Surfing on the Internet is really interesting and exciting. It has become a kind of life style for the modern society. You can shop what you want in the online malls, play video games together with people from different countries and communicate and make friends with people all over the world. You can do a lot more things with the Internet. But fun and convenience is just a side of it, it can also bring about problems and threats. The browser hijacking is one of the most popular and annoying problems. Everyday many new browser hijackers come up and many more computers get infected. It has become a critical issue to deal with. And to properly cope with it, we need to give answers to the following questions: What is a browser hijacker? What is the characteristic of a browser hijacker? What problems and harms a browser hijacker may cause for the computer users? How is the browser hijacker distributed?
A browser hijacker is an unwanted program that sneaks into a user’s computer and modifies the settings of the user’s web browsers such as Microsoft Edge, Google Chrome, Mozilla Firefox, or Internet Explorer and so on, without the user’s permission. A browser hijacker is able to affect computer systems ranging from a series of windows operating systems like Windows 2000, Windows 7, Windows 8, Windows 95, Windows 98, Windows Me, Windows NT, Windows Server 2003, Windows Server 2008, Windows Vista, Windows XP, Windows 8.1, and Windows 10 to the IOS of the Apple company and any other operating systems.
From reliable sources, we collect some names of special programs here as follow: Web-start.org, Tech-connect.biz, Yourconnectivity.net, Search.searchlwr.com, Webstarts.biz, 9o0gle.com, Startgo123.com, Mylucky123.com, Funnysiting.com, Securefindersearch.com, 1.loadblanks.ru. All these programs are classified into malicious browser hijackers because they all have the features and characteristics of a typical browser hijacker according to their descriptions. A typical browser hijacker usually works to change the existing homepage, search page, new tab page and error page into its own. In general, these are used to force hits to a particular website, increasing its advertising revenue. What is the most annoying is that anytime you try to visit a desired website, the browser hijacker will direct you to their own pages in a nasty way. A large amount of suspicious ads that advertise questionable services and products will pop up frequently. Sometimes you can’t even get control of your browser because of the browser hijacker. Some browser hijackers may also install spywares such as a kind of keylogger on your system to steal important information like banking and e-mail authentication details for illegal purposes. Some can also make a permanent damage to the registry on Windows systems.
