs, .exe, .bat or other executable processes and unsafe links. The computer will get the virus infection when the PC users install, open or click on these infected files. Sometimes the virus can even attack the computer by the files on the USB stick as well. Most of the unsafe website and forum will contain the virus infection, the computer can be infected while visiting these webpages.
Generally speaking, this virus can cause terrible virus infection on the infected computer like running slowly and even computer crashing. Once this virus has been installed to the computer, PC users will have to spend a long time opening programs or turning on the infected machine. It keeps taking over the high resource of the CPU and attacking the anti-virus program, other threats can be downloaded automatically from the unsafe website as well. What is worst, the cyber criminals have ability to remote control the infected PC due to this dangerous virus, all the information is in a high-risk of being stolen, the whole computer won’t be safe anymore.
The Trojan horse virus is an extremely dangerous threat on the infected computer. Registry and other system settings can be modified by it completely, that is the reason the nasty redirect virus can escape the tracking of the security tools like anti-virus program or firewall. It is strongly suggested that PC user should get rid of this Trojan horse virus in a manual way to remove it. Learn more from the manual removal guide below.
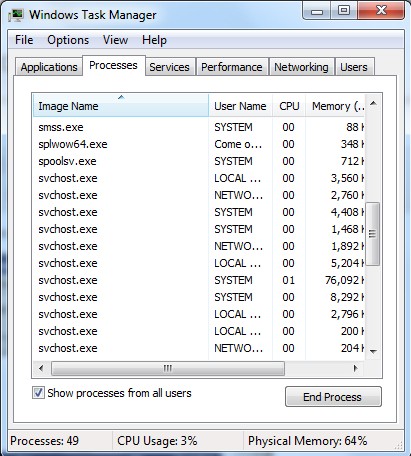
1. Press Ctrl+Shift+ESC keys together and stop virus process in the Windows Task Manager.
(The name of the virus process can be random)
2. Show hidden files and folders.
a. For XP: Press Win+E together, click on Tools, then choose Folder Options
For Vista, 7 and 8: Press Win+E together, click on Organize, then choose Folder and search options.
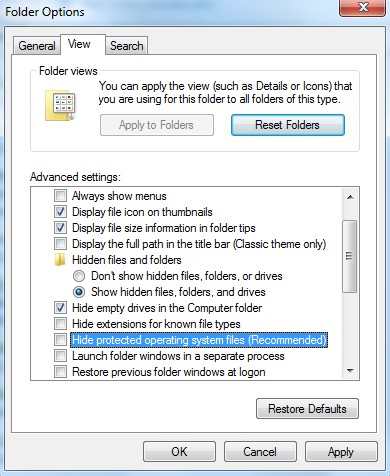
b. Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
3. Open Registry entries. Find out the malicious files and entries of the virus and then delete all.
Attention: Always be sure to back up your PC before making any changes.
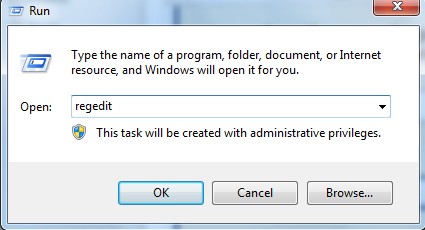
a. Press Win+R to get the Run window. In the “Open” field, type “regedit” and click the “OK” button.
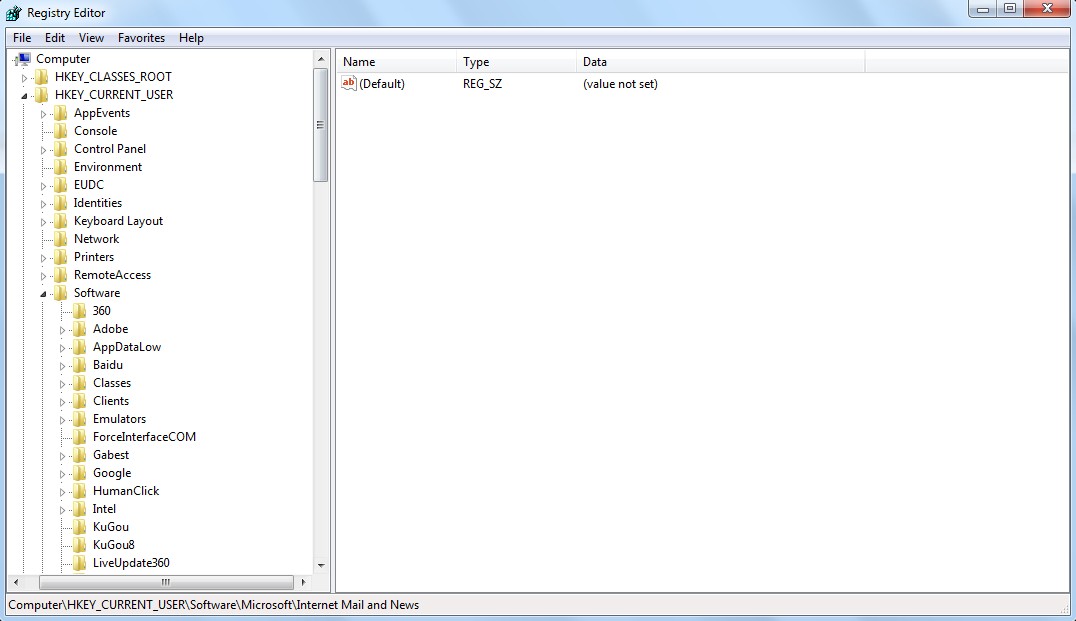
b. All malicious files and registry entries that should be deleted:
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%Temp%\random.exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion
4. Reboot the computer normally to take effective, when the above steps are done.
PC users need to realize that Exploit:Win32/Pdfjsc.AU can cause a great damage when it is installed to the infected machine, The cyber criminals may get into the infected PC via the backdoor process, which means the information on the whole infected computer will be in an extremely dangerous situation. Ignore the virus infection will cause great damage when the time goes by, Thus, it is strongly recommended PC remove this virus as soon as possible to keep the infected PC safe.
If you have no idea how to do with that, please to contact experts from Yoocare Online Tech Support for further help.
Published by & last updated on May 18, 2014 11:09 am



Leave a Reply
You must be logged in to post a comment.