not-a-virus:AdWare.Win32.Lyckriks.cv is composed of a bunch of malicious codes and has the ability to mutate constantly, therefore, antivirus programs can detect this threat but always cannot delete it. You try to use a variety of removal tools but still fail to get rid of it and also make your computer in a mess finally? Do you know something about it? We should have a better understanding of this malicious thing before we take actions to remove it.
not-a-virus:AdWare.Win32.Lyckriks.cv is a dangerous threat that has attacked many computers all over the world so far. It is build by those tricky but clever cyber criminals with advanced computer technology. Therefore, it is able to avoid a variety of antivirus programs. It is usually connected to junk e-mail attachments and malicious websites. Also, when you download some free software from an unknown resource, it is likely to have access to your computer. You may not know it is in the computer until you see a warning from the antivirus.
When not-a-virus:AdWare.Win32.Lyckriks.cv get the chance to station in your computer successfully, it occupies a lot of spaces to reduce the overall CPU performance of your computer. It is capable of modifying the startup registry keys and injecting their sneaky codes in the system, which makes it run automatically right after computer starting up every time. Worms or Trojan viruses will be transferred to the infected computer by this threat constantly to cause more serious damages to the computer. The most frightening thing is that it can open a backdoor for cyber criminals to take control of the computer as well as gain access to your confidential information secretly. You know, letting the bad guys know about your personal information is a very terrible thing. Notably, the threat is like a time bomb that can cause maximum damages to the target computer at any moment. Once you know it is in your computer, you should remove it completely to ensure the security of your system files and prevent further losses. As the victims of the threat, most people tend to use their own trusted antivirus programs to scan the infected computer. However, all efforts will be in vain. You still see it appearing again and again. In this case, to stop its malicious behaviors in the computer, you can consider a more efficient way – manual removal.
