Norton detects the Heuristic.BehavesLike.Win32.Suspicious.H virus in your computer and says it is removed but it appears on the scan result again and again after you restart the computer? Is there a good method to remove the Trojan virus? Will steal your personal information if you do not delete it?
Heuristic.BehavesLike.Win32.Suspicious.H is classified as a Trojan virus that is specially designed and released by cyber criminals to help them gather valuable information. Different from some other normal Trojan viruses, it can circumvent many antivirus programs to install itself on the computer without letting you know. It is not a malicious software or a ransomware that shows up on the computer screen. It hides in the system once it has the opportunity to enter the computer. Trojan viruses are all good at making use of system vulnerabilities which are usually caused by the computer users.
As mentioned before, the Heuristic.BehavesLike.Win32.Suspicious.H virus can bypass the majority of antivirus tools. Usually, it is hidden in some phishing web sites, unknown “free” programs and spam email attachments. It can infect your computer if you access to those unsafe resources when you surf the Internet. Once it is in the computer, the antivirus program is able to detect it and show you security alarms if you keep updating the antivirus program. But, when you try to use your antivirus program to delete it, it does not seem to be removed completely from the computer. What is worse, if you do not have the virus removed as soon as possible, it will help the virus makers to gather your personal info.
1. It has the ability to download additional components and other infections in the target computer in order to fully complete its penetration.
2. It is able to cause system crash and destroy some of your programs in the infected computer.
