Trojan:Win32/Alureon.EP is a newly-released Trojan parasite which can disguise itself on the affected machine by attaching its own code to original Windows system files so that it is hard to be uninstalled. It is suggested users can follow the manual guide below to clean it up for good.
Trojan:Win32/Alureon.EP is a highly dangerous Trojan that can proliferate through malicious websites, spam email messages, unsafe downloads. Once it is downloaded, it drops several junk files on local drive particularly under System folder of Windows. Thus, it makes the removal rather difficult. Undoubtedly, the threat contains Backdoor capability which opens a backdoor to gather confidential information, such as credit card data, the victim’s log credentials and many other and transfers the stolen data to remote cyber criminals who use it for further harmful activities.
Besides the damages mentioned above, Trojan:Win32/Alureon.EP still has many bad actions. It decreases overall PC performance and results in Internet connection issues. This threat can compromise your system and may introduce additional infections such as Metropolitan Police virus and FBI Antipiracy Warning virus etc. to your computer. You may even experience system crash and computer freeze problems occur randomly. In a word, the longer this Trojan stays, the more damages it can bring. To process the clean up of removal of this virus, follow the instructions on this page.
a. There will be lots of annoying pop-up ads and fake security alerts;
b. It will block your access to the Internet and redirect everything you do on your browser to malicious web pages;
c. It will reduce your PC performance and create many junk files to wreak chaos;
d. Antivirus programs on the computer will automatically be shut down;
e. It may come with additional viruses and malwares to further damage your computer;
f. Your private and critical information may be captured a remote host who will use them in Internet crimes.
Currently many computer users had the same experience that this virus couldn’t be removed by any anti-virus applications. So the manual approach is always required to combat this virus. And here is the step-by-step removal guide for all computer users.
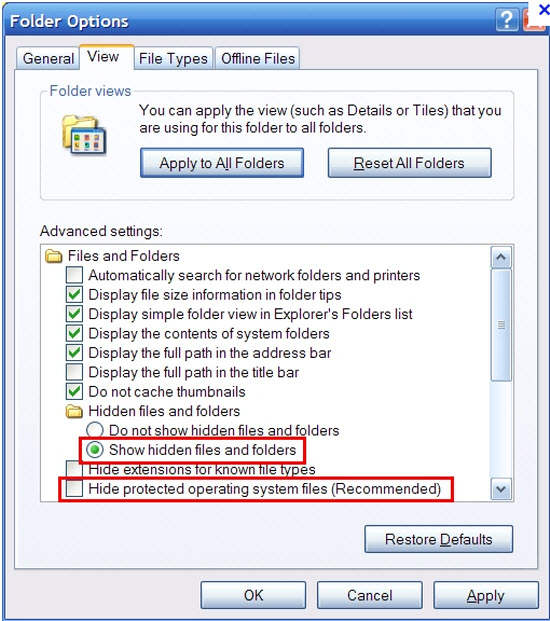
1. Show hidden files and folders.
Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
2. Open Registry entries. Find out the malicious files and entries and then delete all.
Attention: Always be sure to back up your PC before making any changes.
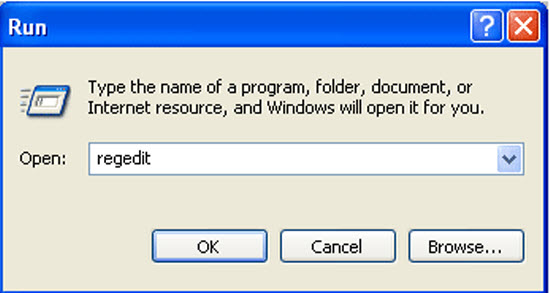
a. Press the “Start” button and then choose the option “Run”. In the “Open” field, type “regedit” and click the “OK” button.
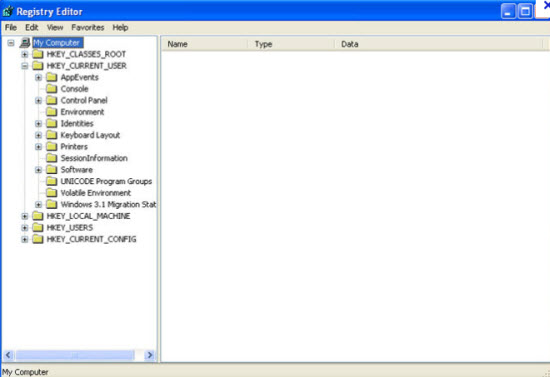
b. All malicious files and registry entries that should be deleted:
%AllUsersProfile%\Application Data\.dll
%AllUsersProfile%\Application Data\.exe(random)
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “[RANDOM]”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “[RANDOM].exe”
Trojan:Win32/Alureon.EP is classified as a harmful Trojan virus that disturbs users continuously. It can infect a computer through many ways. Users always get this virus installed while they’re clicking some malicious ads or visiting some malicious sites, as well as opening unknown downloaded files. If you have these activities online, then there may be a reason that you have this Trojan on your computer. Every PC user should know clearly how to prevent this virus from infecting again. Once the virus completely is removed, users should be aware of unexpected or unsolicited email attachments. At the same time, update your anti-virus program regularly. You also need to avoid forwarding email attachments unless you first scan the attachment for viruses. It is suggested users to get rid of this vicious virus as soon as possible.
Published by on September 13, 2012 2:47 am, last updated on May 28, 2013 8:45 am



Leave a Reply
You must be logged in to post a comment.