Hello, how are you? How does this Generic Suspicious attack my computer? My AVG informs me about this malicious virus but can’t deal with it. Why the virus is so stubborn? As a matter of fact, it makes my computer suffer from poor performance. I am struggling to remove it step by step. But I don’t know where I should start first. This is the reason why I am here for searching a solution. If there is anyone who can help out of this problem, I will be so appreciated.
Generic Suspicious is categorized as a vicious Trojan horse which can bring series of abnormal actions to the system. It will change your system settings as its wishes so that it is impossible for you to get the intended search results. It pretends to be legit program, claiming to help you save time and money. And while you go online, it will force you to enter hacker web sites full of numerous popup ads about real time product images. Its goal is to generate profit from promoting products from multiple top rated price comparison stores. Due to the virus, boot sector gets damage and you find some application functioning slowly when you try to open some normal programs. What is worse, it can generate many unwanted files to the system consuming system space greatly as it usually runs as a background program.
Generic Suspicious is able to get installed in the computer via several deceptive techniques. Actually if you visit a malicious website, click on unwanted ads and download some questionable software without any caution, the Trojan would slip into your computer secretly. It can drain all your vital personal data including passwords, user account number and etc by spying your browser history and then transfer them to the third party for illegal use. With your computer victimized, the virus can transfer some arbitrary files from sponsored server and execute them immorally. It will inject its infectious element to the Windows Start up section to help it run automatically whenever the system starts up. It shows alerts message claiming threats is detected in your computer and says that if you want to remove the threats, you need to purchase a program. Don’t be cheated by it. If you want to protect your computer, it has to be executed immediately.