1. It has the ability to download additional components and other infections in the target computer in order to fully complete its penetration.
2. It is able to cause system crash and destroy some of your programs in the infected computer.
3. It facilitates the virus makers to intrude your computer remotely without letting you know.
4. It is capable of collecting your browsing history and other private data.
The malicious thing can install itself into the computer system without your consent and awareness. It makes your computer work slowly and implants other nasty infections into the computer. To make things worse, this Trojan is a tool for the cyber criminals to invade the infected computer to steal your information. Through making use of advanced technology, it maintains the ability to combine its components with system files or to generate fake system files, which confuses computer users as well as antivirus programs. They cannot identify it accurately and timely, let alone remove it thoroughly. Therefore, manual removal is the best choice to drive it away from your computer. In this case, you are advised to delete every file generated by it manually so as to spare all later trouble. The manual removal needs to be handled carefully so as to avoid any subsequent damages. Users can follow the manual guide here to have the hijacker removed instantly.
1. End Relevant Processes
(1). Press Ctrl+Shift+Esc together to pop up Windows Task Manager, click Processes tab
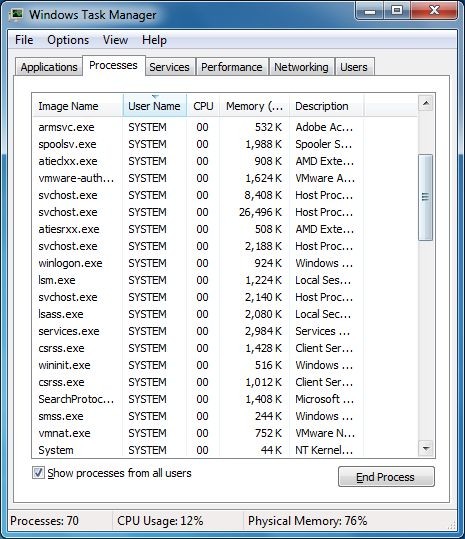
*For Win 8 Users:
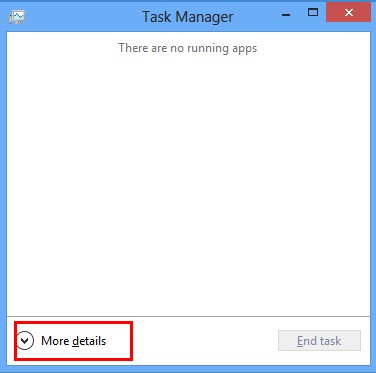
Click More details when you see the Task Manager box
And then click Details tab
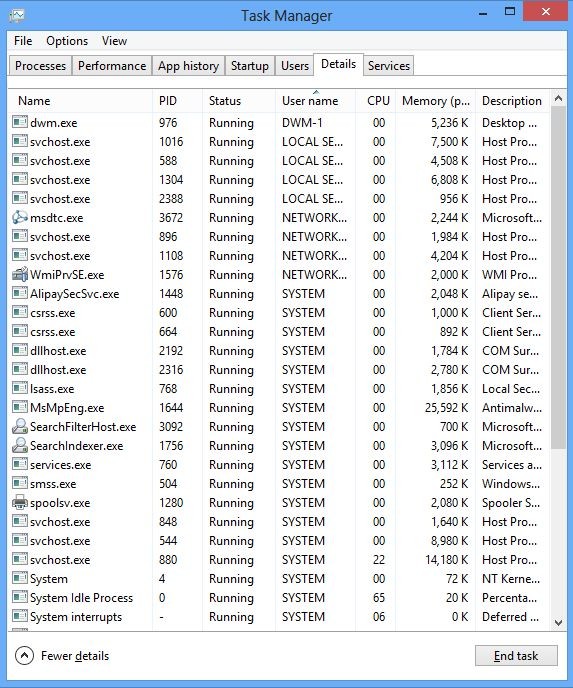
(2). Find out and end its processes
2. Show Hidden Files
(1). Click on Start button and then on Control Panel
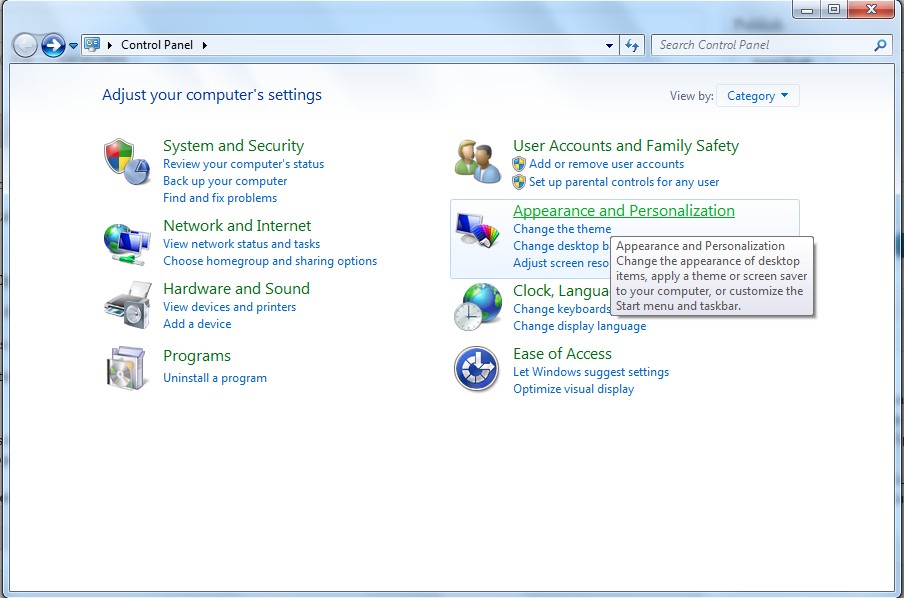
(2). Click on Appearance and Personalization
(3). Click on Folder Options
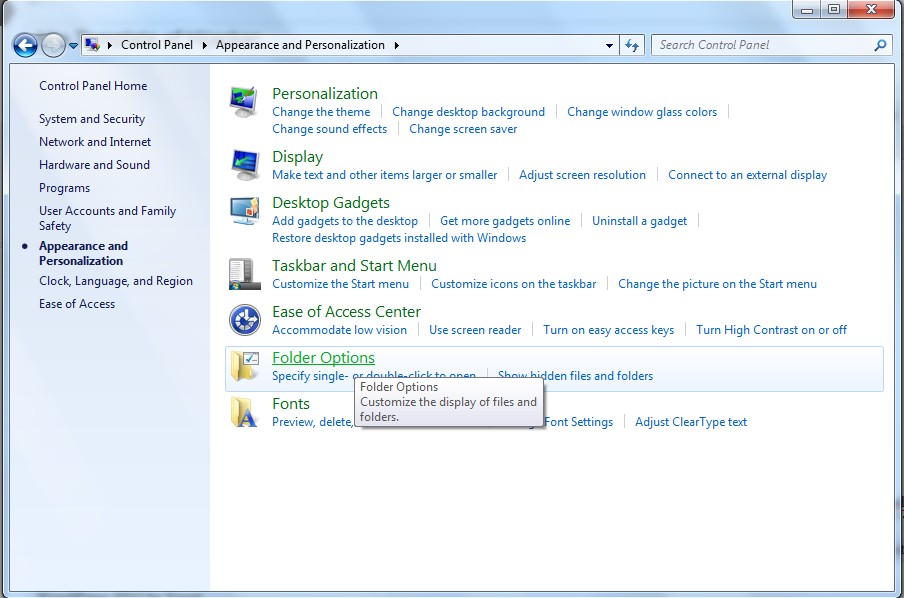
(4). Click on the View tab in the Folder Options window