Many browser Hijackers are included in the installer for another reliable program as “offers”. They are often provided without any documentation on what they do, or uninstall instructions that can be followed to remove them out of system by the users. In order to trick users into installing, they are normally presented in a confusing way. They are usually bundled with freewares, sharewares and ad-supported programs. Some browser hijackers spread around with the help of fake ads that tell about missing updates. When you are visiting a website and trying to play a video online, a message pops up and claims that your Java, Flash Player or FLV Player is out of date, and asks you to update to proceed, you should ignore it because there might be that it is just a way that used by unsafe programs to distribute themselves. Once such pop-up ads are clicked, a browser hijacker may right away successfully sneak into your computer.
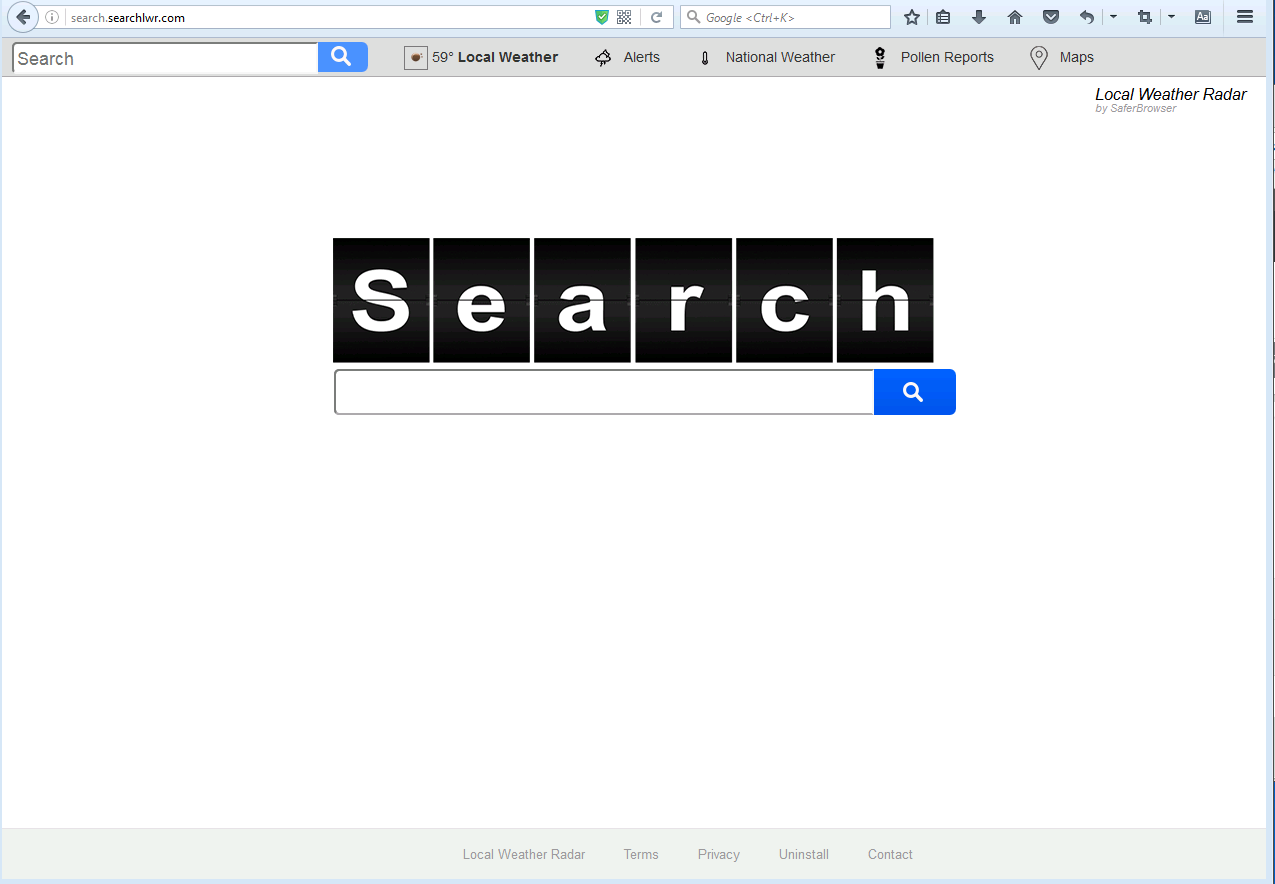
A browser hijacker hijacks your browsear to redirect your web search results and changes the homepage and browser settings. To completely uninstall it from an infected system, manual removal is the first choice because sometimes antivirus software cannot pick up the exact computer threat timely or remove it permanently. Now most browser hijackers are quite similar to spyware and adware threats and therefore cannot be removed with the help of popular antivirus products. Users can follow the manual guide here to get rid of this browser hijacker completely.
1. Clear all the cookies of your affected browsers.
Since this tricky hijacker virus is able to use cookies for tracing and tracking the internet activity of users, it is suggested users clean up all the cookies before a complete removal.
Google Chrome:
Click on the “Tools” menu and click the “Clear browsing data” button.
Select “Delete cookies and other site data” to delete all cookies from the list.
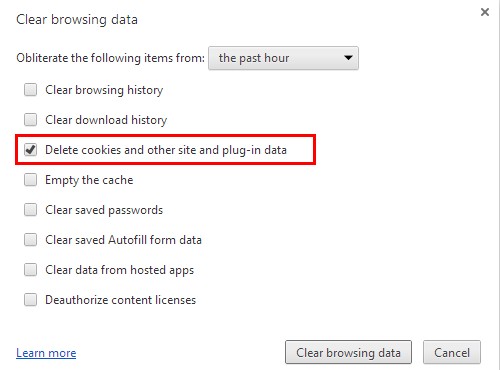
Internet Explorer:
Open Internet explorer window
Click the “Tools” button
Point to “safety” and then click “delete browsing history”
Tick the “cookies” box, then click “delete”
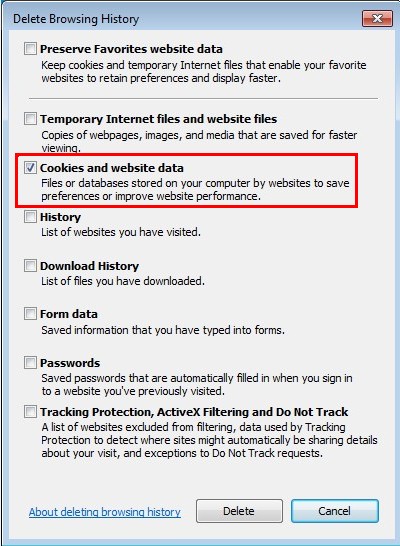
Mozilla Firefox:
Click on Tools, then Options, select Privacy
Click “Remove individual cookies”
In the Cookies panel, click on “Show Cookies”
To remove a single cookie click on the entry in the list and click on the “Remove Cookie”
To remove all cookies click on the “Remove All Cookies” button
