Hi I’ve got a Trojan named Crypt_s.DEK Trojan in program files yesterday. My AVG found it, but can’t remove it. I have tried some tools to stop it and fix the problem, but unfortunately it could not kill it. Then I tried to use antivirus to erase it, still no luck. This virus came back. Have no way to remove it completely and I’ve been tired on trying everything to kill this nasty virus!!! How can I remove this virus completely without using tools?
Crypt_s.DEK Trojan Virus, like its name implies, is belong to the kind of Trojan horse virus. The way this stubborn virus gets in is usually bundling with some free software. These free software contains some deceptive files in its installation folder and many Trojan viruses have capacity of replacing its original icon to a very seductive file name and a similar double suffix such as TXT.EXE, JPG.EXE so as to achieve the aim of cheat users to run a Trojan. The name of the virus is using the characteristics of Windows operating system to mess up its real file attributes with the fake one. People would mistakenly judge it as a picture or a document and click the files. People are hard to detect its trait with the naked eye. If a hacker wants to control a computer, he must take the way of deception to trick victim users running the Trojan program. The hacker would take all kinds of action to accomplish camouflage process to make sure the Trojan virus has successfully implanted to the target system. The common way is to use anti-virus to do a system full scan. Anti-virus detection is rely on the feature code in Trojan virus, therefore, hackers often adopt the method of embedding legal code into the Trojan program to deceive anti-virus software, evade anti-virus software scan to guarantee Trojans are not killing by security programs.
Unlike the other computer virus, instead of focusing on the destruction of computer data, the role of the Trojan horse is spying on someone’s operation on the infected computer and is trying to steal the user information such as stealing passwords, account Numbers game, online stock accounts, online bank accounts, etc. In the past, the purpose of writing and spreading Trojan virus is to spy out other people’s privacy or pranks. Nowadays, Trojan horses have been commercialized aiming at useful information in the target machine in order to make actual benefit from victim users. Focusing on the filch files information, its working mechanism is able to go across physical barrier between internal and external network. Leaving such a big threat in your computer is not a wise choice; if you have noticed the trouble, remove it quickly to avoid financial loss.
1. It allows the virus makers to access your computer remotely without letting you know.
2. It is able to cause system crash and disable your executable programs.
3. It drops some other threats including malware, adware parasites and spyware into your computer.