Generic Suspicious allows cyber-criminals to break into the infected computer without being noticed and it could disable executable programs installed on your computer and cause system crash. Also it will change important settings on your computer to allow remote control from cyber criminals. Other than that, it will modify your registry settings and important key value to make it difficult to be removed.
Manual removal is suggested here if the antivirus program in your computer can’t deal with it. The most guaranteed way to get rid of the trojan without reinstalling the system or formatting the hard disk is manual removal. Here are some basic steps to achieve this point. However, removing the virus manually requires high skills in order to determine which files to delete for the Trojan infection is changing with the passage of time. You are also suggested to do a backup before starting.
1. End Relevant Processes
(1). Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab
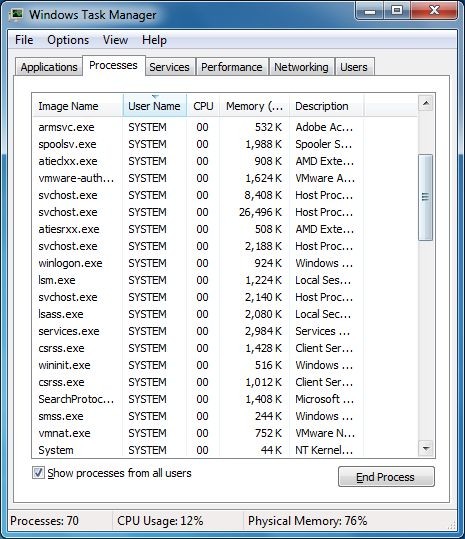
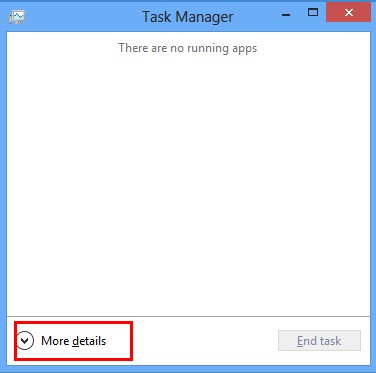
*For Win 8 Users:
Click More details when you see the Task Manager box
And then click Details tab
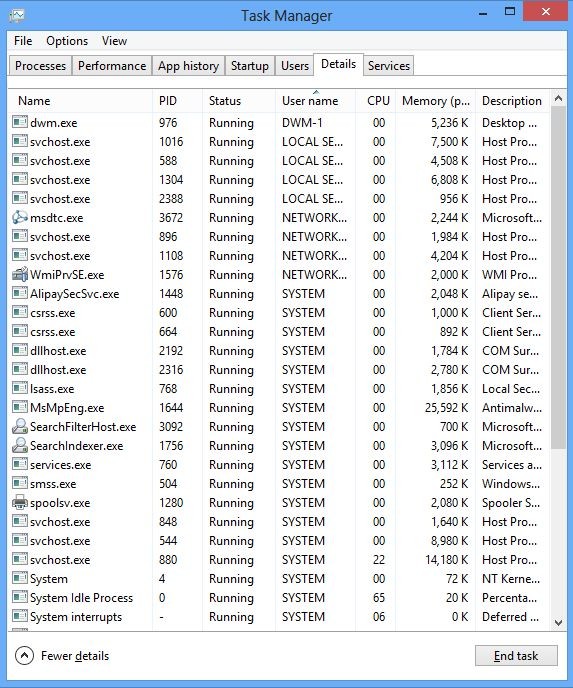
(2). Find out and end the processes of Generic Suspicious
2. Show Hidden Files
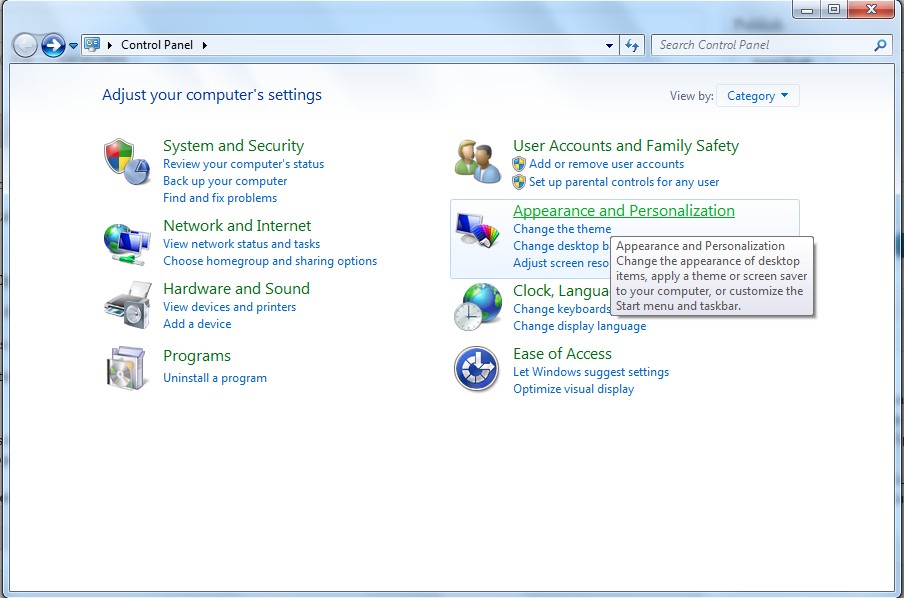
(1). Click on Start button and then on Control Panel
(2). Click on Appearance and Personalization
(3). Click on Folder Options
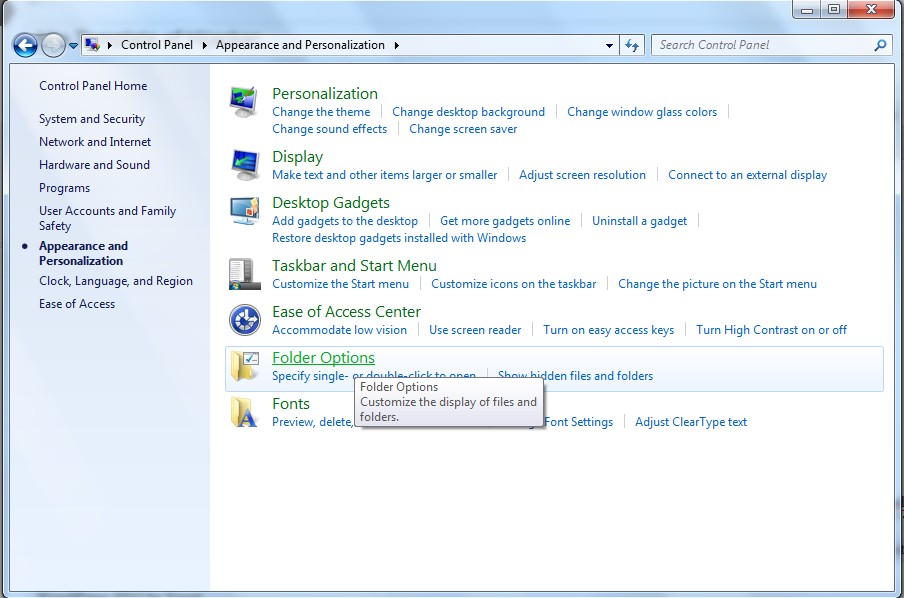
(4). Click on the View tab in the Folder Options window
(5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
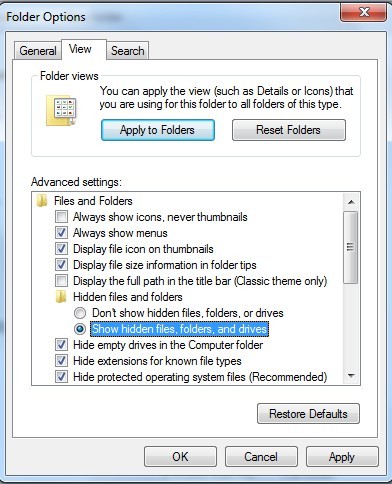
(6). Click OK at the bottom of the Folder Options window
*For Win 8 Users:
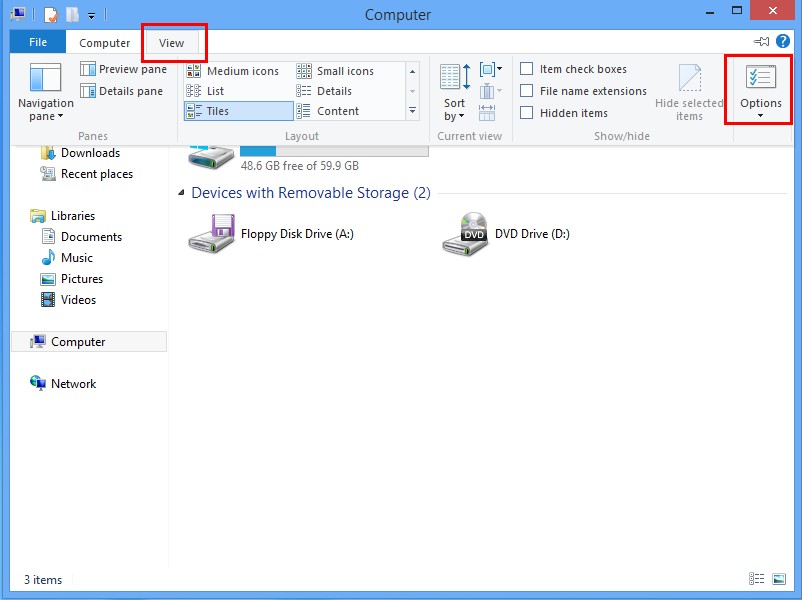
Press Win+E together to open Computer window, click View and then click Options
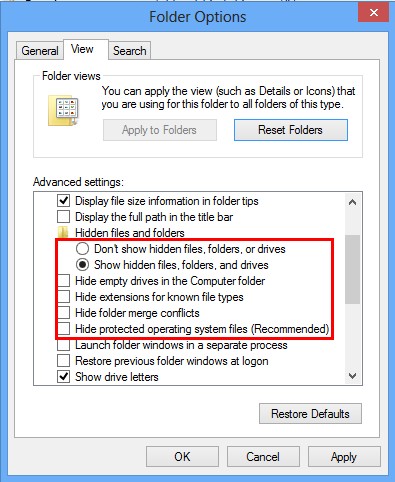