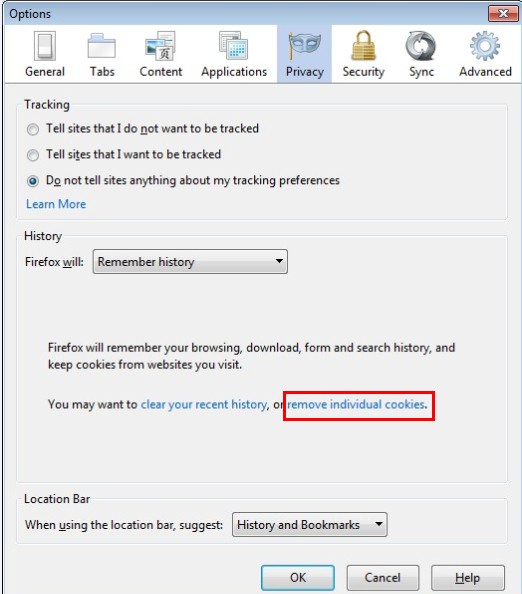
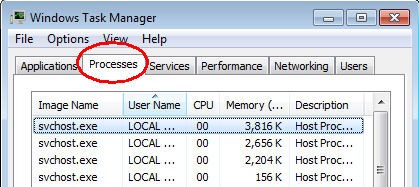
2. End the malicious process from Task Manager.
Once a browser hijacker is installed, computer user may notice that CPU usage randomly jumps to 100 percent. At any time Windows always has many running processes. A process is an individual task that the computer runs. In general, the more processes, the more work the computer has to do and the slower it will run. If your system’s CPU spike is constant and remain at a constant 90-95%, users should check from Task Manager and see if there is a suspicious process occupying the system resources and then end it immediately.
(The name of the virus process can be random.)
Press Ctrl+Shift+Esc to quickly bring up Task Manager Window:
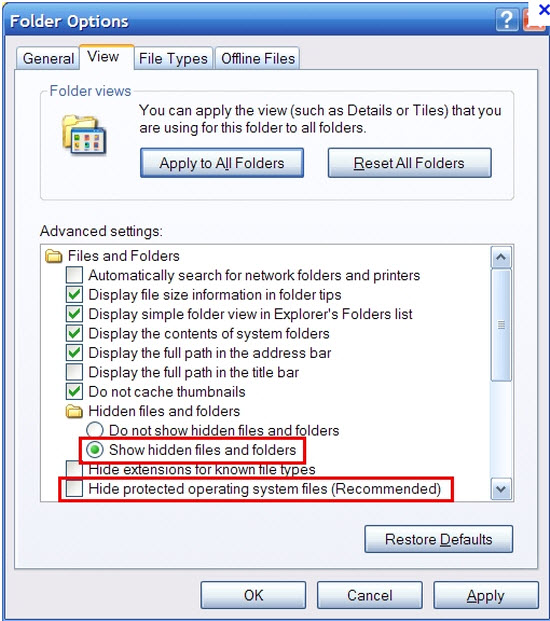
3. Show hidden files and folders.
Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
4. Delete all the malicious files related to the hijacker manually.
%AppData%Local[random].exe
C:\Documents and Settings\LocalService\Local Settings\Temporary Internet Files\*.exe
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main StartPage
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
A browser hijacker is a PUP that is able to affect all kinds of browsers and operating systems. It can cause the problems including changing the settings of your browser, directing you to a website you don’t desire in a nasty way, promoting questionable services and products by forwarding unlimited unwanted ads, installing spywares to monitor your activities without your permission and damaging your computer by making permanent changes to the registry on Windows system. So it is recommended to remove it out of your system as soon as possible when it is found in your computer. And to remove it completely, manual removal is strongly advised. You can turn to an expert who specializes in virus removal for help. Because an expert will be able to help you crack down on the hijacker without bringing in other problems caused by mistaken operation. To stay away from browser hijackers, you should take some time to study the distribution ways of a browser hijacker carefully. And I believe you will be well inspired and be able to protect your computer from being affected by most browser hijackers after the study.
Note: If you have little knowledge about computer and do not know how to operate the removal, please contact experts from YooCare Online Tech Support for further help.
Published by on October 29, 2016 11:13 pm, last updated on October 31, 2016 12:58 pm



Leave a Reply
You must be logged in to post a comment.