3. It facilitates the virus makers to intrude your computer remotely without letting you know.
4. It is capable of collecting your browsing history and other private data.
The virus can help computer hackers to collect valuable information from personal computer users and implant malware or spyware into the computer, which may further damage your computer. Therefore, it is recommended that you should delete it timely. In order to completely eliminate this Trojan virus, manual removal is the most effective way.
1. End Relevant Processes
(1). Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab
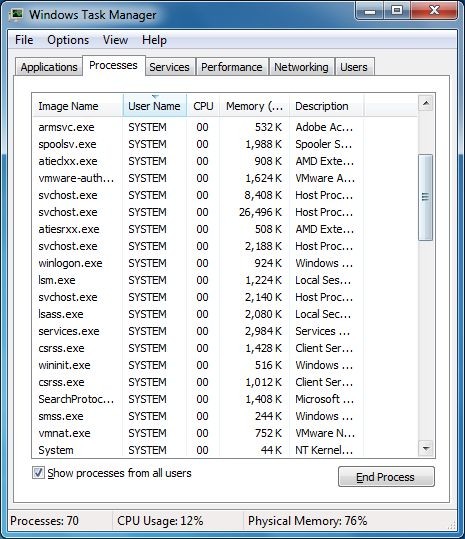
*For Win 8 Users:
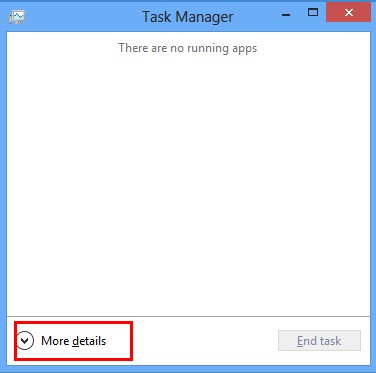
Click More details when you see the Task Manager box
And then click Details tab
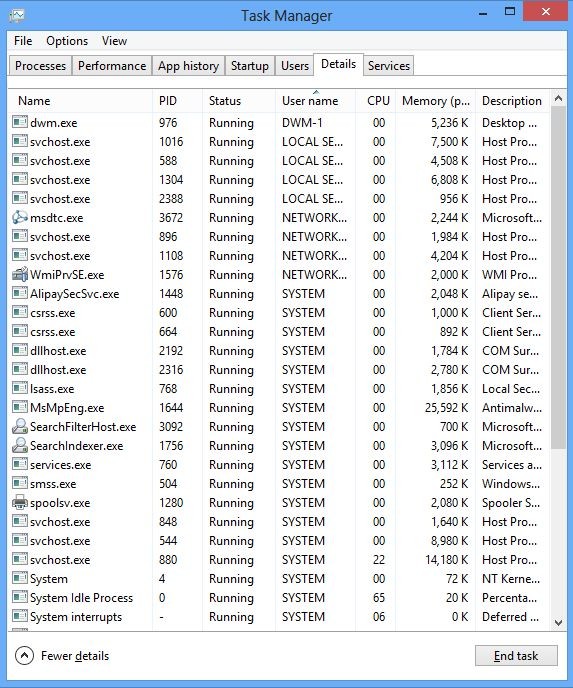
(2). Find out and end the processes of Heuristic.BehavesLike.Win32.Suspicious.H
2. Show Hidden Files
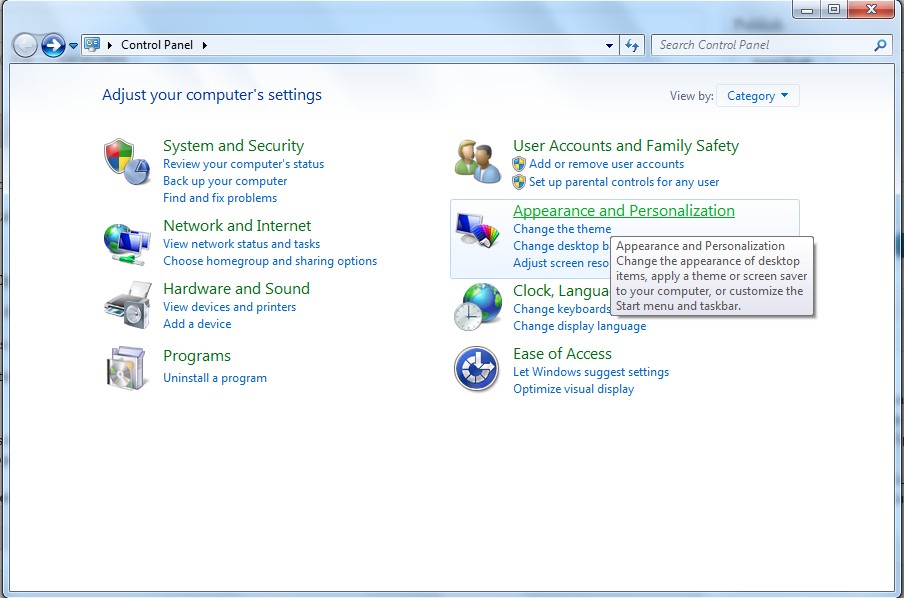
(1). Click on Start button and then on Control Panel
(2). Click on Appearance and Personalization
(3). Click on Folder Options
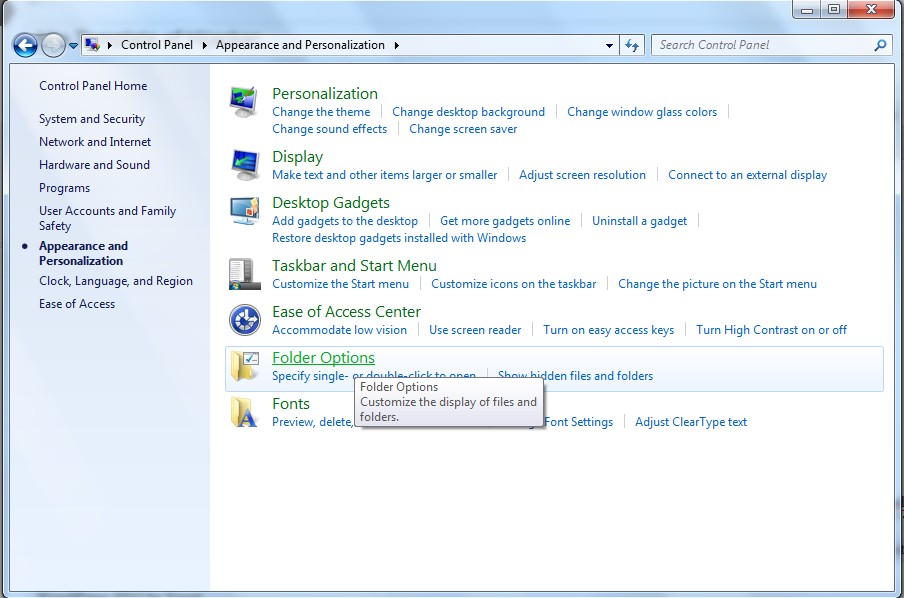
(4). Click on the View tab in the Folder Options window
(5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
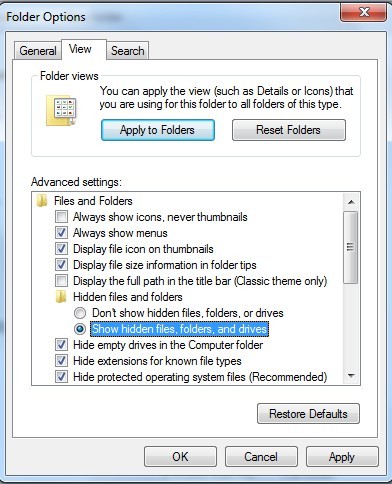
(6). Click OK at the bottom of the Folder Options window
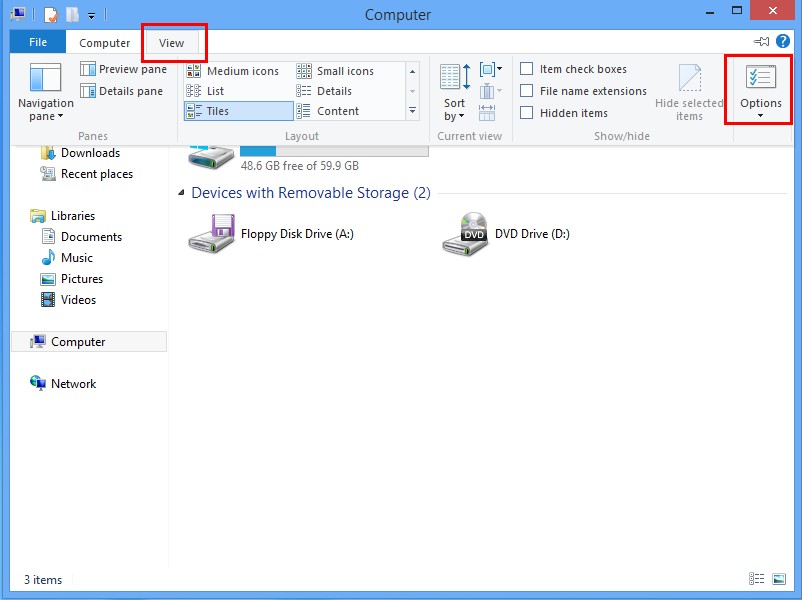
*For Win 8 Users:
Press Win+E together to open Computer window, click View and then click Options
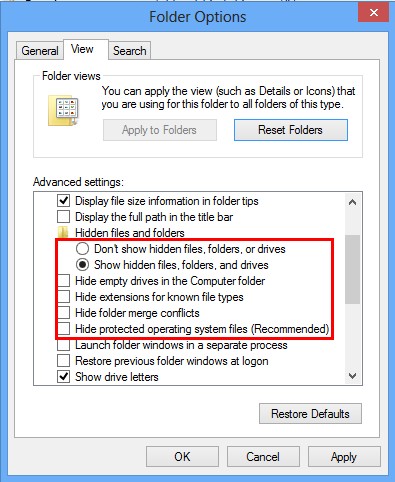
Click View tab in the Folder Options window, choose Show hidden files, folders, and drives under the Hidden files and folders category
3. Delete Relevant Registry Entries and Files
(1). Delete the registry entries of Heuristic.BehavesLike.Win32.Suspicious.H through Registry Editor
Press Win+R to bring up the Run window, type “regedit” and click “OK”
While the Registry Editor is open, search and delete the related registry entries
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Random’
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
(2). Find out and remove the associated files
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
%AllUsersProfile%\Application Data\~random
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
Trojan viruses are very active in the Internet world. They have been to many places, because for most people, the computer has become very important and now the network is developed. Through various communication networks, Heuristic.BehavesLike.Win32.Suspicious.H has its specific target groups – some inexperienced computer users who lack of safety awareness. We should not touch unsafe or unknown resources online if we want to stay away from this dangerous thing. It is able to gain unauthorized access to the target computer. It will bring a lot of troubles to harass you. For example, you will encounter more and more malicious programs in the computer and keep being redirected to some other unwanted web sites when you surf the web. The network connection is often cut off. The system itself may follow the commands of this Trojan to reboot or shut down randomly. In conclusion, the virus should be removed as soon as possible if you do not want to experience any of the above results and lose your data.
The above manual removal is quite dangerous and complicated, which needs sufficient professional skills. Therefore, only computer users with rich computer knowledge are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by on December 30, 2014 3:26 am, last updated on December 30, 2014 3:26 am



Leave a Reply
You must be logged in to post a comment.