4. It is capable of collecting your browsing history and other important data.
Crypt_s.DEK Trojan Virus is a malicious Trojan virus which can install itself into the computer system without your consent and awareness. It makes your computer work slowly and implants other nasty infections into the computer. To make things worse, this Trojan is a tool for the hacker to invade the infected computer to steal your information. It is recommended to remove it as quickly as possible. Users can follow the manual guide here to have it removed instantly.
1. Show Hidden Files
(1). Click on the Start button and then on Control Panel
(2). Click on the Appearance and Personalization link
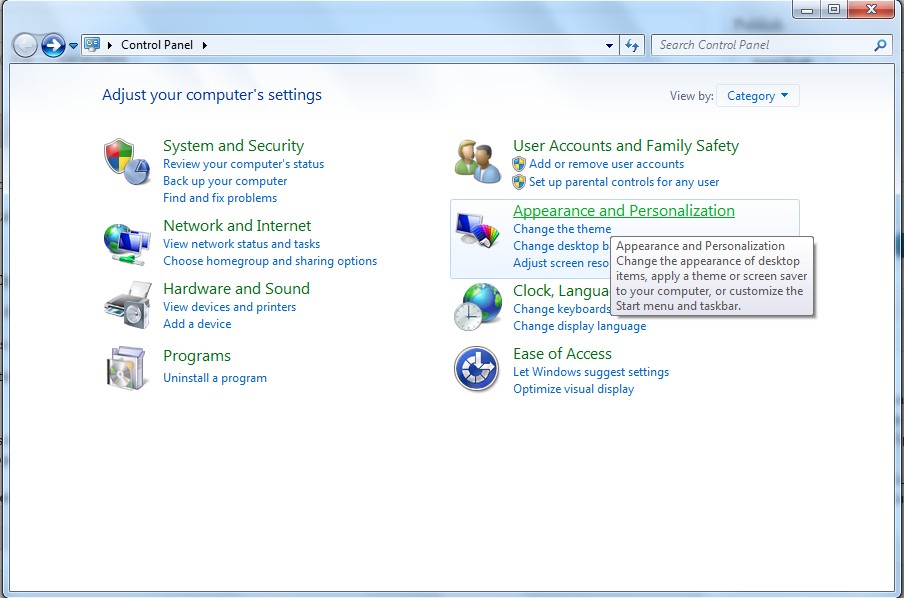
(3). Click on the Folder Options link
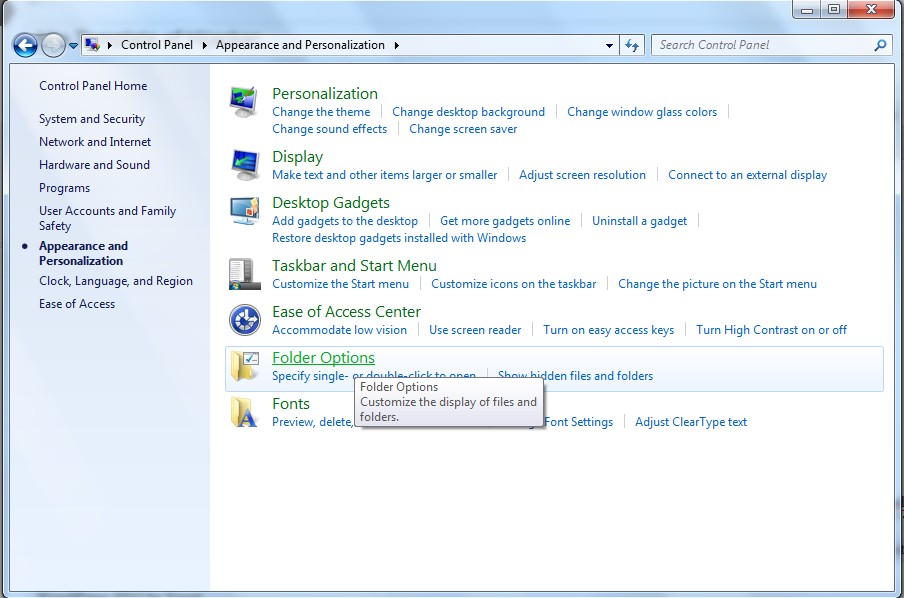
(4). Click on the View tab in the Folder Options window
(5). Choose the Show hidden files, folders, and drives under the Hidden files and folders category
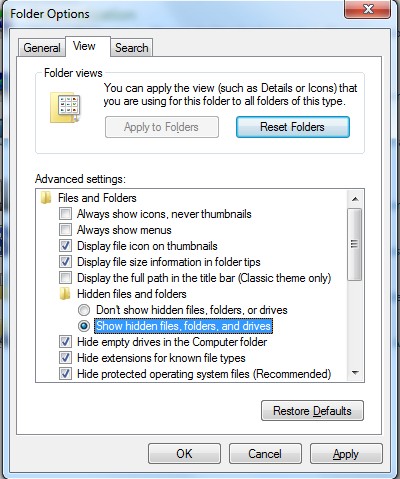
(6). Click OK at the bottom of the Folder Options window.
2. Delete Virus Files
(1). Delete the related registry entries through Registry Edit
Guides to open registry editor: Click “Start” menu, hit “Run”, then type “regedit”, click “OK”
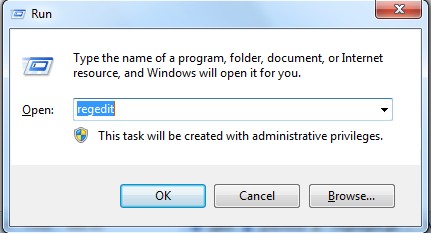
While the Registry Editor is open, search and delete the following registry entries listed below:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Random’
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
(2). Find out and remove the associated files of this browser hijacker virus.
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
%AllUsersProfile%\Application Data\~random
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
Crypt_s.DEK Trojan Virus is a highly dangerous virus to computer user.As we have mentioned above, Trojans are often seems to be harmless, but will perform some unexpected or unauthorized, and usually malicious action. The symptoms’ of Trojan infection are usually showing in the process of using the infected computer such as slow reaction, hard disk are reading and writing constantly, no response from mouse or keyboard and windows are suddenly closed without hints. Once the infection is done, its interference activity has started. Your computer settings will be secretly changed by the Trojan horse and you will be interrupted by lots of constant pop ups. Hiding behind system rootkit makes this virus more difficult to be removed. Manual way should be the most effective way to remove nasty virus.
If you don’t have much computer background knowledge and are not able to remove virus by the above instructions, please contact YooCare Expert for a fast and professional removal.
Published by on September 23, 2013 12:52 pm, last updated on September 23, 2013 12:52 pm



Leave a Reply
You must be logged in to post a comment.