Have you heard of Rootkit.Boot.SST.b virus? It is associated with File Recovery Virus, SMART HDD Virus which can make all your icons disappeared, leaving you a black screen with empty start menu. Once detected, an immediate removal is needed.
Rootkit.Boot.SST.b is a highly dangerous virus that always drops malicious files and modifies the registry in an attempt to harm your machine. This Trojan has combined with rogue programs such as System Restore, System Fix. File Recovery, Smart Check or Smart HDD. It can easily enter any PC system via security exploits and flaws. When this virus is installed, it will mess up the whole system, making users upset.
This virus can hide itself in the deep of an infected computer. It is generally used for collecting passwords, credit card numbers, usernames and other personal data, and then transferring to the remote hacker. When you detect the virus, you will also have other rogue programs installed which will scan your computer automatically, generating a fake report telling your hard drive is about to fail and you have many system errors. Users should not be taken in that. This malware also makes PC slow dramatically. It compromises your personal information and privacy that must be removed without a doubt.
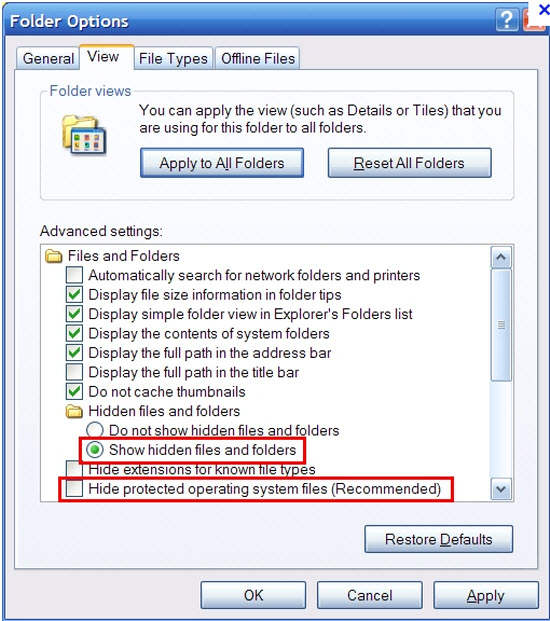
1. Show hidden files and folders.
Open Folder Options by clicking the Start button, clicking Control Panel, clicking Appearance and Personalization, and then clicking Folder Options.
Click the View tab.
Under Advanced settings, click Show hidden files and folders, uncheck Hide protected operating system files (Recommended) and then click OK.
2. Open Registry entries. Find out the malicious files and entries and then delete all.
Attention: Always be sure to back up your PC before making any changes.
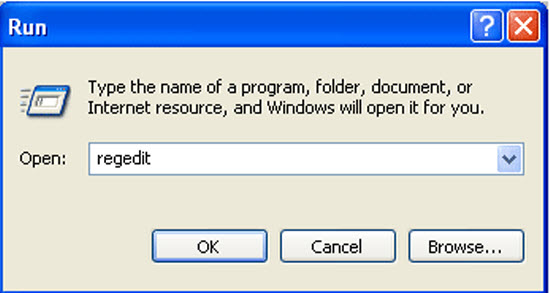
a. Press the “Start” button and then choose the option “Run”. In the “Open” field, type “regedit” and click the “OK” button.
b. All malicious files and registry entries that should be deleted:
%AllUsersProfile%\Application Data\.exe
%UserProfile%\Desktop\
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings “net
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run “[random].exe”
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell
If you failed to remove this malware with the instructions above or need any assistant, you are welcome to contact YooCare experts to resolve all the problems completely.
Published by on July 19, 2012 2:55 am, last updated on July 19, 2012 2:56 am



Leave a Reply
You must be logged in to post a comment.