(5). Choose Show hidden files, folders, and drives under the Hidden files and folders category
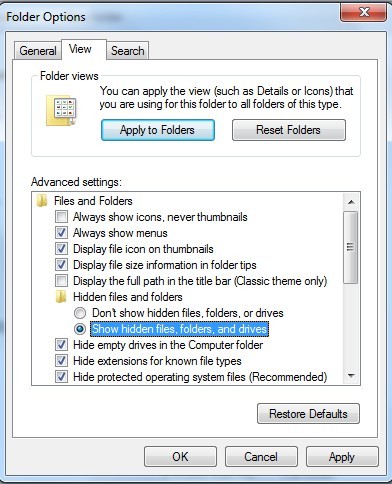
(6). Click OK at the bottom of the Folder Options window
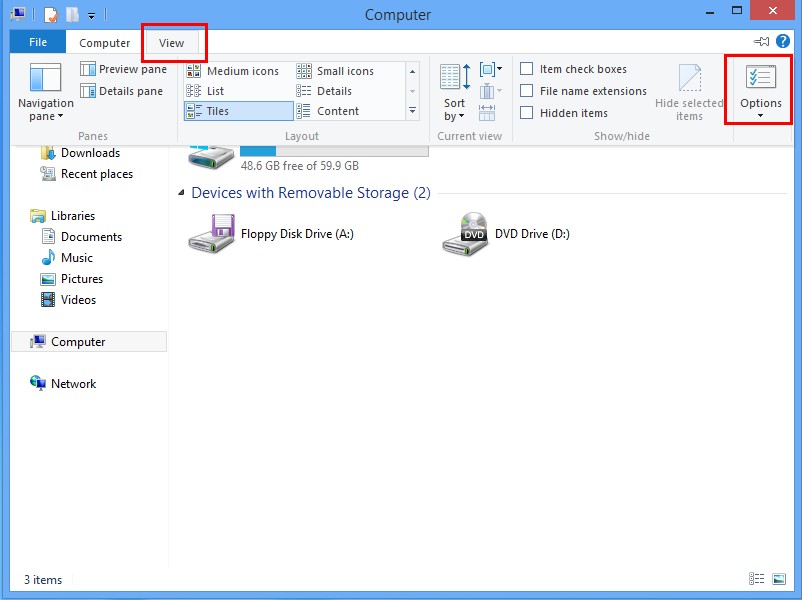
*For Win 8 Users:
Press Win+E together to open Computer window, click View and then click Options
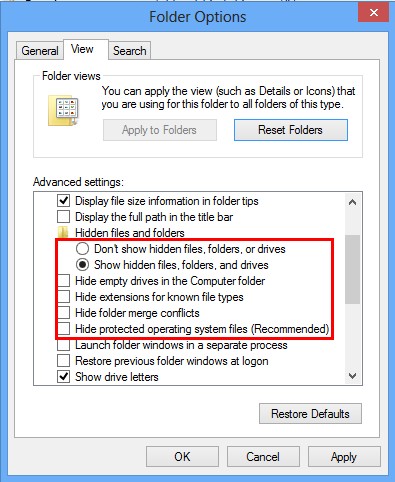
Click View tab in the Folder Options window, choose Show hidden files, folders, and drives under the Hidden files and folders category
3. Delete Relevant Registry Entries and Files
(1). Delete the virus registry entries through Registry Editor
Press Win+R to bring up the Run window, type “regedit” and click “OK”
While the Registry Editor is open, search and delete the related registry entries
(2). Find out and remove the associated files
not-a-virus:AdWare.Win32.Lyckriks.cv is a rampant malicious program. Installing some free programs, opening spam e-mail attachments and clicking on unknown links are to invite it to break into your computer. Some phishing sites force you to install plug-ins which are bundled with it. If you do not remove it promptly, it will bring some of the other malicious software or spyware to your computer, as a result, cyber criminals can break into the infected computer. Please note that your sensitive information, such as bank account passwords and confidential documents, may be used by an unknown third party. Some antivirus programs will pop up a warning window to remind you that your computer is infected with it, but unfortunately, they cannot eliminate it. Thus, you can try manual removal.
The above manual removal is quite dangerous and complicated, which needs sufficient professional skills. Therefore, only computer users with rich computer knowledge are recommended to implement the process because any errors including deleting important system files and registry entries will crash your computer system. If you have no idea of how to process the manual removal, please contact experts from YooCare Online Tech Support for further assistance.
Published by on March 4, 2014 4:03 am, last updated on March 4, 2014 4:03 am



Leave a Reply
You must be logged in to post a comment.