Click View tab in the Folder Options window, choose Show hidden files, folders, and drives under the Hidden files and folders category
3. Delete Relevant Registry Entries and Files
(1). Delete the registry entries of Generic Suspicious through Registry Editor
Press Win+R to bring up the Run window, type “regedit” and click “OK”
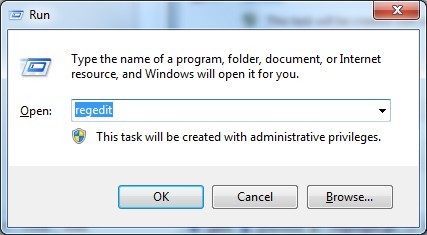
While the Registry Editor is open, search and delete the related registry entries
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[RANDOM CHARACTERS].exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run ‘Random’
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Random
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “CertificateRevocation” =Random
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\run\Random.exe
(2). Find out and remove the associated files
%AllUsersProfile%\random.exe
%AppData%\Roaming\Microsoft\Windows\Templates\random.exe
%Temp%\random.exe
%AllUsersProfile%\Application Data\random
%AllUsersProfile%\Application Data\~random
%AllUsersProfile%\Application Data\.dll HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Random “.exe”
Generic Suspicious opens a backdoor for the hackers to take control of the computer remotely for misuse. If you don’t get rid of this virus in time, it will do lots of malicious action on your computer. It is able to replicate and spread itself easily thus damaging the system severely. And it is able to infiltrate other risky infections to further consolidate its survival and take better control of your computer. As a result, such unexpected symptoms may occur like system crash, blue screen errors and other serious problems. If your computer has already been infected by it, you should take manual measures to remove it without any delay.
The above manual removal is quiet complicated, which needs sufficient professional skills to process. Therefore, only computer users with sufficient computer skills are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by on December 16, 2014 10:53 pm, last updated on December 16, 2014 10:55 pm



Leave a Reply
You must be logged in to post a comment.